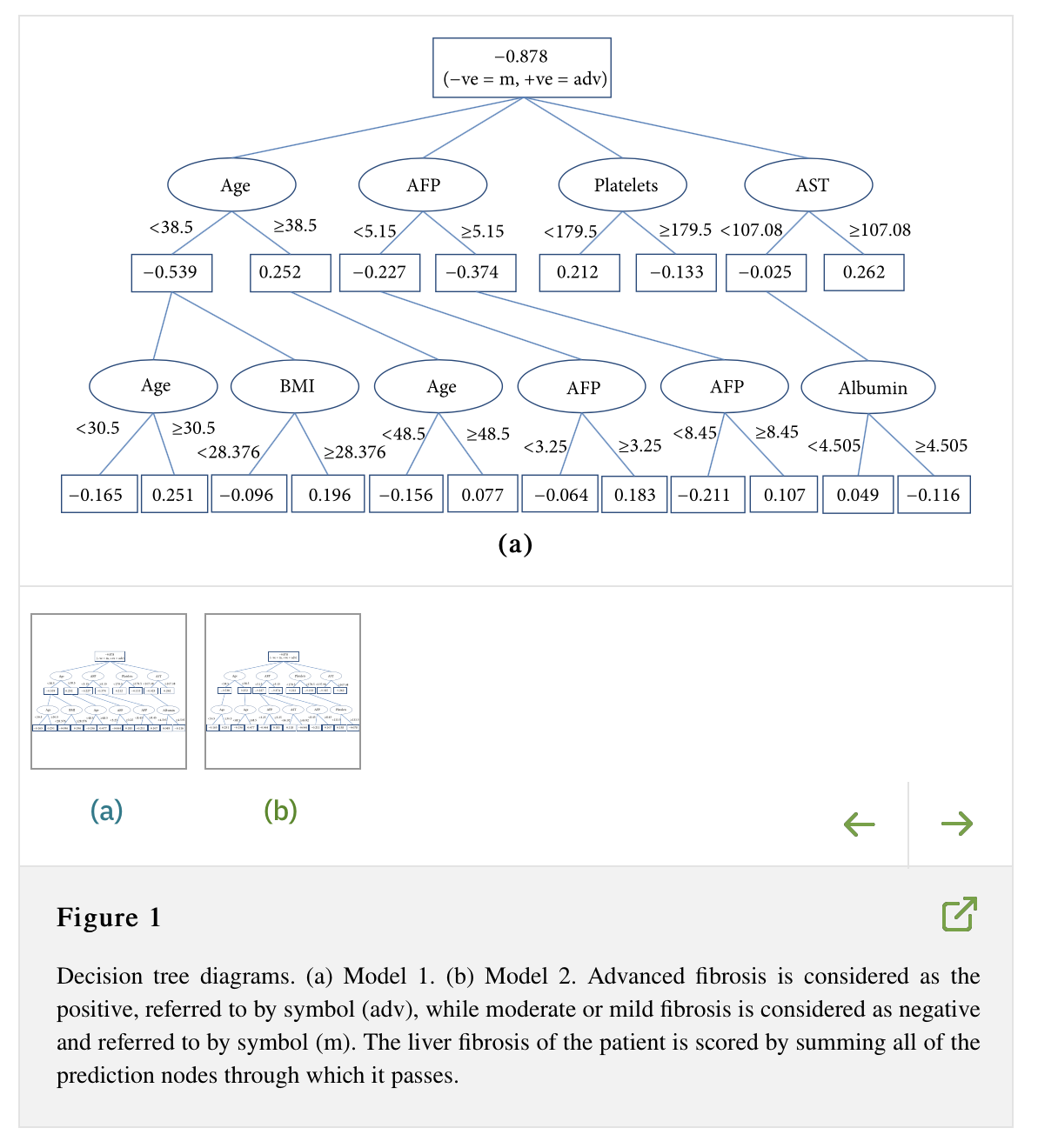
Accurate Prediction of Advanced Liver Fibrosis Using the Decision Tree Learning Algorithm in Chronic Hepatitis C Egyptian Patients
Background/Aim. Respectively with the prevalence of chronic hepatitis C in the world, using noninvasive methods as an alternative method in staging chronic liver diseases for avoiding the drawbacks of biopsy is significantly increasing. The aim of this study is to combine the serum biomarkers and clinical information to develop a classification model that can predict advanced liver fibrosis. Methods. 39,567 patients with chronic hepatitis C were included and randomly divided into two separate sets. Liver fibrosis was assessed via METAVIR score; patients were categorized as mild to moderate (F0
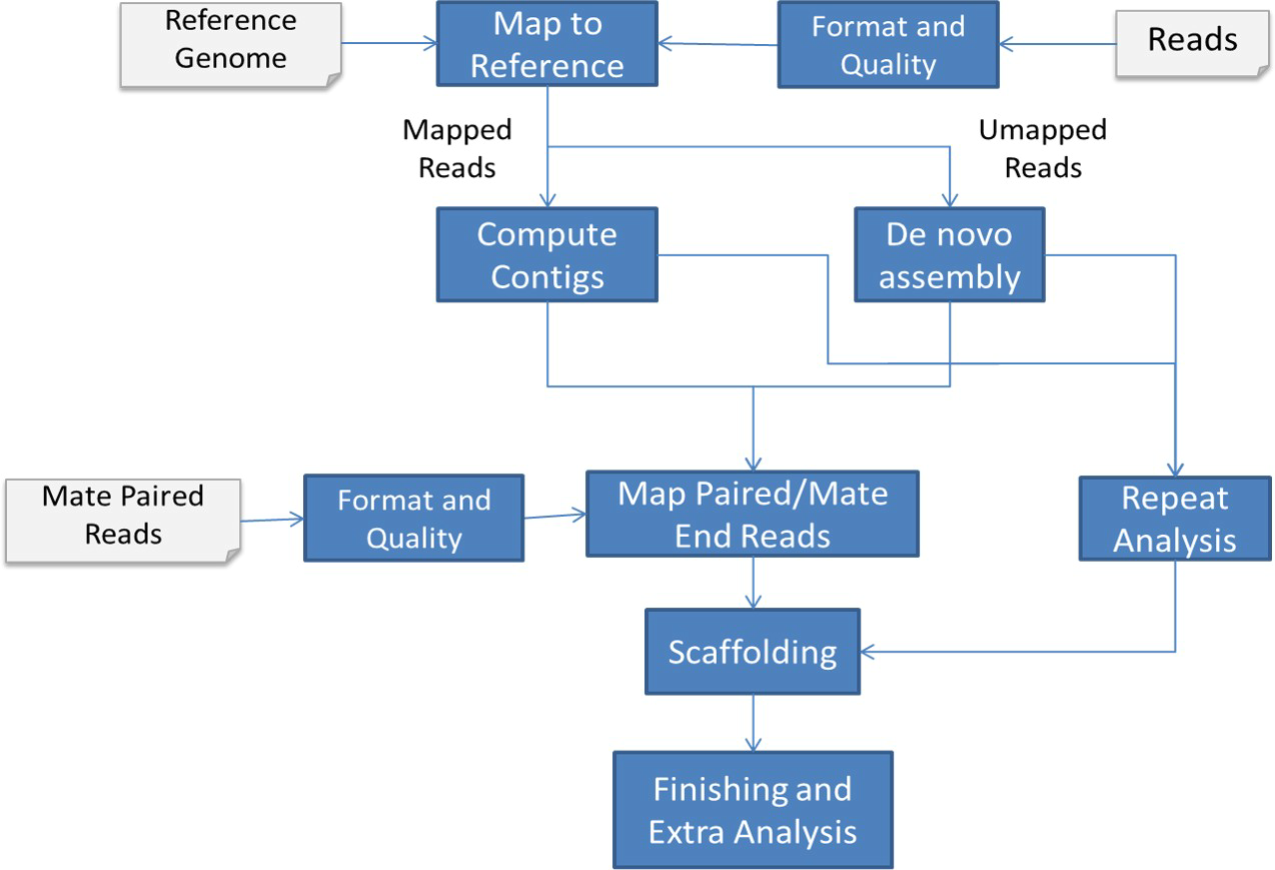
Sequencing and assembly of the Egyptian buffalo genome
Water buffalo (Bubalus bubalis) is an important source of meat and milk in countries with relatively warm weather. Compared to the cattle genome, a little has been done to reveal its genome structure and genomic traits. This is due to the complications stemming from the large genome size, the complexity of the genome, and the high repetitive content. In this paper, we introduce a high-quality draft assembly of the Egyptian water buffalo genome. The Egyptian breed is used as a dual purpose animal (milk/meat). It is distinguished by its adaptability to the local environment, quality of feed
On the effect of uplink power control on temporal retransmission diversity
Using stochastic geometry, this letter studies the retransmission performance in uplink cellular networks with fractional path-loss inversion power control (FPC). We first show that the signal-to-interference-ratio (SIR) is correlated across time, which imposes temporal diversity loss in the retransmission performance. In particular, FPC with lower path-loss compensation factor decreases inter-cell interference but suffers from degraded retransmission diversity. On the other hand, full path-loss inversion achieves almost full temporal diversity (i.e., temporal SIR independence) at the expense
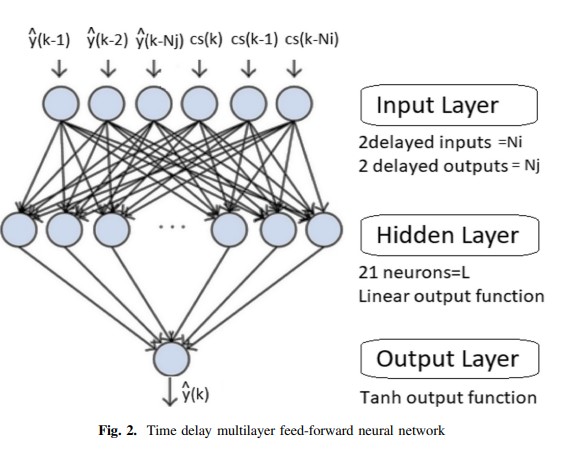
Performance Evaluation of Research Reactors Under Different Predictive Controllers
This paper is concerned with the evaluation of nuclear research reactor under two types of predictive controllers. The first one is Receding Horizon Predictive Controller (RHPC) which is considered a simple linear predictive controller. The other one is Neural Network Predictive Controller (NNPC) which is a type of nonlinear predictive controller. These controllers are applied over multi-point reactor core model. This model takes into consideration the nonlinearity of the reactor. It also takes into consideration some important physical phenomena like temperature effect, time variant fuel
Predicting Remaining Cycle Time from Ongoing Cases: A Survival Analysis-Based Approach
Predicting the remaining cycle time of running cases is one important use case of predictive process monitoring. Different approaches that learn from event logs, e.g., relying on an existing representation of the process or leveraging machine learning approaches, have been proposed in literature to tackle this problem. Machine learning-based techniques have shown superiority over other techniques with respect to the accuracy of the prediction as well as freedom from knowledge about the underlying process models generating the logs. However, all proposed approaches learn from complete traces

Quantum video encryption based on qubit-planes controlled-XOR operations and improved logistic map
This paper proposes an efficient and secure quantum video encryption algorithm for quantum videos based on qubit-planes controlled-XOR operations and improved logistic map in multi-layer encryption steps. Three simple cryptosystem steps are presented in the proposed approach to accomplish the whole encryption process: inter-frame permutation, intra-frame pixel position geometric transformation, and high 4-intra-frame-qubit-planes scrambling. Firstly, the inter-frame positions of quantum video are permutated via inter-frame permutation that is controlled by the keys which are generated by
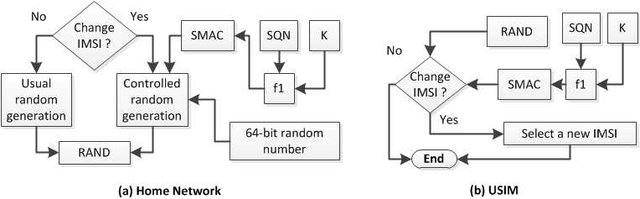
User Privacy in Legacy Mobile Network Protocols
Current security issues in mobile networks have great impact on user privacy. With the focus directed to signaling protocols security, network security and air interface encryption, critical configurations and design flaws that would impact user privacy can be overlooked. The leakage of IMSI on the broadcast channels during network paging is a privacy issue worth considering. In this paper, we present an experimental analysis for the IMSI leakage in the GSM broadcast channels during the paging procedure and the impact of this type of passive attack on user's privacy. © 2018 IEEE.
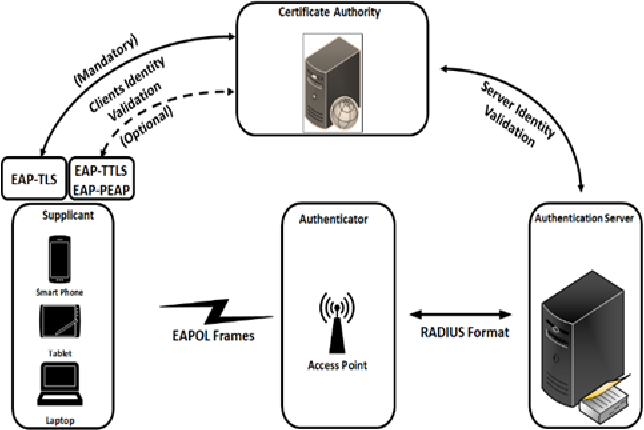
Enterprise WLAN security flaws current attacks and relative mitigations
The Increasing number of mobiles and handheld devices that allow wireless access to enterprise data and services is considered a major concern for network designers, implementers and analysts. Enhancements of wireless technologies also accelerate the adoptions of enterprise wireless networks that are widely deployed solely or as an extension to existing wired networks. Bring Your Own Device is an example of the new challenging wireless trends. BYOD environments allow the use of personal mobile computing devices like smart phones, tablets, and laptops for business activities. BYOD has become
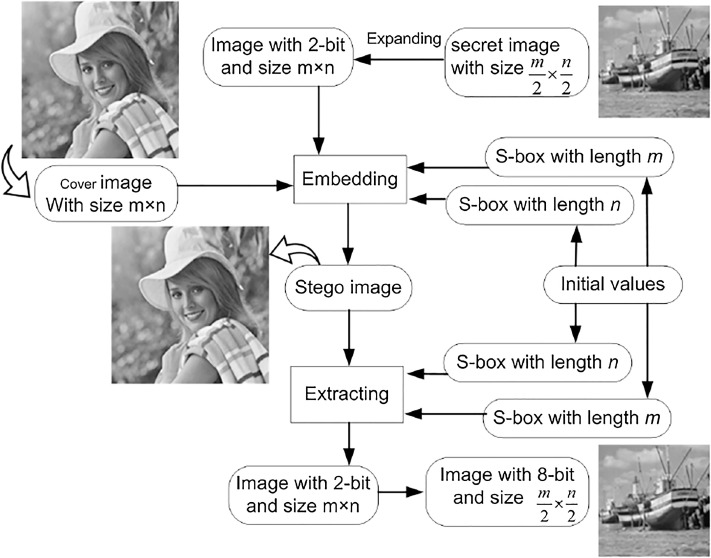
A novel image steganography technique based on quantum substitution boxes
Substitution boxes play an essential role in designing secure cryptosystems. With the evolution of quantum technologies, current data security mechanisms may be broken due to their construction based on mathematical computation. Quantum walks, a universal quantum computational model, play an essential role in designing quantum algorithms. We utilize the benefits of quantum walks to present a novel technique for constructing substitution boxes (S-boxes) based on quantum walks (QWs). The performance of the presented QWs S-box technique is evaluated by S-box evaluation criteria, and our results
Cyber Threats and Policies for Industrial Control Systems
Modern Industrial Control Systems (ICS) are very important in our life as we use information and communication technology (ICT) to manage, monitor and improve ICS usage. This continually exposes it to new threats due to the vulnerabilities and architectural weaknesses introduced by the extensive use of ICT. Different types of ICSs have common attacks in which these attacks are very sophisticated and have a great impact. This paper presents the results of our research on the impact of ICT attacks. Besides, it discusses how to protect ICS from attacks and policies/standards that each nation
Pagination
- Previous page ‹‹
- Page 18
- Next page ››
