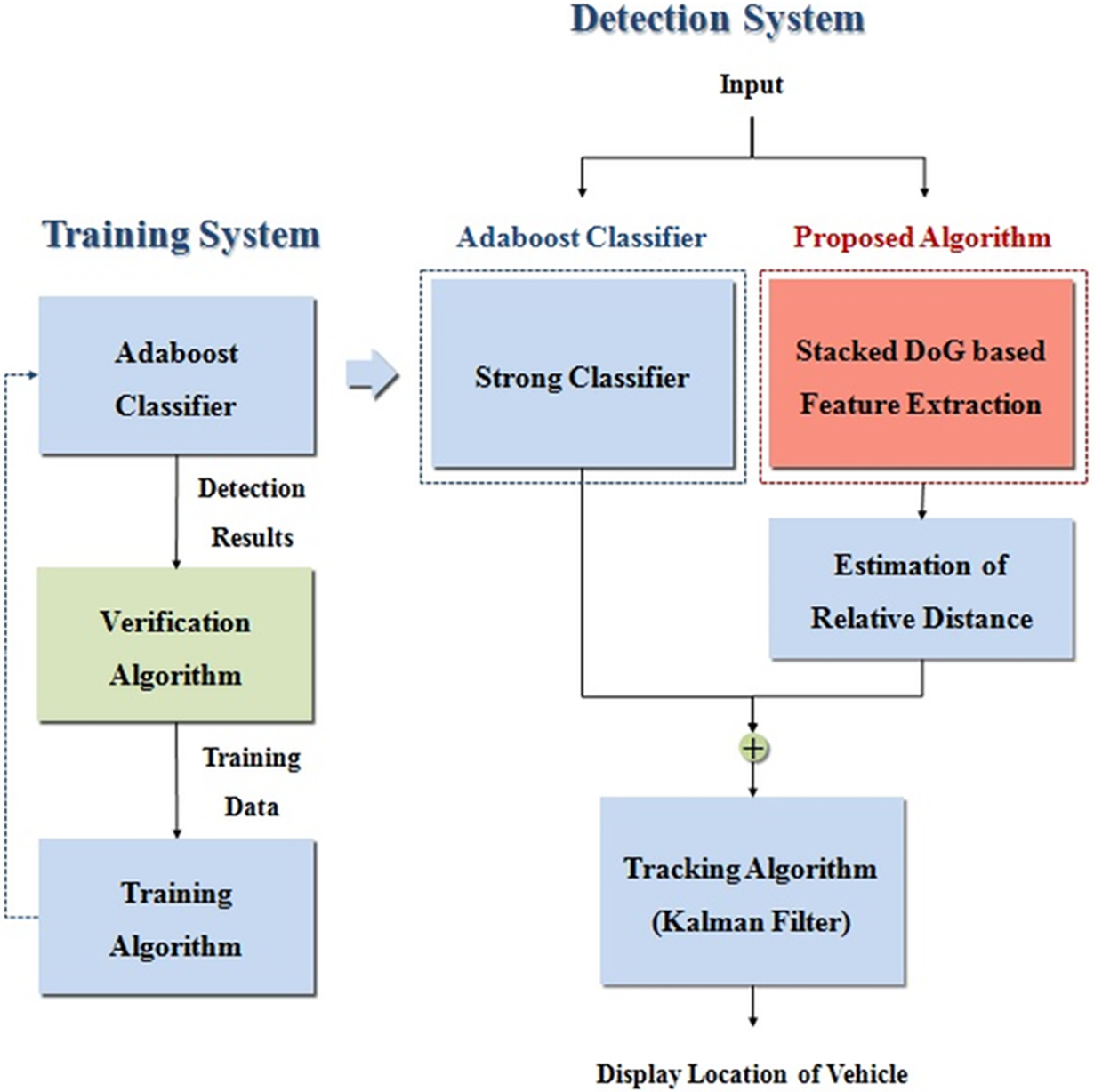
A Novel Vehicle Detection System
Histogram of oriented gradient (HOG) feature has been widely used in vehicle detection. In this paper, a modified version of HOG is proposed by introducing compass gradient into the HOG calculation. Three different versions of the modified HOG features are used as an input for linear and nonlinear support vector machine (SVM). The modified HOG variants proved to have better classification performance than that of the standard HOG. The classification results of modified HOG and nonlinear SVM are compared to the classification results of YOLO object detector. Finally, a vehicle detection system
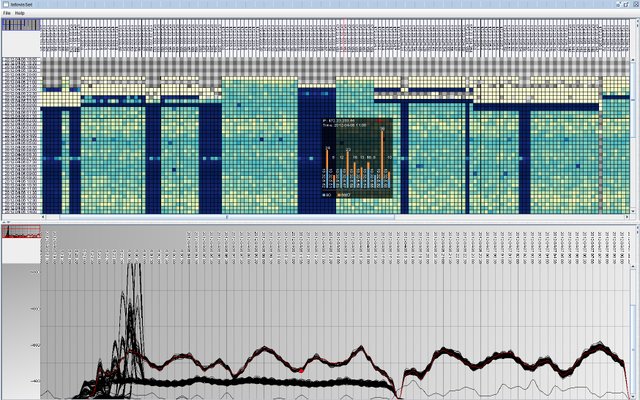
VAFLE: Visual analytics of firewall log events
In this work, we present VAFLE, an interactive network security visualization prototype for the analysis of firewall log events. Keeping it simple yet effective for analysts, we provide multiple coordinated interactive visualizations augmented with clustering capabilities customized to support anomaly detection and cyber situation awareness. We evaluate the usefulness of the prototype in a use case with network traffic datasets from previous VAST Challenges, illustrating its effectiveness at promoting fast and well-informed decisions. We explain how a security analyst may spot suspicious
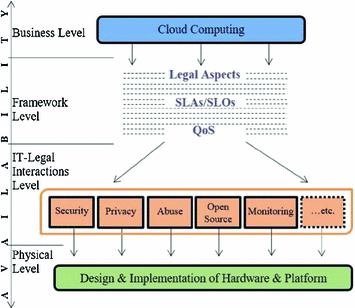
Enabling cloud business by QoS roadmap
Day after day, global economy becomes tougher. It is a fact in which Cloud Computing business gets impacted the most. When it comes to cost, Cloud Computing is the most attractive paradigm for IT solutions. It is because Cloud Computing relaxes cost constraints. This relaxing enables Cloud Customers to operate their business through Cloud Computing under such economic pressure. On the other side, Cloud Computing solutions should deliver IT services at the agreed and acceptable Quality of Service levels. This moves the economic challenges from Cloud Customer premises to Cloud Provider premises
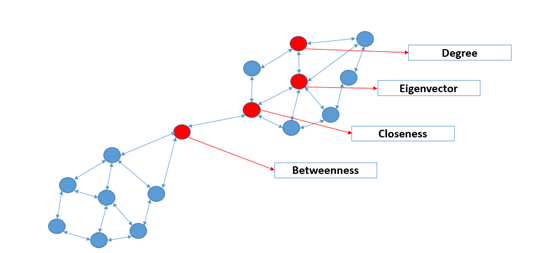
Enhanced customer churn prediction using social network analysis
There were 6.8 billion estimates for mobile subscriptions worldwide by end of 2013 [11]. As the mobile market gets saturated, it becomes harder for telecom providers to acquire new customers, and makes it essential for them to retain their own. Due to the high competition between different telecom providers and the ability of customers to move from one provider to another, all telecom service providers suffer from customer churn. As a result, churn prediction has become one of the main telecom challenges. The primary goal of churn prediction is to predict a list of potential churners, so that
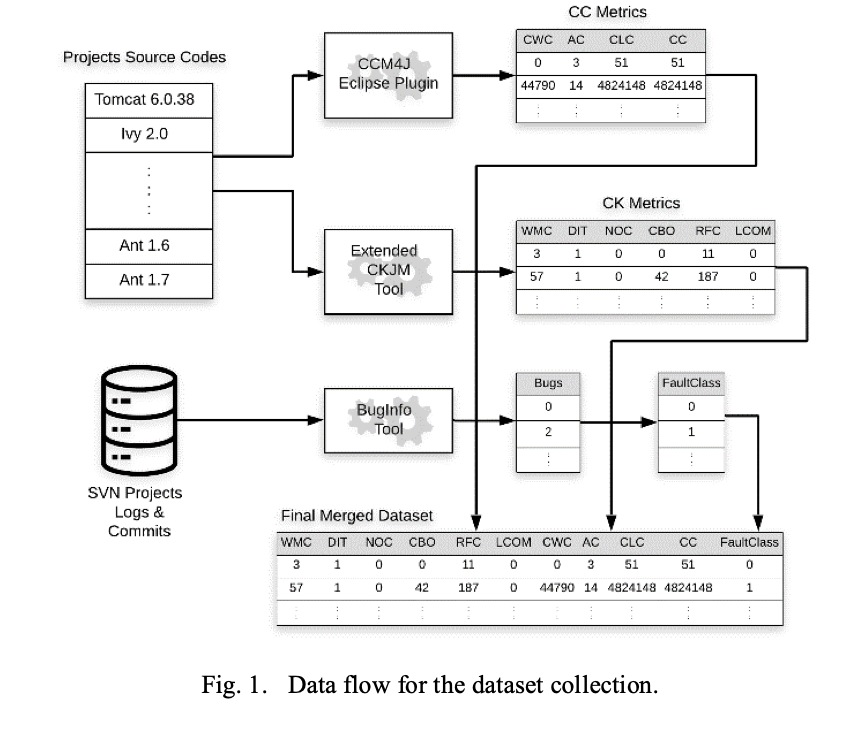
A Universal Model for Defective Classes Prediction Using Different Object-Oriented Metrics Suites
Recently, research studies were directed to the construction of a universal defect prediction model. Such models are trained using different projects to have enough training data and be generic. One of the main challenges in the construction of a universal model is the different distributions of metrics in various projects. In this study, we aim to build a universal defect prediction model to predict software defective classes. We also aim to validate the Object-Oriented Cognitive Complexity metrics suite (CC metrics) for its association with fault-proneness. Finally, this study aims to
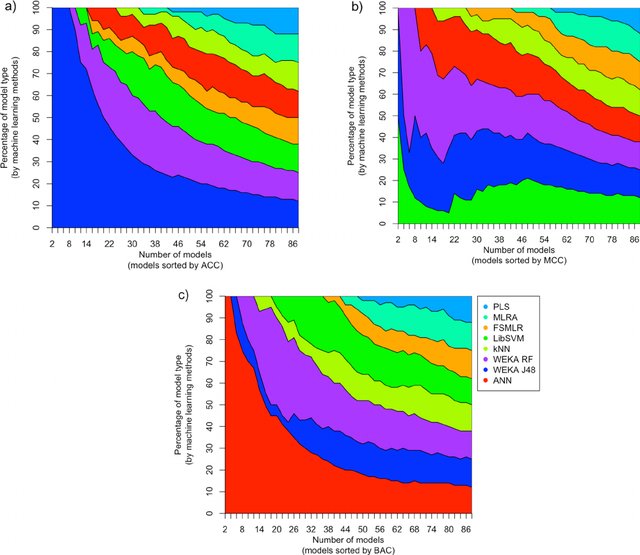
Using Molecular Fingerprints as Descriptors in Toxicity Prediction: A Survey
During humans' lifetime, their bodies deal with different chemicals through various sources. Chemical toxicity is a challenging problem that needs rapid and efficient methods for evaluation of environmental chemicals, or medications development. Computer science helps in toxicity prediction through building models from pre-tested compounds by learning from data. These models raise a flag to avoid trying some combinations for trial in wet-lab, which reduces the high cost of clinical trials. A compound chemical structure features are represented by Molecular Fingerprint. This survey searches for
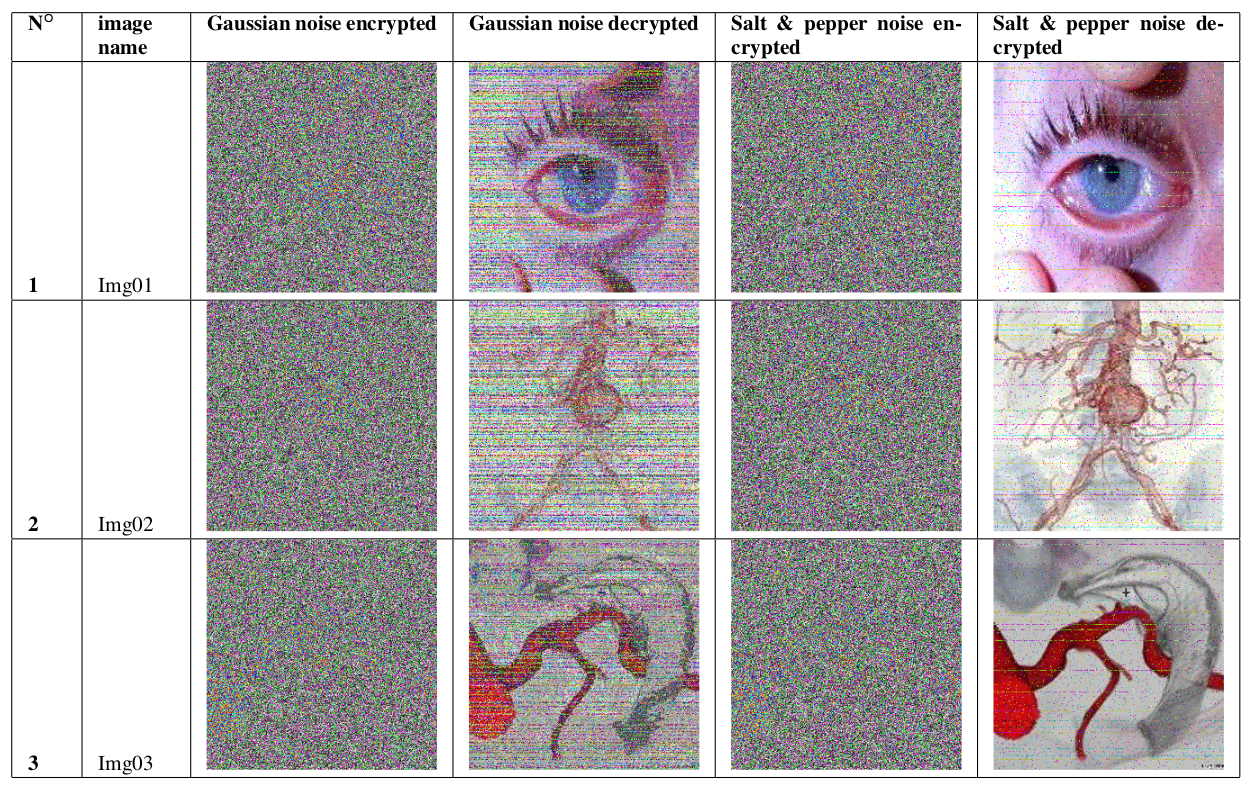
A New Chaotic Map with Dynamic Analysis and Encryption Application in Internet of Health Things
In this paper, we report an effective cryptosystem aimed at securing the transmission of medical images in an Internet of Healthcare Things (IoHT) environment. This contribution investigates the dynamics of a 2-D trigonometric map designed using some well-known maps: Logistic-sine-cosine maps. Stability analysis reveals that the map has an infinite number of solutions. Lyapunov exponent, bifurcation diagram, and phase portrait are used to demonstrate the complex dynamic of the map. The sequences of the map are utilized to construct a robust cryptosystem. First, three sets of key streams are
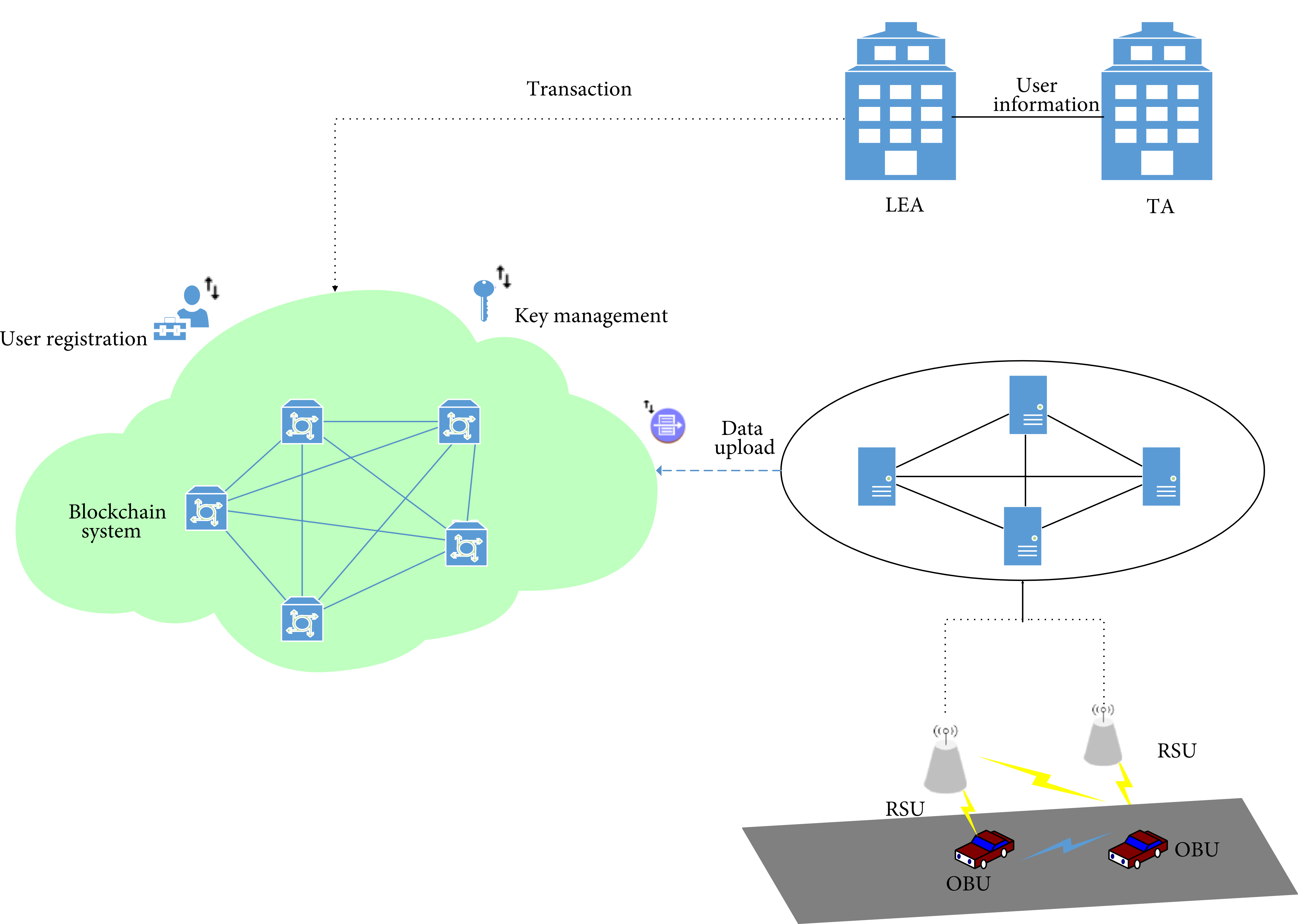
Using Blockchain Technology for the Internet of Vehicles
The Internet of Vehicles (IoV) aims to connect vehicles with their surroundings and share data. In IoV, various wireless technologies like 5G, WIFI, DSRC, WiMAX, and ZigBee are used. To share data within wireless surroundings in a secure way, some security aspects need to be fulfilled. Blockchain technology is a good fit to cover these countermeasures. IoV uses a lot of technologies and interacts with different types of wireless nodes, and this increases the vulnerability to some attacks that could endanger lives. Using blockchain technology within the IoV architecture could provide efficient
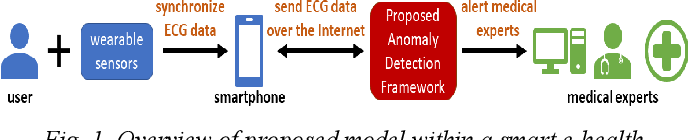
A Multitier Deep Learning Model for Arrhythmia Detection
An electrocardiograph (ECG) is employed as a primary tool for diagnosing cardiovascular diseases (CVDs). ECG signals provide a framework to probe the underlying properties and enhance the initial diagnosis obtained via traditional tools and patient-doctor dialogs. Notwithstanding its proven utility, deciphering large data sets to determine appropriate information remains a challenge in ECG-based CVD diagnosis and treatment. Our study presents a deep neural network (DNN) strategy to ameliorate the aforementioned difficulties. Our strategy consists of a learning stage where classification
Efficient quantum-based security protocols for information sharing and data protection in 5G networks
Fifth generation (5G)networks aim at utilizing many promising communication technologies, such as Cloud Computing, Network Slicing, and Software Defined Networking. Supporting a massive number of connected devices with 5G advanced technologies and innovating new techniques will surely bring tremendous challenges for trust, security and privacy. Therefore, secure mechanisms and protocols are required as the basis for 5G networks to address this security challenges and follow security-by-design but also security-by-operations rules. In this context, new efficient cryptographic protocols and
Pagination
- Previous page ‹‹
- Page 19
- Next page ››
