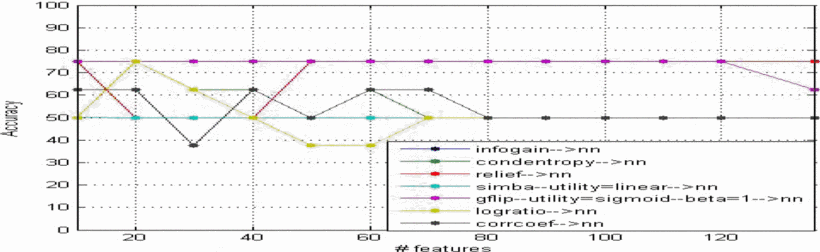
Feature selection in computer aided diagnostic system for microcalcification detection in digital mammograms
In this paper an approach is proposed to develop a computer-aided diagnosis (CAD) system that can be very helpful for radiologist in diagnosing microcalcifications' patterns in digitized mammograms earlier and faster than typical screening programs and showed the efficiency of feature selection on the CAD system. The proposed method has been implemented in four stages: (a) the region of interest (ROI) selection of 32x32 pixels size which identifies clusters of microcalcifications, (b) the feature extraction stage is based on the wavelet decomposition of locally processed image (region of
Towards scalable and cost-aware bioinformatics workflow execution in the cloud - Recent advances to the tavaxy workflow system
Cloud-based scientific workflow systems can play an important role in the development of cost effective bioinformatics analysis applications. So far, most efforts for supporting cloud computing in such workflow systems have focused on simply porting them to the cloud environment. The next due steps are to optimize these systems to exploit the advantages of the cloud computing model, basically in terms of managing resource elasticity and the associated business model. In this paper, we introduce new advancements in designing scalable and cost-effective workflows in the cloud using the Tavaxy
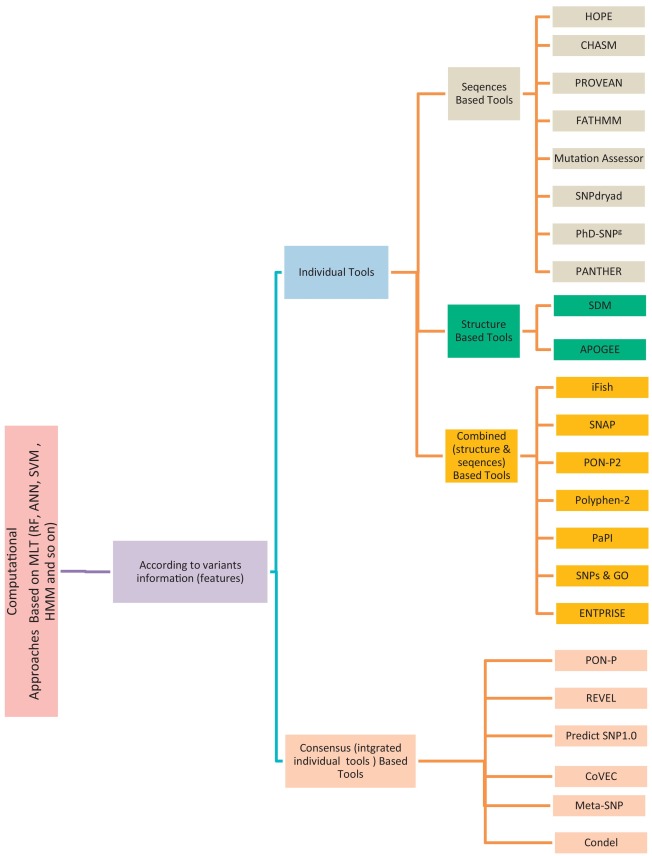
A review study: Computational techniques for expecting the impact of non-synonymous single nucleotide variants in human diseases
Non-Synonymous Single-Nucleotide Variants (nsSNVs) and mutations can create a diversity effect on proteins as changing genotype and phenotype, which interrupts its stability. The alterations in the protein stability may cause diseases like cancer. Discovering of nsSNVs and mutations can be a useful tool for diagnosing the disease at a beginning stage. Many studies introduced the various predicting singular and consensus tools that based on different Machine Learning Techniques (MLTs) using diverse datasets. Therefore, we introduce the current comprehensive review of the most popular and recent
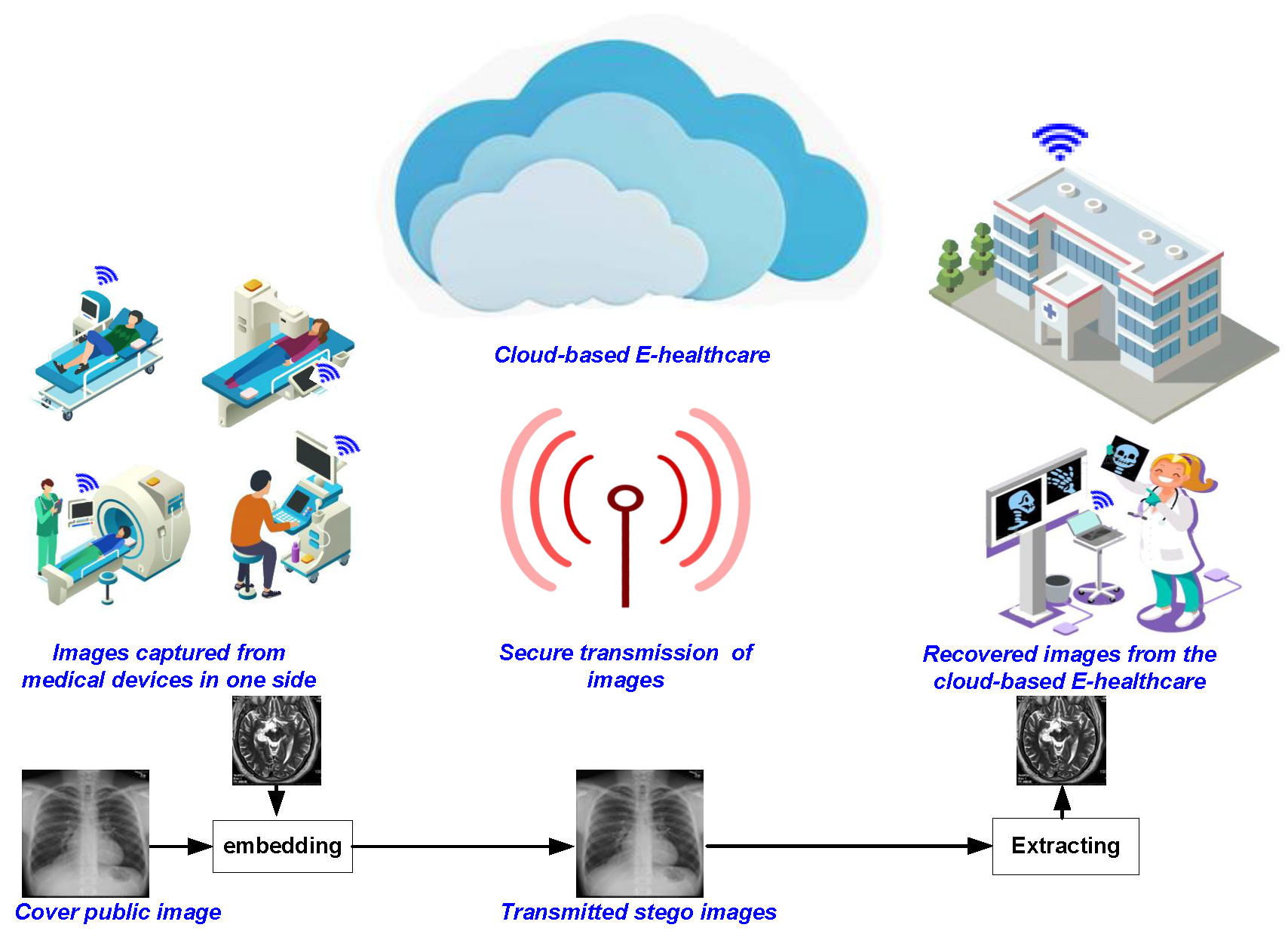
A robust quasi-quantum walks-based steganography protocol for secure transmission of images on cloud-based E-healthcare platforms
Traditionally, tamper-proof steganography involves using efficient protocols to encrypt the stego cover image and/or hidden message prior to embedding it into the carrier object. However, as the inevitable transition to the quantum computing paradigm beckons, its immense computing power will be exploited to violate even the best non-quantum, i.e., classical, stego protocol. On its part, quantum walks can be tailored to utilise their astounding ‘quantumness’ to propagate nonlinear chaotic behaviours as well as its sufficient sensitivity to alterations in primary key parameters both important
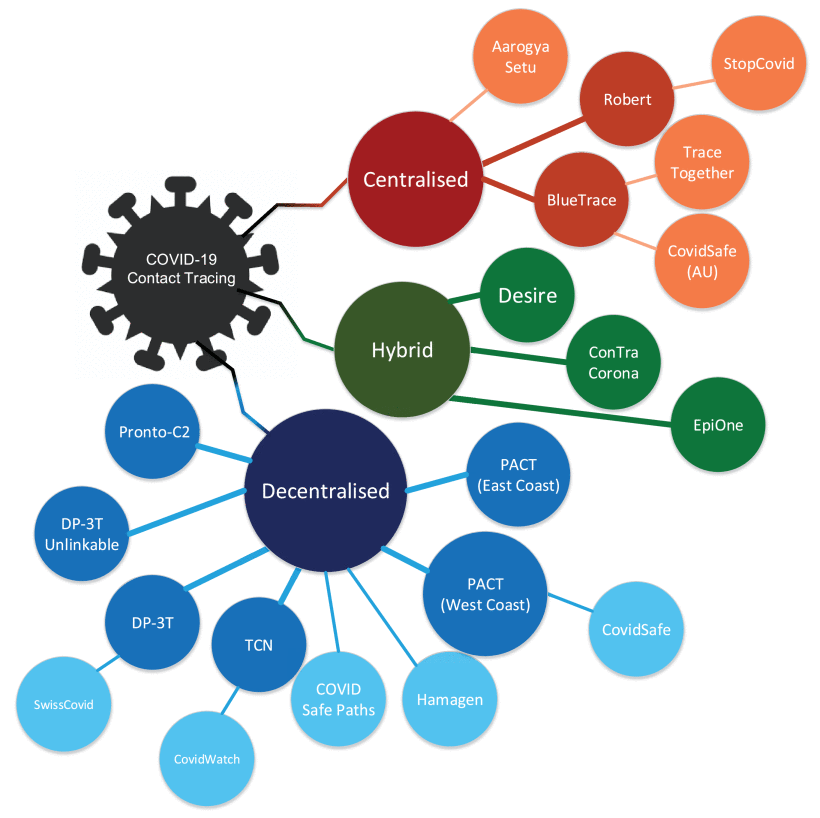
A Survey of COVID-19 Contact Tracing Apps
The recent outbreak of COVID-19 has taken the world by surprise, forcing lockdowns and straining public health care systems. COVID-19 is known to be a highly infectious virus, and infected individuals do not initially exhibit symptoms, while some remain asymptomatic. Thus, a non-negligible fraction of the population can, at any given time, be a hidden source of transmissions. In response, many governments have shown great interest in smartphone contact tracing apps that help automate the difficult task of tracing all recent contacts of newly identified infected individuals. However, tracing
Complexwavelet Transform Cwt Based Video Magnification for 3d Facial Video Identification
Magnifying micro changes in motion and brightness of videos that are unnoticeable by the human visual system have recently been an interesting area to explore. In this paper, we explore this technique in 3D facial video identification, we utilize this technique to identify 3D objects from 2D images. We present a Complex Wavelet Transform CWT, 2D-Dual CWT based technique, to calculate any changes between subsequent video frames of CWT sub-bands at different spatial locations. In this technique, a gradient based method is proposed to determine the orientation of each CWT sub band in addition to
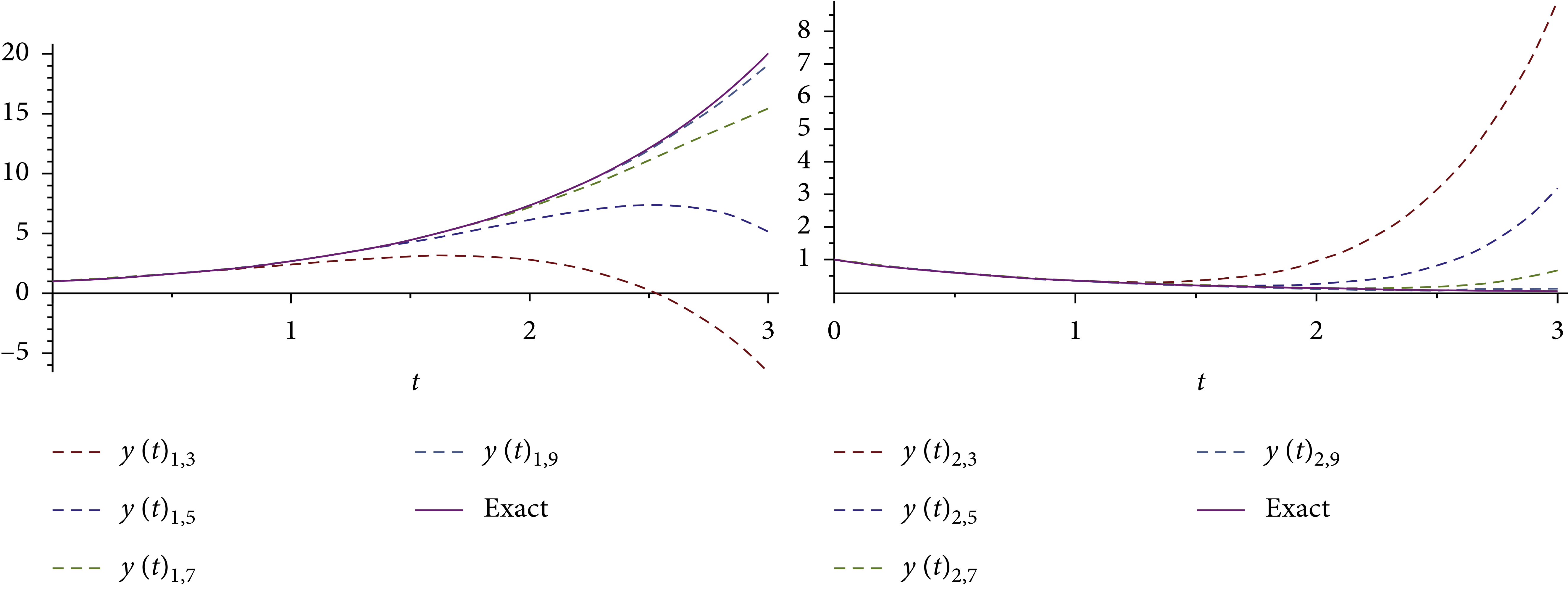
An Analytical Computational Algorithm for Solving a System of Multipantograph DDEs Using Laplace Variational Iteration Algorithm
In this research, an approximation symbolic algorithm is suggested to obtain an approximate solution of multipantograph system of type delay differential equations (DDEs) using a combination of Laplace transform and variational iteration algorithm (VIA). The corresponding convergence results are acquired, and an efficient algorithm for choosing a feasible Lagrange multiplier is designed in the solving process. The application of the Laplace variational iteration algorithm (LVIA) for the problems is clarified. With graphics and tables, LVIA approximates to a high degree of accuracy with a few
IoT Based AI and its Implementations in Industries
The Internet of Things (IoT) is an Internet revolution that is increasingly used in business, industry, medicine, the economy and other modern information society. IoT, particularly transport, industrial robots and automation systems are supported by artificial intelligence in a wide range of daily implementations with dominant industrial applications. IoT is an interconnected network of physical objects, which enables them to gather and share information, using software, sensor units and network connectivity. In industries; IoT brought about a new revolution in industries. In the field of IoT
Controlled alternate quantum walk-based pseudo-random number generator and its application to quantum color image encryption
Pseudo-random number generator (PRNG) are a key component in the design of modern cryptographic mechanisms and are regarded as a backbone element of many modern cryptographic applications. However and in spite of their robustness, quantum computers could crack down PNGR-based systems. Quantum walks, a universal model of quantum computation, have nonlinear properties that make them a robust candidate to produce PRNG. In this paper, we utilize controlled alternate quantum walk (CAQW) to create PRNG. Moreover, we use the presented PRNG mechanism as a component of a new quantum color image
Combating sybil attacks in vehicular ad hoc networks
Vehicular Ad Hoc Networks (VANETs) are considered as a promising approach for facilitating road safety, traffic management, and infotainment dissemination for drivers and passengers. However, they are subject to an attack that has a severe impact on their security. This attack is called the Sybil attack, and it is considered as one of the most serious attacks to VANETs, and a threat to lives of drivers and passengers. In this paper, we propose a detection scheme for the Sybil attack. The idea is based on public key cryptography and aims to ensure privacy preservation, confidentiality, and non
Pagination
- Previous page ‹‹
- Page 23
- Next page ››
