FPGA realization of speech encryption based on modified chaotic logistic map
This paper presents an FPGA design and implementation of a chaotic speech encryption and decryption system based on bit permutations. Different encryption schemes are realized and compared. In addition, various testing methods including entropy, mean squared error, and correlation coefficients are used to analyze the efficiency of the system. The techniques for area and delay minimization are used. Carry look-ahead adder, multi-operand adder and booth multiplier are used to improve the performance of the encryption schemes design. A comparison between the different encryption architectures and

Guest editorial mission critical networking
[No abstract available]
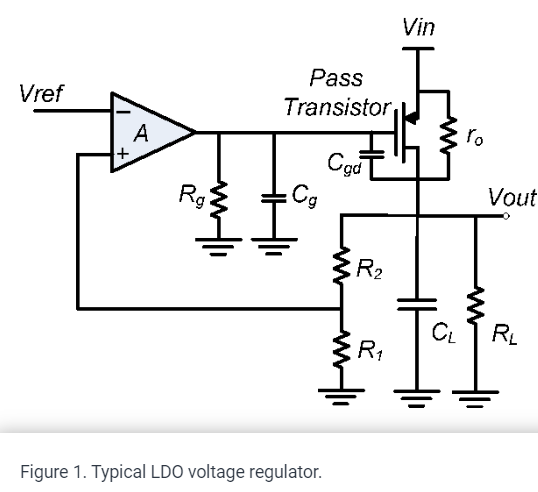
Parallel feedback compensation for LDO voltage regulators
A novel low dropout (LDO) voltage regulator compensation technique is demonstrated. A parallel feedback path is used to insert a zero at approximately three times the output pole. The parallel feedback consists of passive elements only and occupies small area. The proposed technique completely eliminates the output pole at different load conditions and results in high LDO bandwidth, which achieves fast output tracking of the input reference and fast recovery of sudden load changes. Moreover, the output pole elimination at different load conditions enables the potential scaling of the error
Multi-phase oscillator for higher-order PSK applications
Multi-phase oscillator is an essential block in digital communication systems especially phase shift keying PSK based systems. In this paper, a procedure for designing a multi-phase oscillator with any required phase shift is proposed, unlike the previous oscillator which generates equal phase shifts. This oscillator circuit is built using fractional-order elements to generate any distribution of phase shift. The general characteristics equation is studied where the condition for oscillation and oscillation frequency are derived. Finally, different examples are introduced with their
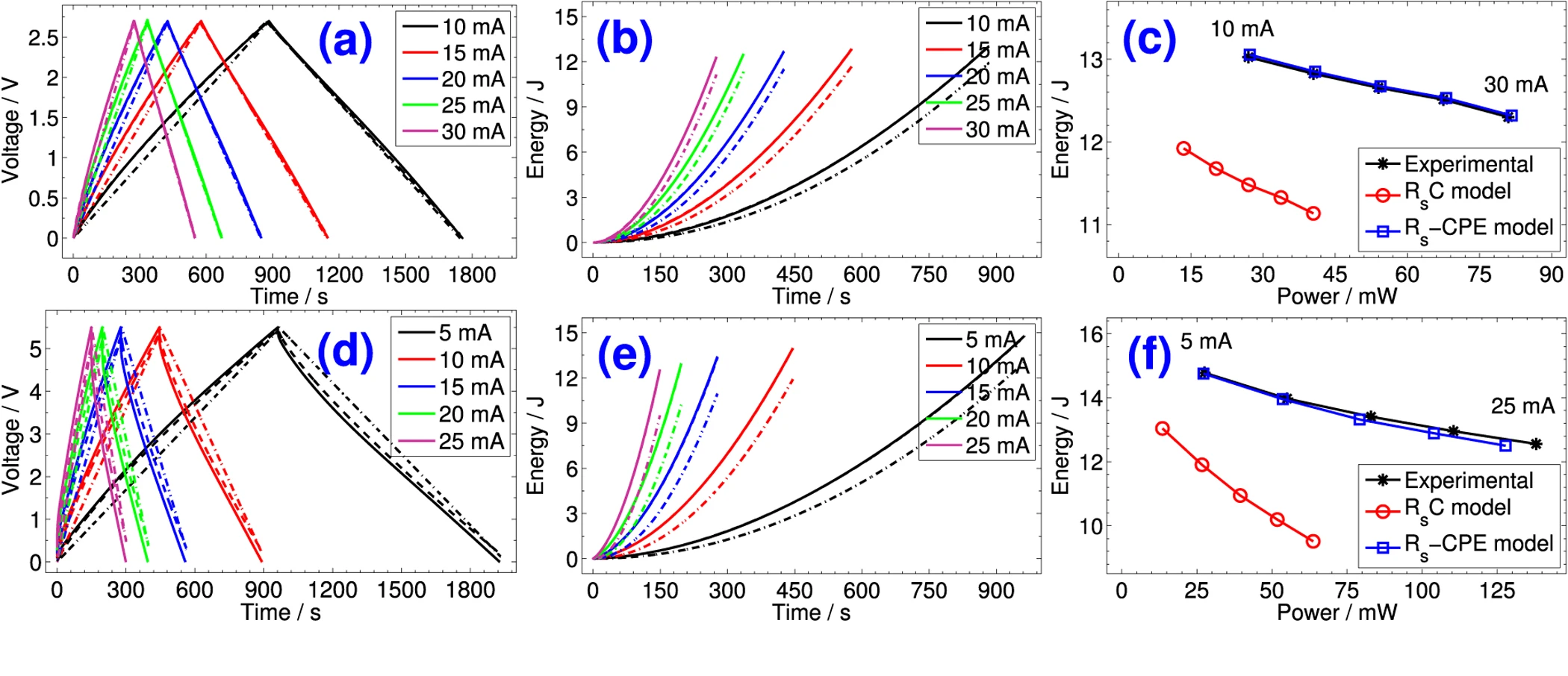
Reevaluation of Performance of Electric Double-layer Capacitors from Constant-current Charge/Discharge and Cyclic Voltammetry
The electric characteristics of electric-double layer capacitors (EDLCs) are determined by their capacitance which is usually measured in the time domain from constant-current charging/discharging and cyclic voltammetry tests, and from the frequency domain using nonlinear least-squares fitting of spectral impedance. The time-voltage and current-voltage profiles from the first two techniques are commonly treated by assuming ideal S s C behavior in spite of the nonlinear response of the device, which in turn provides inaccurate values for its characteristic metrics. In this paper we revisit the
Finite precision logistic map between computational efficiency and accuracy with encryption applications
Chaotic systems appear in many applications such as pseudo-random number generation, text encryption, and secure image transfer. Numerical solutions of these systems using digital software or hardware inevitably deviate from the expected analytical solutions. Chaotic orbits produced using finite precision systems do not exhibit the infinite period expected under the assumptions of infinite simulation time and precision. In this paper, digital implementation of the generalized logisticmap with signed parameter is considered. We present a fixed-point hardware realization of a Pseudo-Random
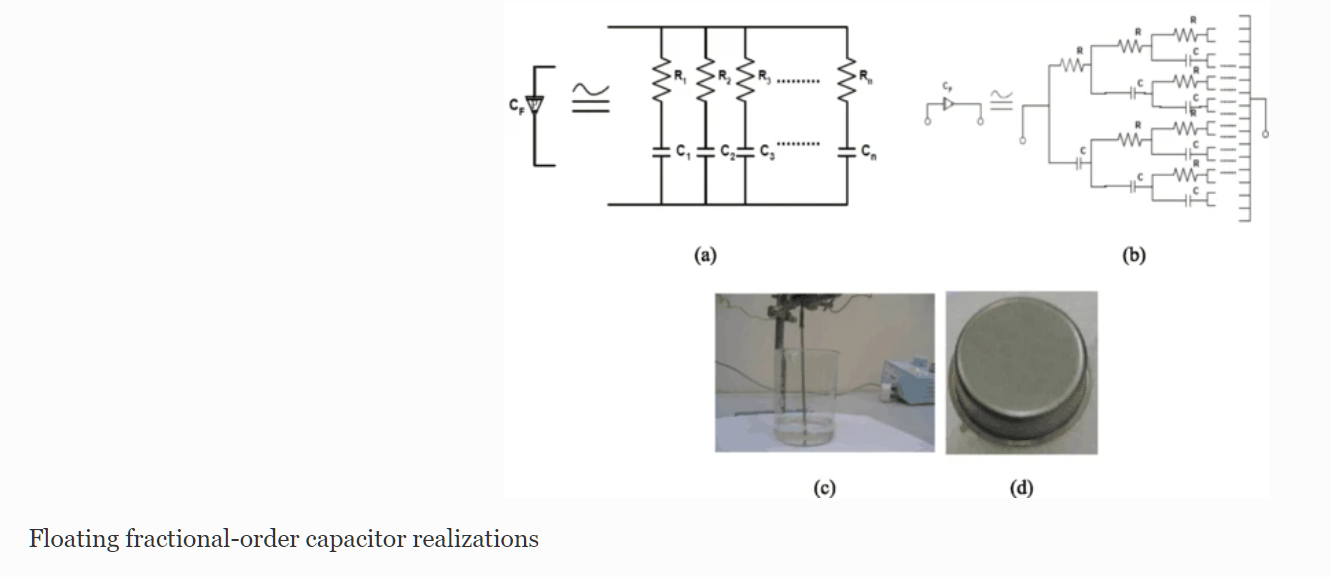
Optimization of fractional-order RLC filters
This paper introduces some generalized fundamentals for fractional-order RL β C α circuits as well as a gradient-based optimization technique in the frequency domain. One of the main advantages of the fractional-order design is that it increases the flexibility and degrees of freedom by means of the fractional parameters, which provide new fundamentals and can be used for better interpretation or best fit matching with experimental results. An analysis of the real and imaginary components, the magnitude and phase responses, and the sensitivity must be performed to obtain an optimal design
FPGA-Based Memristor Emulator Circuit for Binary Convolutional Neural Networks
Binary convolutional neural networks (BCNN) have been proposed in the literature for resource-constrained IoTs nodes and mobile computing devices. Such computing platforms have strict constraints on the power budget, system performance, processing and memory capabilities. Nonetheless, the platforms are still required to efficiently perform classification and matching tasks needed in various applications. The memristor device has shown promising results when utilized for in-memory computing architectures, due to its ability to perform storage and computation using the same physical element
High Speed, Approximate Arithmetic Based Convolutional Neural Network Accelerator
Convolutional Neural Networks (CNNs) for Artificial Intelligence (AI) algorithms have been widely used in many applications especially for image recognition. However, the growth in CNN-based image recognition applications raised challenge in executing millions of Multiply and Accumulate (MAC) operations in the state-of-The-Art CNNs. Therefore, GPUs, FPGAs, and ASICs are the feasible solutions for balancing processing speed and power consumption. In this paper, we propose an efficient hardware architecture for CNN that provides high speed, low power, and small area targeting ASIC implementation
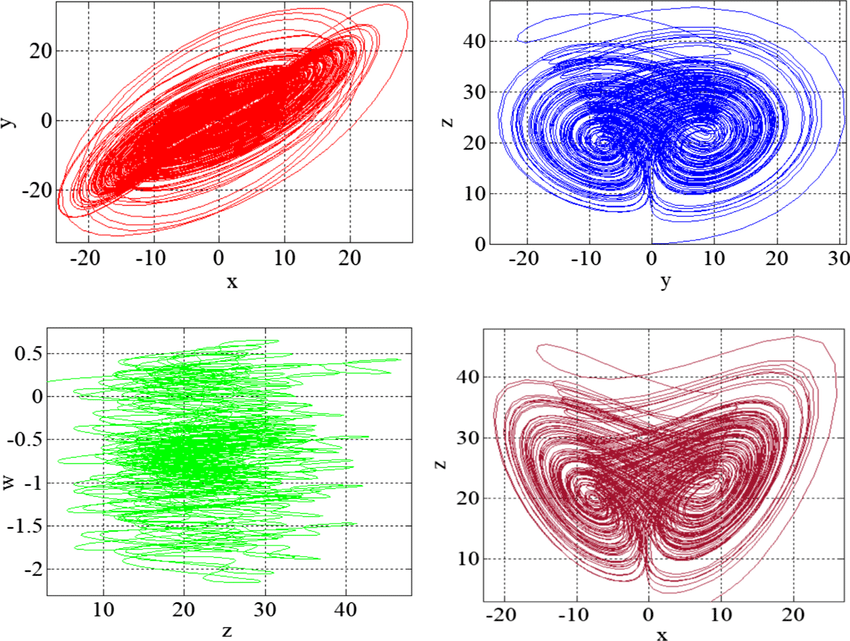
New hybrid synchronisation schemes based on coexistence of various types of synchronisation between master-slave hyperchaotic systems
In this paper, we present new approaches to study the co-existence of some types of synchronisation between hyperchaotic dynamical systems. The paper first analyses, based on stability theory of linear continuous-Time systems, the co-existence of the projective synchronisation (PS), the function projective synchronisation (FPS), the full state hybrid function projective synchronisation (FSHFPS) and the generalised synchronisation (GS) between general master and slave hyperchaotic systems. Successively, using Lyapunov stability theory, the coexistence of three different synchronisation types is
Pagination
- Previous page ‹‹
- Page 9
- Next page ››
