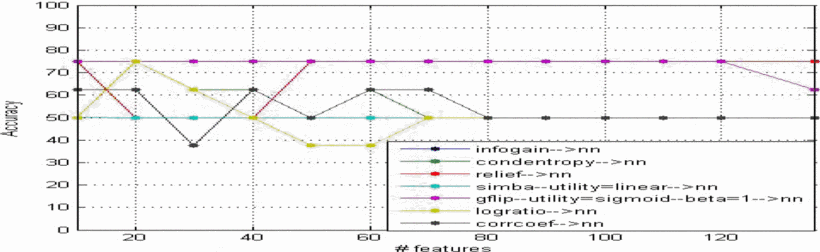
Feature selection in computer aided diagnostic system for microcalcification detection in digital mammograms
In this paper an approach is proposed to develop a computer-aided diagnosis (CAD) system that can be very helpful for radiologist in diagnosing microcalcifications' patterns in digitized mammograms earlier and faster than typical screening programs and showed the efficiency of feature selection on the CAD system. The proposed method has been implemented in four stages: (a) the region of interest (ROI) selection of 32x32 pixels size which identifies clusters of microcalcifications, (b) the feature extraction stage is based on the wavelet decomposition of locally processed image (region of
Extreme Points Derived Confidence Map as a Cue for Class-Agnostic Interactive Segmentation Using Deep Neural Network
To automate the process of segmenting an anatomy of interest, we can learn a model from previously annotated data. The learning-based approach uses annotations to train a model that tries to emulate the expert labeling on a new data set. While tremendous progress has been made using such approaches, labeling of medical images remains a time-consuming and expensive task. In this paper, we evaluate the utility of extreme points in learning to segment. Specifically, we propose a novel approach to compute a confidence map from extreme points that quantitatively encodes the priors derived from
Controlled alternate quantum walks based privacy preserving healthcare images in Internet of Things
The development of quantum computers and quantum algorithms conveys a challenging scenario for several cryptographic protocols due to the mathematical scaffolding upon which those protocols have been built. Quantum walks constitute a universal quantum computational model which is widely used in various fields, including quantum algorithms and cryptography. Quantum walks can be utilized as a powerful tool for the development of modern chaos-based cryptographic applications due to their nonlinear dynamical behavior and high sensitivity to initial conditions. In this paper, we propose new
Features selection for building an early diagnosis machine learning model for Parkinson's disease
In this work, different approaches were evaluated to optimize building machine learning classification models for the early diagnosis of the Parkinson disease. The goal was to sort the medical measurements and select the most relevant parameters to build a faster and more accurate model using feature selection techniques. Decreasing the number of features to build a model could lead to more efficient machine learning algorithm and help doctors to focus on what are the most important measurements to take into account. For feature selection we compared the Filter and Wrapper techniques. Then we

NONYM!ZER: Mitigation Framework for Browser Fingerprinting
Not only recent compelled cookies regulations have radically restrained their threats but also increased people awareness has played a fundamental part. This has placed huge pressure on enterprises to find alternatives to bridge this gap and satisfy business demands. Since then fingerprinting has gained enormous popularity. In this paper, we introduce 'nonym!zer' as a mitigation framework for browser fingerprinting. It helps to hinder or impede browser fingerprinting on desktop browsers that web servers use such as WebGL or Canvas technologies. © 2019 IEEE.
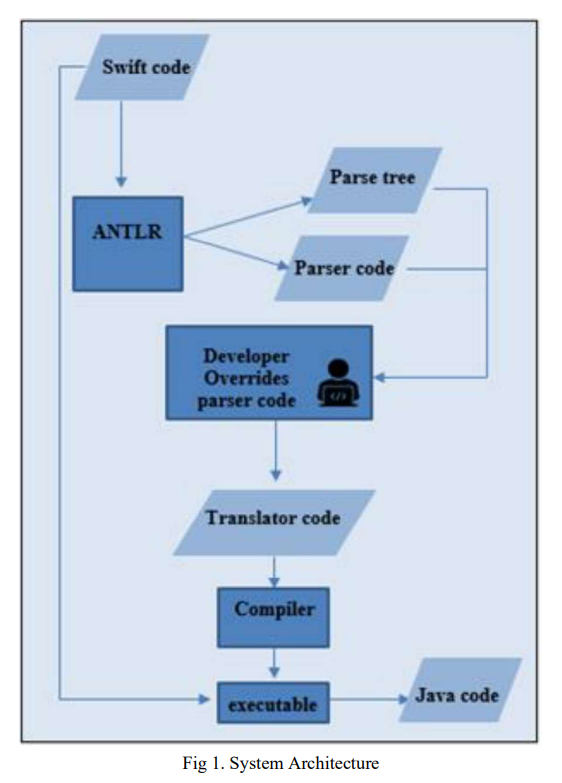
Trans-Compiler based Mobile Applications code converter: Swift to java
Numerous commercial tools like Xamarin, React Native and PhoneGap utilize the concept of cross-platform mobile applications development that builds applications once and runs it everywhere opposed to native mobile app development that writes in a specific programming language for every platform. These commercial tools are not very efficient for native developers as mobile applications must be written in specific language and they need the usage of specific frameworks. In this paper, a suggested approach in TCAIOSC tool to convert mobile applications from Android to iOS is used to develop the
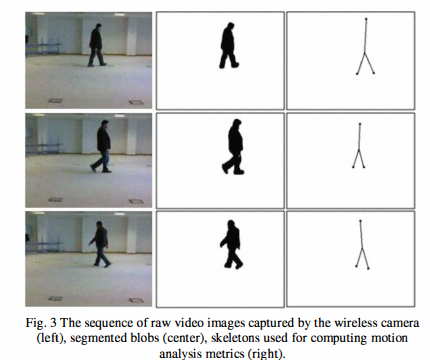
Ambient and wearable sensing for gait classification in pervasive healthcare environments
Pervasive healthcare environments provide an effective solution for monitoring the wellbeing of the elderly where the general trend of an increasingly ageing population has placed significant burdens on current healthcare systems. An important pervasive healthcare system functionality is patient motion analysis where gait information can be used to detect walking behavior abnormalities that may indicate the onset of adverse health problems, for quantifying post-operative recovery, and to observe the progression of neurodegenerative diseases. The development of accurate motion analysis models
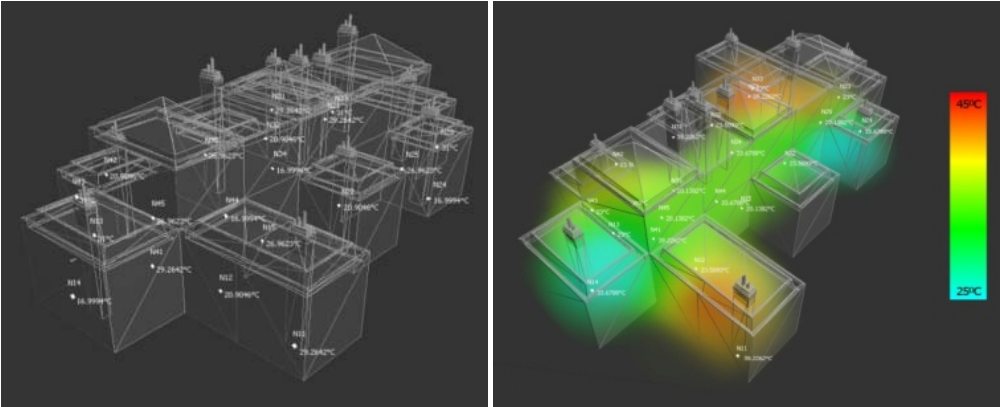
Monitoring and visualization of large WSN deployments
Recent developments in wireless sensor networks have ushered in novel ubiquitous computing applications based on distributed large-scale data acquisition and interactive interpretation. However, current WSNs suffer from lack of effective tools to support large network deployment and administration as well as unavailability of interactive visualization techniques required to explore and analyze captured sensing data, which is hindering the development of real-life WSN-based ubiquitous systems. Sensor Explorer addresses the above problems by providing modular efficient stream management engine
Cloud computing security: Challenges & future trends
Cloud computing is one of the most trendy terminologies. Cloud providers aim to satisfy clients' requirements for computing resources such as services, applications, networks, storage and servers. They offer the possibility of leasing these resources rather than buying them. Many popular companies, such as Amazon, Google and Microsoft, began to enhance their services and apply the technology of cloud computing to provide cloud environment for their customers. Although there are lots of advantages in using a cloud-based system, some issues must be handled before organisations and individuals
Convergence study of IPv6 tunneling techniques
IPv4 address exhaustion pushed IETF to create IPv6, the improved substitute of IPv4. The Internet complexity and its enormous size prolong the transition from IPv4 to IPv6 process. This means that both versions will necessarily co-exist. Meanwhile, tunneling appears as a solution trend. The tunneling is a transition technique that is considered temporary till all ISPs would support IPv6. At this paper, we compare the routing convergence of two tunnel types, 6to4 and Manually Configured versus the conventional IPv4 and IPv6 protocols. We analyze the network resources consumed during cold start
Pagination
- Previous page ‹‹
- Page 24
- Next page ››
