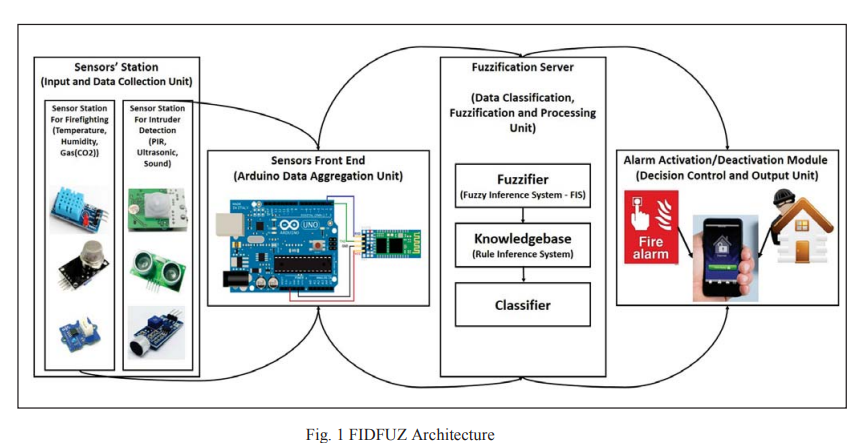
Design and implementation of robust firefighting/intruder detection system using fuzzy logic decision control (FIDFUZ)
This research focuses on using quantifiable methods for using the IoT as a main support to firefighting/intruder detection. From our research, we have found numerous researches associated to supplying remote services by means of portable sensors and communication technologies. We represent in our research a unique Smart Firefighting/lntruder Detection System with the support of Fuzzy Logic Decision Control (FIDFUZ). The projected system has an innovative value which is the Fuzzy Logic Decision Support System application that deals with the predicted inaccuracy and the doubt in the sensor's
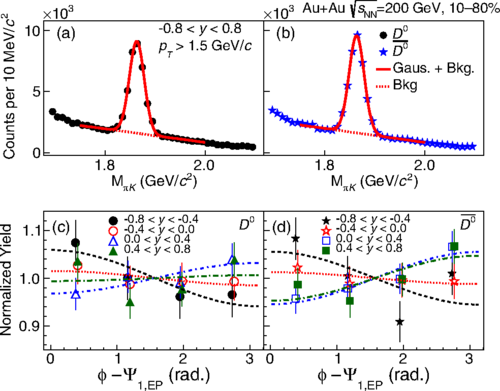
First Observation of the Directed Flow of D0 and D0 ̄ in Au+Au Collisions at sNN =200 GeV
We report the first measurement of rapidity-odd directed flow (v1) for D0 and D0̄ mesons at midrapidity (|y|
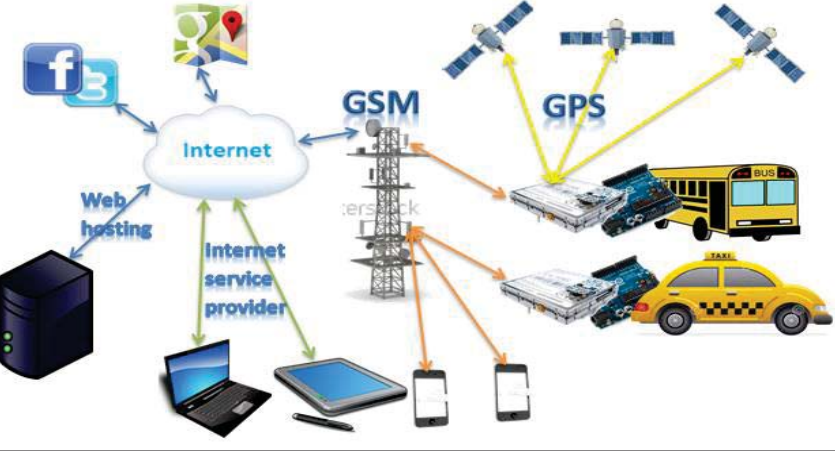
A Real-Time Social Network- Based Traffic Monitoring Vehicle Tracking System
Social networking has become an essential part of our daily lives. tTe integration of social networking communication model and Internet of Things (IoT) provides the users with a greater advantage than the benefit of using each one alone. This paper presents a real-time traffic monitoring and vehicle tracking for the public or private transportation sectors. The proposed system uses a social network service to provide traffic monitoring for individual users. A fully functional prototype model is developed and presented to demonstrate the system operation and to evaluate its performance. © 2018
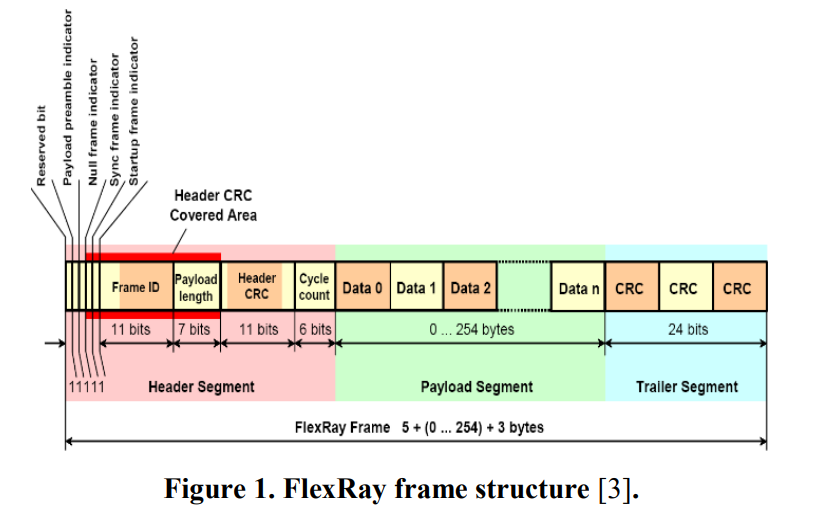
Lightweight authentication protocol deployment over FlexRay
In-vehicle network security is becoming a major concern for the automotive industry. Although there is significant research done in this area, there is still a significant gap between research and what is actually applied in practice. Controller area network (CAN) gains the most concern of community but little attention is given to FlexRay. Many signs indicate the approaching end of CAN usage and starting with other promising technologies. FlexRay is considered one of the main players in the near future. We believe that migration era is near enough to change our mindset in order to supply
SAODV and modified SAODV performance comparison
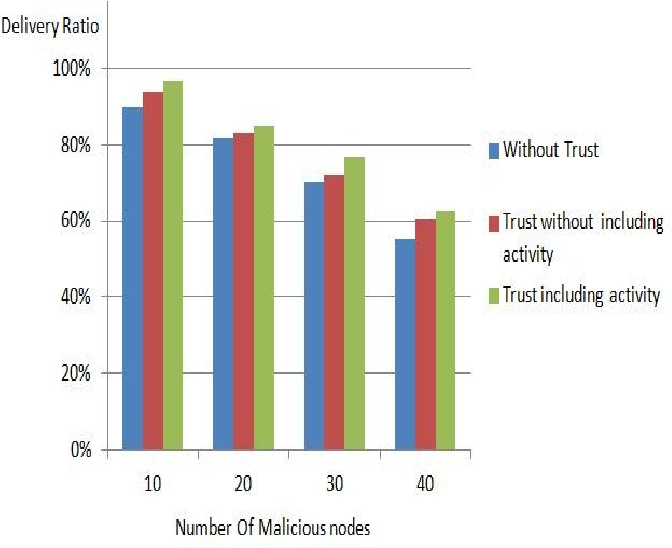
Routing plays a vital role in ad hoc networks and Ad hoc On-demand Distance Vector (AODV) protocol is considered one of the most famous routing protocols in ad hoc networks. Unfortunately it doesn't specify security measures. This has motivated the researchers to design secured version of AODV. However Security always collides with performance. The higher the security level is, the lower the performance level. This paper presents a performance comparison between Secure AODV (SAODV) and Modified SAODV (MSAODV). © 2013 IEEE.
A novel proximity based trust model for opportunistic networks
Trust should be earned. This is a famous quote that we use everyday implicitly or explicitly. Trust often is an inherent characteristic of our daily life, but in the digital community and between devices how can we represent trust? Since our mobile and digital devices became our confidants, we cannot share the information embedded in these devices with other devices without establishing trust. Hence, in this research a proximity based trust model based on Homophily principle is proposed. Earlier social studies have shown that people tend to have similarities with others in close proximity. In
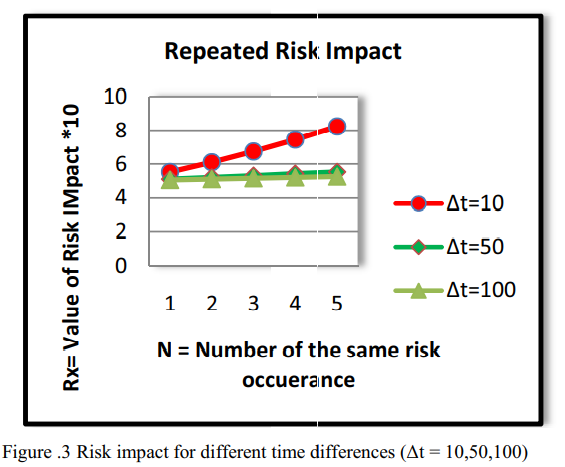
Organizational risk assessment based on attacks repetition
Risk assessment is a very critical and important process to protect the organization assets and reputation against security threats and risks. It provides a clear picture of the current threats that the organization is facing and helps the top management to take the right decision to eliminate or mitigate those risks. Usually if the vulnerability is exploited, the same attack may be happen twice or more in a different time periods because the vulnerability has been exploited and not mitigated. In this paper, we are illustrating our observation of the relation between the risk value and the
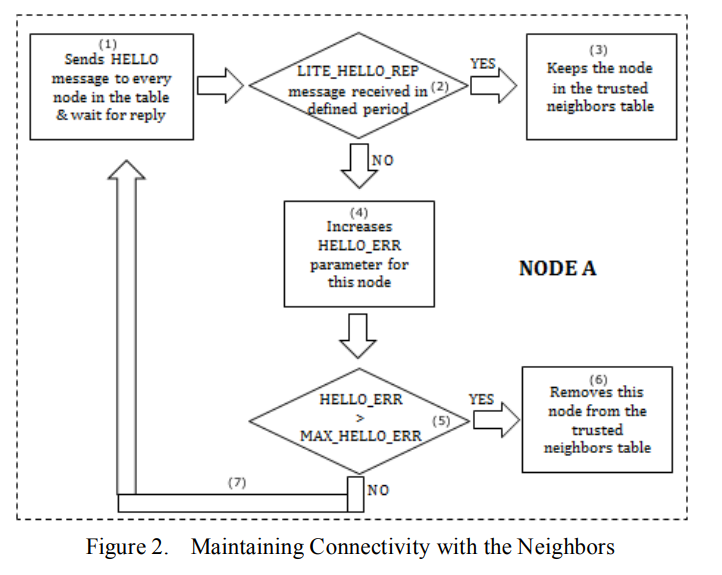
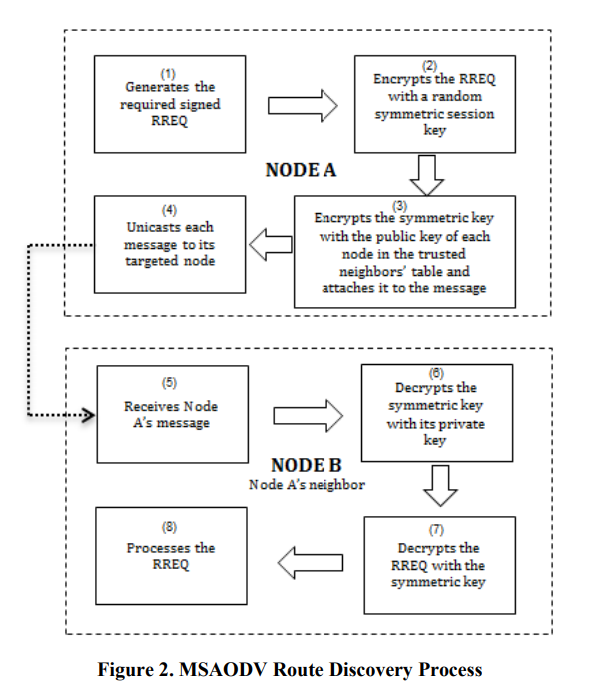
Immunizing the SAODV protocol against routing information disclosure
Secure routing protocols presents one of the most important challenges of Mobile Ad hoc Networks (MANETs). This is due to their special characteristics such as shared wireless medium, stringent resource constraints and highly dynamic network topology. This paper presents a solution to the problem of routing information disclosure and traffic analysis in a new way that doesn't require exchanging a group secret key between one-hop neighbors. In addition, the proposed solution maintains the routing data integrity and node authentication features. Furthermore, the solution provides a new method
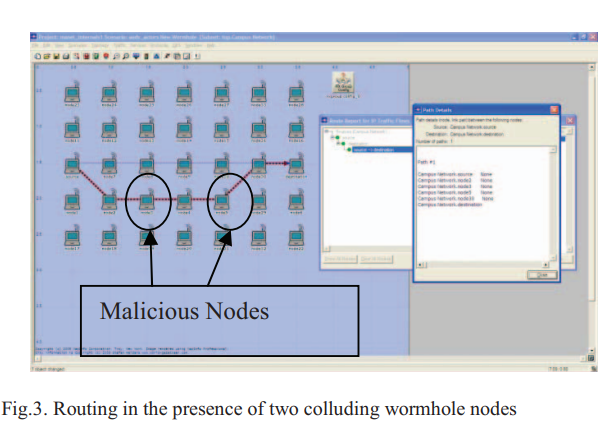
An innovative approach for the wormhole attack detection and prevention in wireless ad hoc networks
Due to their diverse applications, ad hoc networks are appealing for use in many domains. However, their features of open medium, absence of infrastructure, dynamic changing network topology, cooperative algorithms, lack of centralized monitoring and management point, resource constraints and lack of a clear line of defense, they are vulnerable to many attacks. Therefore, there is a major concern about their security. Amongst attacks we are particularly interested in a severe attack called the wormhole attack. In this paper, we propose a scheme for the wormhole attack detection and prevention
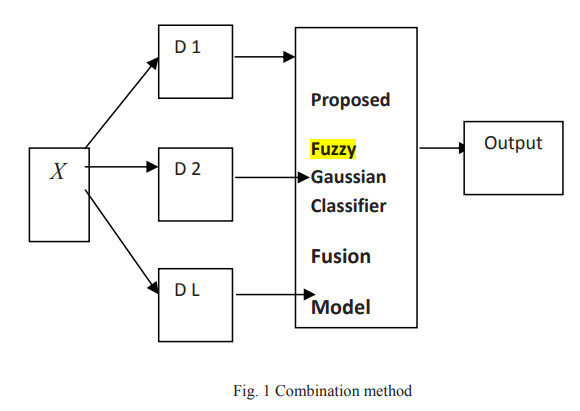
Fuzzy gaussian classifier for combining multiple learners
In the field of pattern recognition multiple classifier systems based on the combination of outputs from different classifiers have been proposed as a method of high performance classification systems. The objective of this work is to develop a fuzzy Gaussian classifier for combining multiple learners, we use a fuzzy Gaussian model to combine the outputs obtained from K-nearest neighbor classifier (KNN), Fuzzy K-nearest neighbor classifier and Multi-layer Perceptron (MLP) and then compare the results with Fuzzy Integral, Decision Templates, Weighted Majority, Majority Naïve Bayes, Maximum
Pagination
- Previous page ‹‹
- Page 35
- Next page ››
