Improved spectrum mobility using virtual reservation in collaborative cognitive radio networks
Cognitive radio technology would enable a set of secondary users (SU) to opportunistically use the spectrum licensed to a primary user (PU). On the appearance of this PU on a specific frequency band, any SU occupying this band should free it for PUs. Typically, SUs may collaborate to reduce the impact of cognitive users on the primary network and to improve the performance of the SUs. In this paper, we propose and analyze the performance of virtual reservation in collaborative cognitive networks. Virtual reservation is a novel link maintenance strategy that aims to maximize the throughput of
Integrated VLC/RF Wireless Technologies for Reliable Content Caching System in Vehicular Networks
In a vehicular communications environment, the need for information sharing, entertainment, and multimedia will increase, leading to congestion of backhaul networks. The major challenge of this network is latency and resource limitations. Proactive caching can be obtained from local caches rather than from remote servers, which can avoid long delays resulting from limited backhaul capacity and resources. Therefore, proactive caching reduces latency and improves the quality of services. Determining which files should be cached in memory is a critical issue. The paper proposes various placement
Indoor localization and movement prediction algorithms with light-fidelity
Indoor localization has recently attended an increase in interest due to the potential for a wide range of services. In this paper, indoor high-precision positioning and motion prediction algorithms are proposed by using light fidelity (LI-FI) system with angular diversity receiver (ADR). The positioning algorithm uses to estimate the location of an object in the room. Furthermore, the prediction algorithm applies to predict the motion of that object. The simulation results show that the average root mean squares error of the positioning algorithm is about 0.6 cm, and the standard deviation
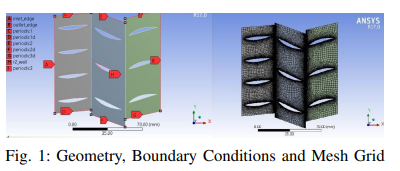
Optimized Preliminary Design of a Multistage Low-Speed Axial FLow Compressor
This paper proposes a technique based on a MAT-LAB code capable of getting an optimized preliminary design of an efficient low-speed compressor qualified for laboratory experiments with relatively low cost. The code was made to design five repeated compressor stages on two steps conducted iteratively, namely 'mean line and radial design' to determine the optimum compressor geometry and then the 'off-design' to test the stability of the design in other working conditions. The optimization tool minimizes a flexible cost function which can be changed if needed to get different designs. A certain
Supervised fuzzy C-means techniques to solve the capacitated vehicle routing problem
Fuzzy C-Means (FCM) clustering technique is among the most effective partitional clustering algorithms available in the literature. The Capacitated Vehicle Routing Problem (CVRP) is an important industrial logistics and managerial NP-hard problem. Cluster-First Route-Second Method (CFRS) is one of the efficient techniques used to solve CVRP. In CFRS technique, customers are first divided into clusters in the first phase, then each cluster is solved independently as a Traveling Salesman Problem (TSP) in the second phase. This research is concerned with the clustering phase of CFRS, and TSP is
Improvement of structural efficiency in metals by the control of topological arrangements in ultrafine and coarse grains
Improvement of structural efficiency in various materials is critically important for sustainable society development and the efficient use of natural resources. Recently, a lot of attention in science and engineering has been attracted to heterogeneous-structure materials because of high structural efficiency. However, strategies for the efficient design of heterogenous structures are still in their infancy therefore demanding extensive exploration. In this work, two-dimensional finite-element models for pure nickel with bimodal distributions of grain sizes having ‘harmonic’ and ‘random’
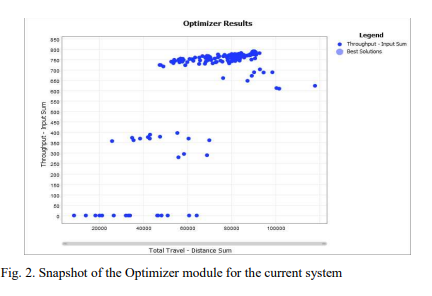
FlexSim Simulation to Enhance Productivity of a Production Cell : A Case Study
The use of modelling and simulation as a decision-making tool has increasingly been recognized to solve industrial problems. Modeling and simulation are utilized in this study to assess, analyze, and provide recommendations for improving the performance of an existing production cell in a manufacturing plant. To analyze the performance of the assembly line under investigation, multiple key performance indicators (KPIs) are determined. With the aid of FlexSim simulation tool, an improved system is recommended after running more than 90 different scenarios to enhance the productivity. The
Improving Productivity of A Production Line in Perfumes Industry in Egypt Using Lean Manufacturing Methodology
This study presents proposed solutions for increasing the productivity of a production line in the perfumes industry in Egypt using lean manufacturing methodology. Enhancing efficiency is a major significant objective to consider in a typical manufacturing firm to improve the overall performance. Increasing productivity is achieved through applying an extensive lean program implementing appropriate lean tools to solve problems identified as wastage in materials and activities as well as bottlenecks increasing lead time. Information of current problems and gaps are gathered through visits and
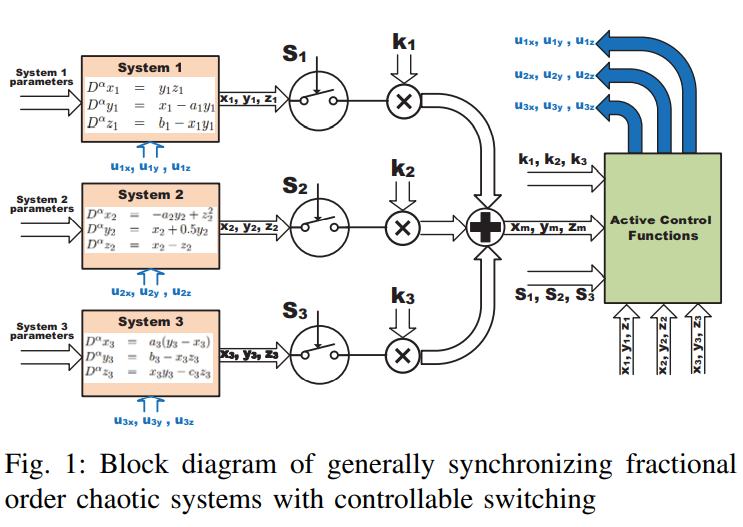
Switched active control synchronization of three fractional order chaotic systems
This paper discusses the continuous effect of fractional order parameter on two chaotic systems. Switched synchronization of three different fractional order chaotic systems is presented as an extension for synchronizing two different systems using active control. The proposed technique, which is based on the switching parameters and the scaling factors that control the choices of master and slave systems, is explained. The NonStandard Finite Difference method is used for the numerical solution of the fractional order master and slave systems. Four cases and many numeric simulations are
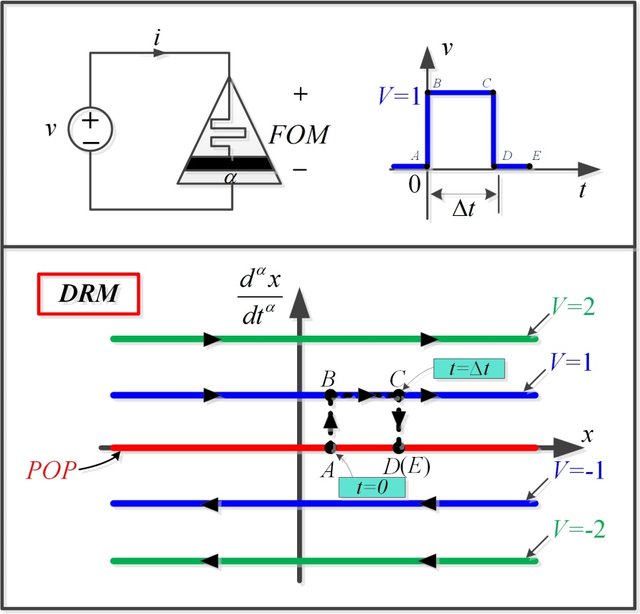
Multiple Pinch-Off Points in Memristive Equations: Analysis and Experiments
Pinched hysteresis behavior is considered evidence of the existence of the memristive element. Recently, the multi-lobes (more than two) behavior has been discovered in some memristive devices. In this paper, a fractional-order flux/voltage-controlled memristive model is introduced that is able to develop multiple symmetric and asymmetric pinch-off points. Generalized closed-form expressions for the necessary conditions of multiple pinch-off points existence are derived in addition to the coordinates of the pinch-off points in the I-V plane. Closed-form expressions for the minimum and maximum
Pagination
- Previous page ‹‹
- Page 10
- Next page ››
