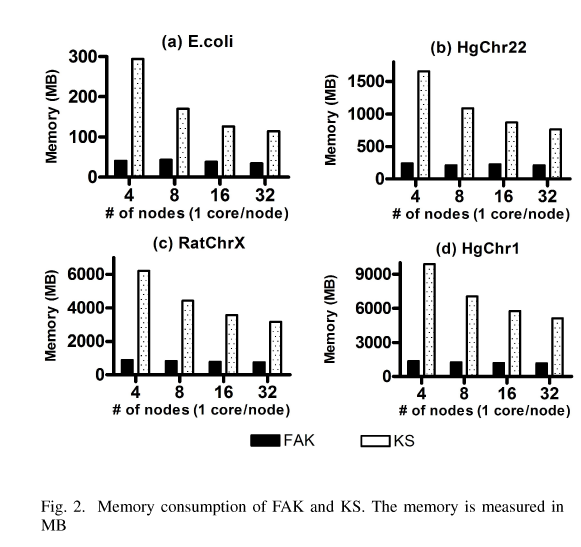
Dyadchurn: Customer churn prediction using strong social ties
The increase in mobile phone subscriptions in recent years, has led to near market saturation in the telecom industry. As a result, it has become harder for telecom providers to acquire new customers, and the need for retaining existing ones has become of paramount importance. Because of fierce competition between different telecom providers and because the ease of which customers can move from one provider to another, all telecom service providers suffer from customer churn. In this paper, we propose a dyadic based churn prediction model, DyadChurn, where customer churn is modeled through
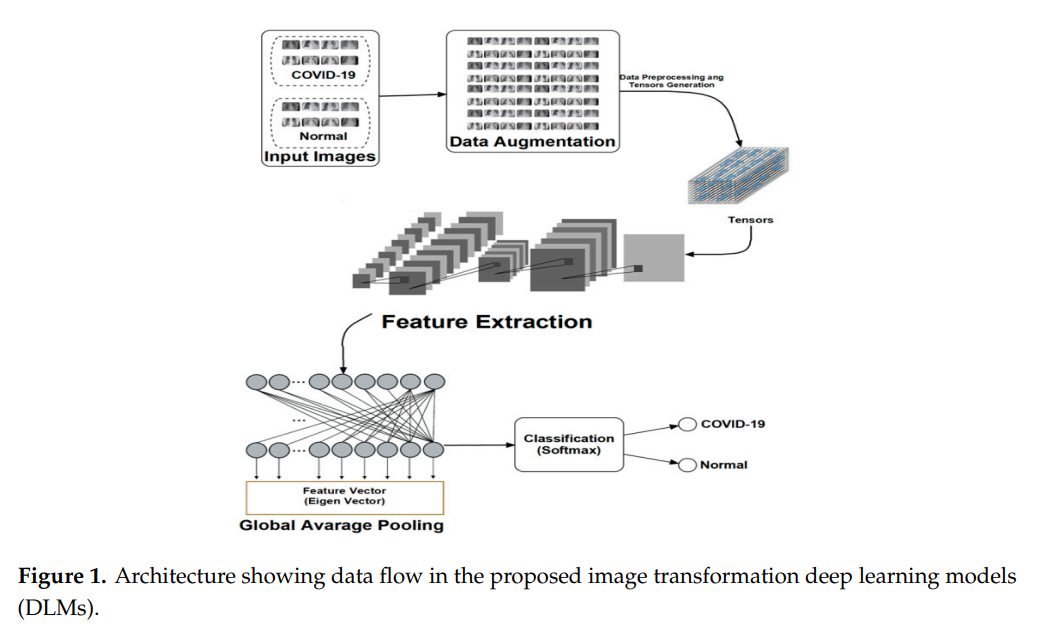
Deploying machine and deep learning models for efficient data-augmented detection of COVID-19 infections
This generation faces existential threats because of the global assault of the novel Corona virus 2019 (i.e., COVID-19). With more than thirteen million infected and nearly 600000 fatalities in 188 countries/regions, COVID-19 is the worst calamity since the World War II. These misfortunes are traced to various reasons, including late detection of latent or asymptomatic carriers, migration, and inadequate isolation of infected people. This makes detection, containment, and mitigation global priorities to contain exposure via quarantine, lockdowns, work/stay at home, and social distancing that
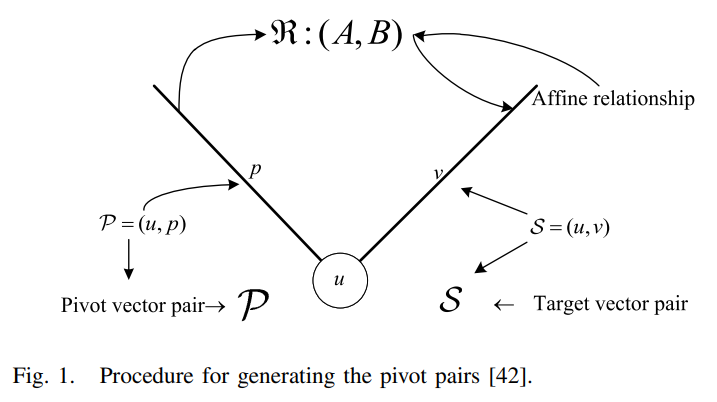
Dominant Data Set Selection Algorithms for Electricity Consumption Time-Series Data Analysis Based on Affine Transformation
In the explosive growth of time-series data (TSD), the scale of TSD suggests that the scale and capability of many Internet of Things (IoT)-based applications has already been exceeded. Moreover, redundancy persists in TSD due to the correlation between information acquired via different sources. In this article, we propose a cohort of dominant data set selection algorithms for electricity consumption TSD with a focus on discriminating the dominant data set that is a small data set but capable of representing the kernel information carried by TSD with an arbitrarily small error rate less than
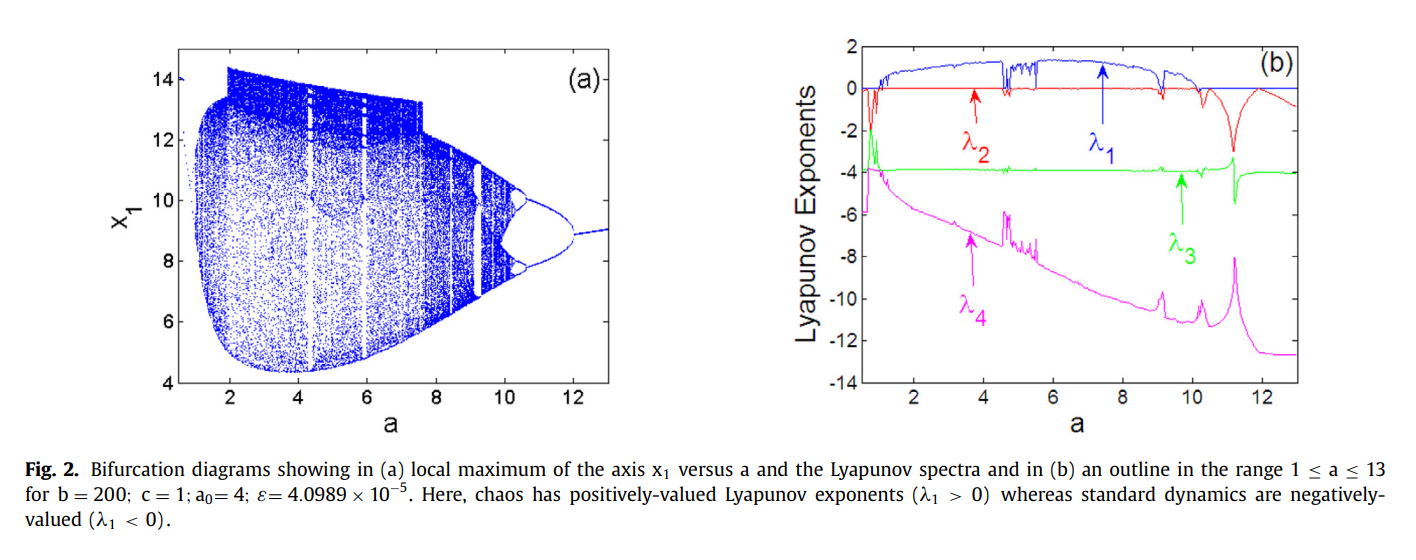
Design and implementation of a simple dynamical 4-D chaotic circuit with applications in image encryption
We present a simple yet highly dimensional hybrid diode bridge circuit network that can exhibit complex chaotic behaviours. Further, since our network is characterised by smooth fourth-order exponential nonlinearity, we employ a distinctive approach to assess its different properties: we examine the circuit stability near fixed points. Specifically, we evaluate dynamic complexity using the Lyaponov spectrum analysis, bifurcation analysis and phase space trajectories; additionally, we assess coexisting attractors in the parameter space using numerical and experimental analysis. Furthermore, we
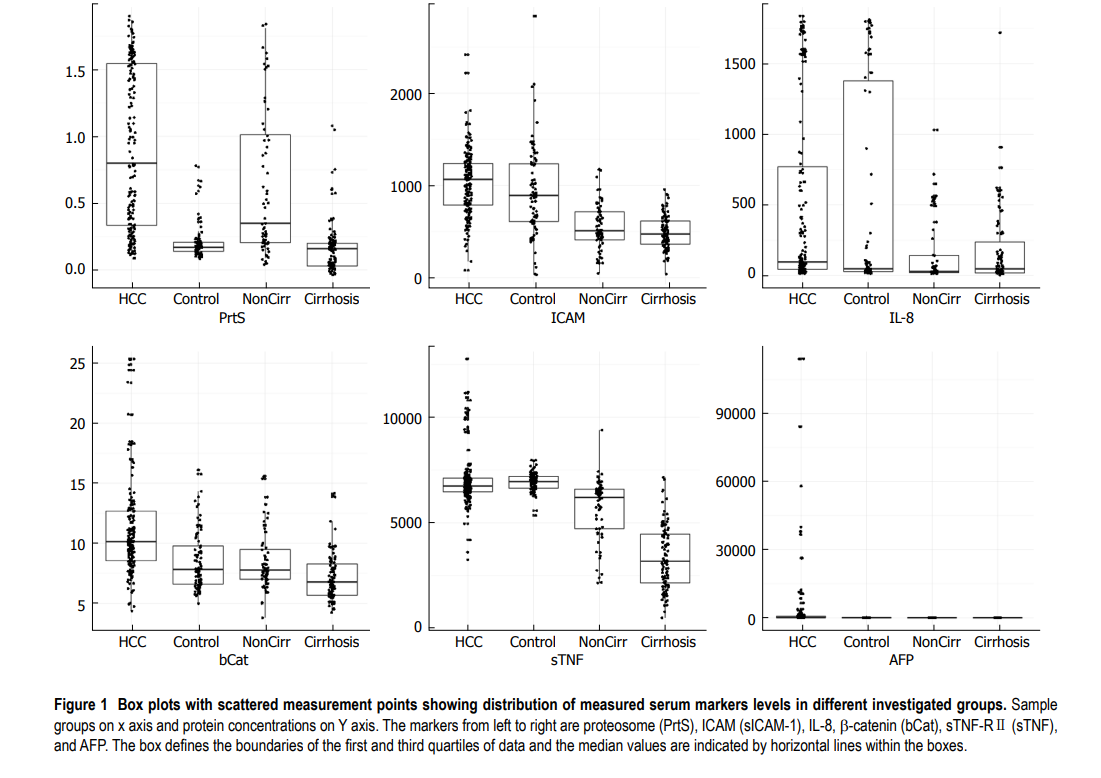
Early detection of hepatocellular carcinoma co-occurring with hepatitis C virus infection: A mathematical model
AIM: To develop a mathematical model for the early detection of hepatocellular carcinoma (HCC) with a panel of serum proteins in combination with α-fetoprotein (AFP). METHODS: Serum levels of interleukin (IL)-8, soluble intercellular adhesion molecule-1 (sICAM-1), soluble tumor necrosis factor receptor II (sTNF-R II), proteasome, and β-catenin were measured in 479 subjects categorized into four groups: (1) HCC concurrent with hepatitis C virus (HCV) infection (n = 192); (2) HCV related liver cirrhosis (LC) (n = 96); (3) Chronic hepatitis C (CHC) (n = 96); and (4) Healthy controls (n = 95). The
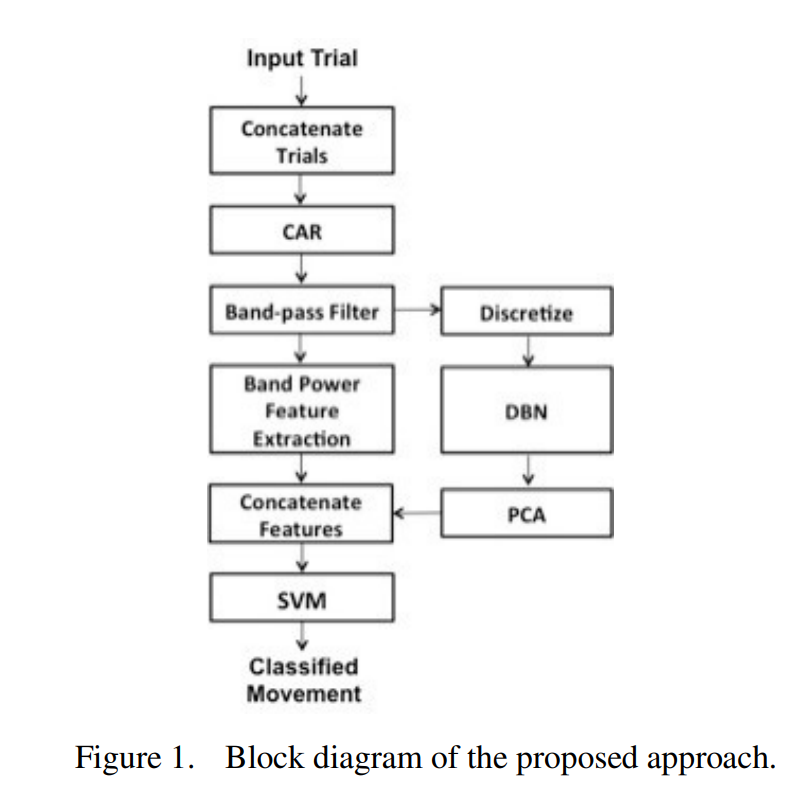
Dynamic Bayesian Networks for EEG motor imagery feature extraction
Dynamic Bayesian Networks (DBNs) are efficient graphical tools that could be used to detect causal relationships in multivariate systems. Here, we utilize DBNs to infer causality among electroencephalography (EEG) electrodes during a motor imagery task. We inferred the causal relationships between EEG electrodes during each of right and left hands imagery movements from 9 different subjects. We demonstrate how using the inferred connectivity as a feature enhances the discrimination among right and left hands imagery movements compared to using traditional band power features. Our analysis
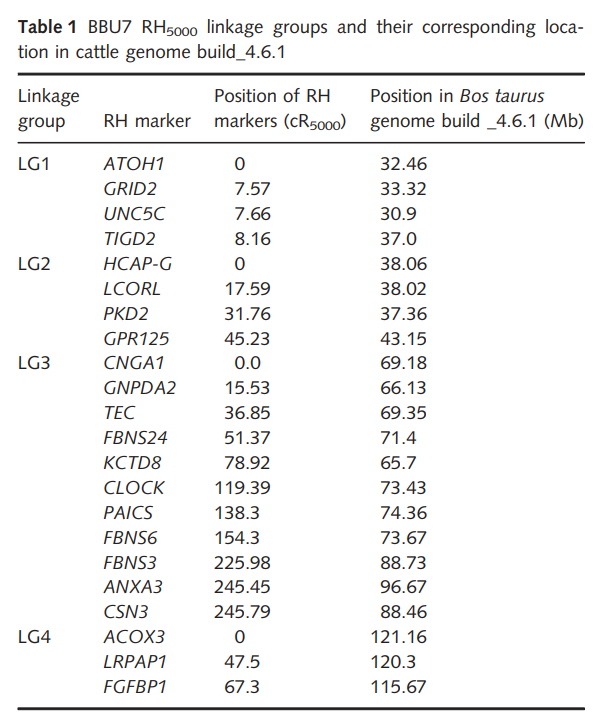
Radiation hybrid map of buffalo chromosome 7 detects a telomeric inversion compared to cattle chromosome 6
[No abstract available]
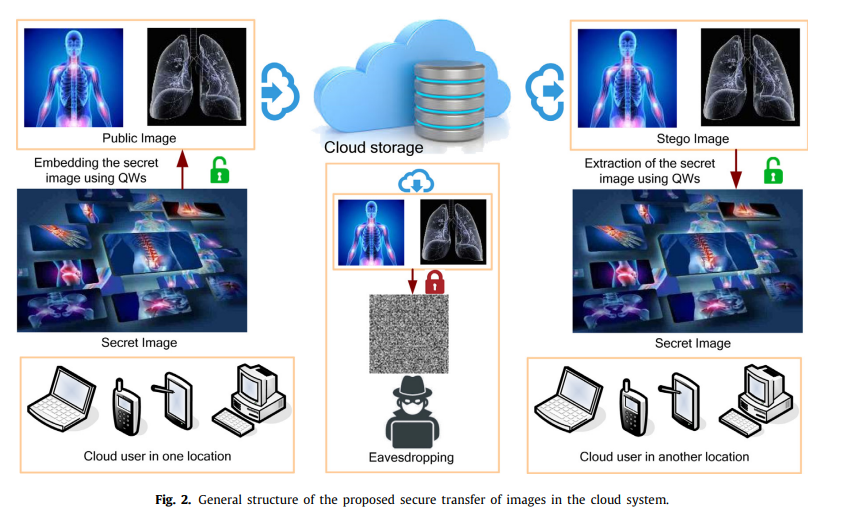
Secret images transfer in cloud system based on investigating quantum walks in steganography approaches
The central role of the cloud data warehouse is to ensure the security of confidential data that can be achieved via techniques of steganography and cryptography. Amidst the growth of quantum computation, modern data security tools may be cracked because of its structure based on mathematical computations. Quantum walk (QW) acts as a vital role in designing quantum algorithms, which is a universal computational model. Therefore, we allocate the advantages of QWs to design a QWs-based novel image steganography mechanism for cloud systems, which the embedding/extraction process for the secret

Open issues in the sentiment analysis of Arabic social media: A case study
With the rapid increase in the volume of Arabic opinionated posts on different microblogging mediums comes an increasing demand for Arabic sentiment analysis tools. Yet, research in the area of Arabic sentiment analysis is progressing at a very slow pace compared to that being carried out in English and other languages. This paper highlights the major problems and open research issues that face sentiment analysis of Arabic social media. The paper also presents a case study the goal of which is to investigate the possibility of determining the semantic orientation of Arabic Egyptian tweets and
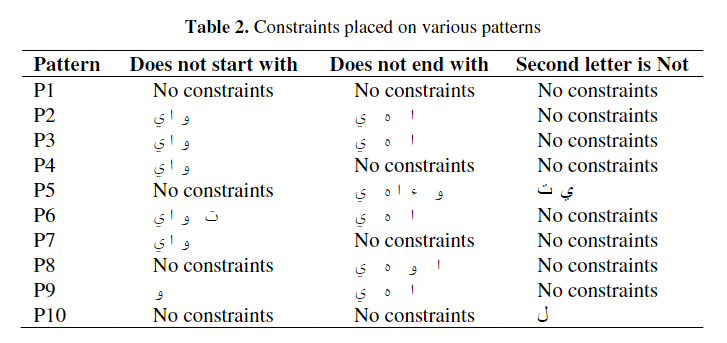
A corpus based approach for the automatic creation of Arabic broken plural dictionaries
Research has shown that Arabic broken plurals constitute approximately 10% of the content of Arabic texts. Detecting Arabic broken plurals and mapping them to their singular forms is a task that can greatly affect the performance of information retrieval, annotation or tagging tasks, and many other text mining applications. It has been reported that the most effective way of detecting broken plurals is through the use of dictionaries. However, if the target domain is a specialized one, or one for which there are no such dictionaries, building those manually becomes a tiresome, not to mention
Pagination
- Previous page ‹‹
- Page 33
- Next page ››
