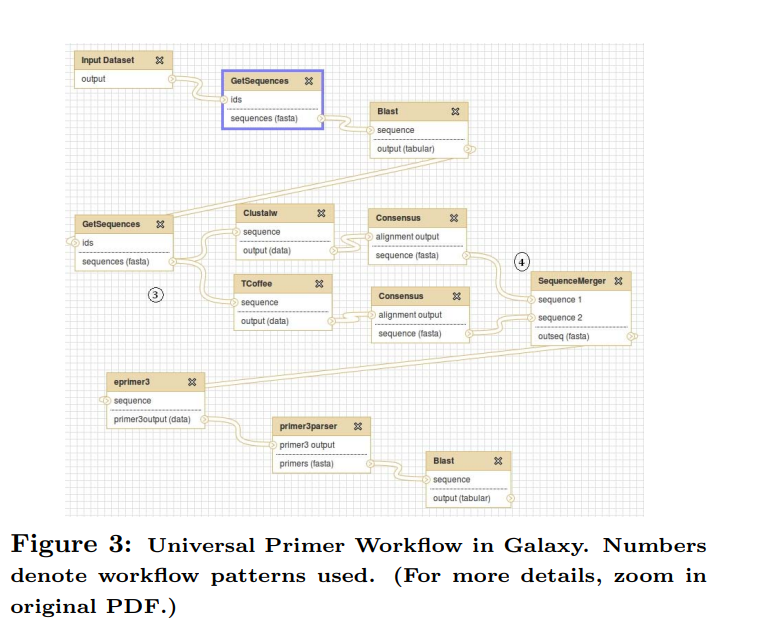
Meta-workflows: Pattern-based interoperability between Galaxy and Taverna
Taverna and Galaxy are two workflow systems developed specifically for bioinformatics applications. For sequence analysis applications, some tasks can be implemented easily on one system but would be difficult, or infeasible, to be implemented on the other. One solution to overcome this situation is to combine both tools in a unified framework that seamlessly makes use of the best features of each tool. In this paper, we present the architecture and implementation of a high-level system that provides such a solution. Our approach is based on meta-workflows and workflow patterns. We present a
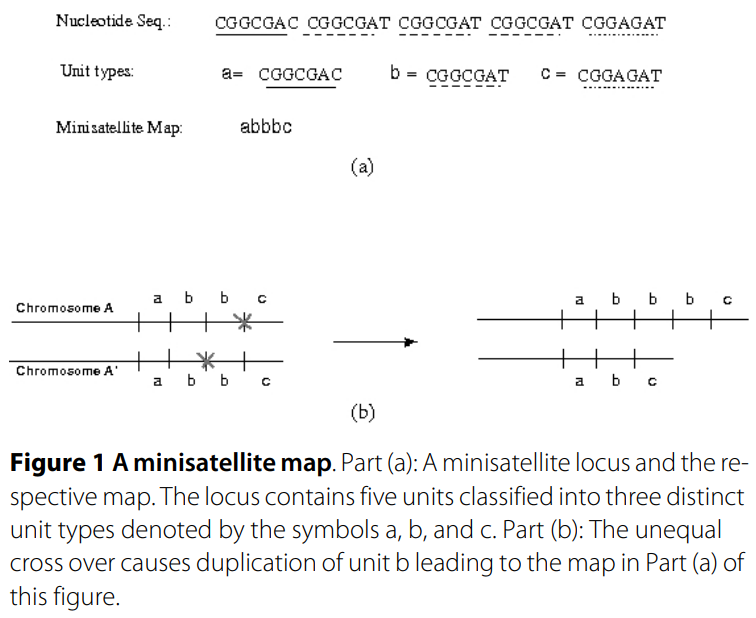
WAMI: A web server for the analysis of minisatellite maps
Background. Minisatellites are genomic loci composed of tandem arrays of short repetitive DNA segments. A minisatellite map is a sequence of symbols that represents the tandem repeat array such that the set of symbols is in one-to-one correspondence with the set of distinct repeats. Due to variations in repeat type and organization as well as copy number, the minisatellite maps have been widely used in forensic and population studies. In either domain, researchers need to compare the set of maps to each other, to build phylogenetic trees, to spot structural variations, and to study duplication
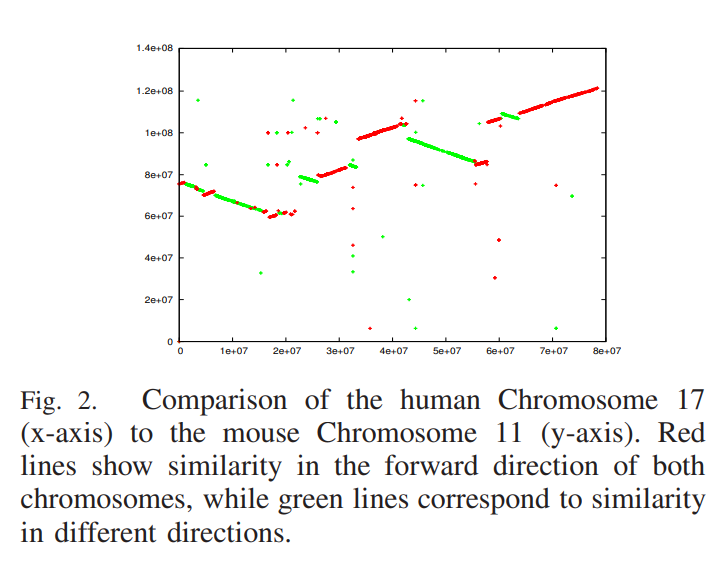
WinBioinfTools: Bioinformatics tools for windows cluster
Open source bioinformatics tools running under MS Windows are rare to find, and those running underWindows HPC cluster are almost nonexisting, in spite of the fact that Windows is the most popular operating system. Therefore, we introduce WinBioinfTools, an open source toolkit containing a number of bioinformatics tools running under Windows High Performance Computing Server 2008. The current version contains three programs for biological sequence analysis: 1) CoCoNUT for pairwise genome comparison, 2) WinBLAST for biological database search, and 3) WinPSA for global pairwise sequence
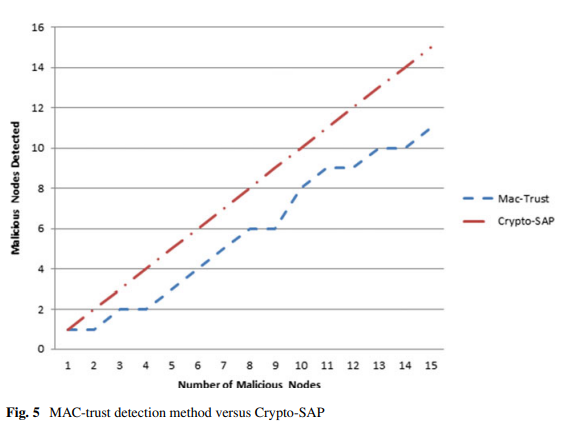
Crypto-SAP Protocol for Sybil Attack Prevention in VANETs
VANETs are considered as sub-category from MANETs. They provide the vehicles with the ability of communication among each other to guarantee safety and provide services for drivers. VANETs have many network vulnerabilities like: Working on wireless media makes it vulnerable to many kinds of attacks and nodes can join or leave the network dynamically making change in its topology which affects communication links stability. In VANETs, each car works as a node and router, so if a malicious attacker joins the network, the attacker could send false messages to disrupt the network operation and
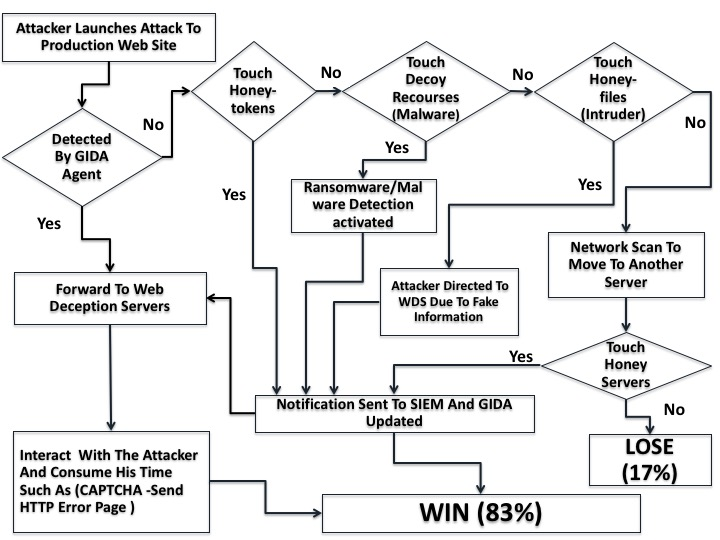
A New Web Deception System Framework
Web applications have many vulnerabilities that allow attackers to compromise sensitive data and gain unauthorized access to the production web servers. Compromised web-sessions represent a major threat. Current random attacks draw attention to the need for new protection and detection tools. In this paper, we propose a web deception scheme to mitigate web attacks in the production web site. The solution is more like a call for arms, using game theory, honeyweb, and honeytokens with ransomware and intrusion detection. The proposed scheme is explained in details as well as simulation results. ©
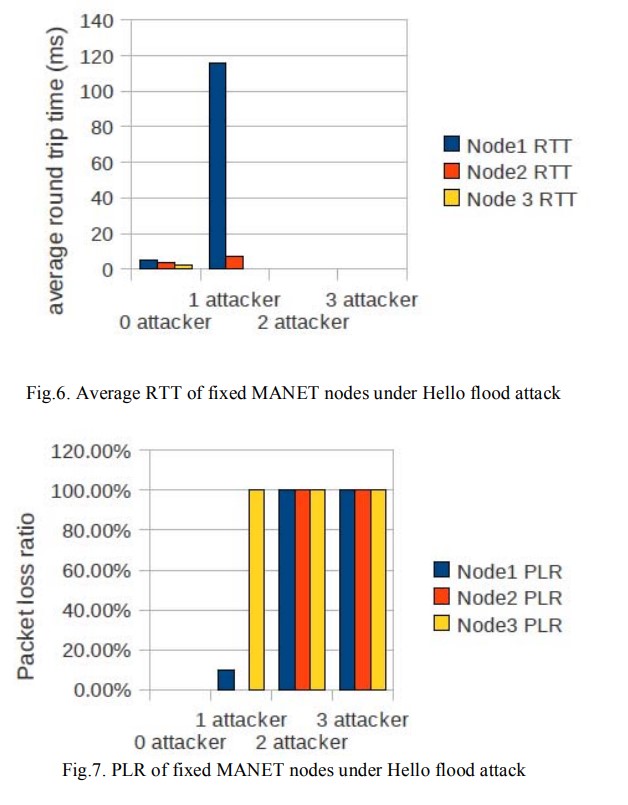
Performance evaluation of AODV under dos attacks
Mobile Ad-hoc Networks consist of a group of nodes with wireless connectivity forming a network without fixed infrastructure or centralized administration. Such networks are very dynamic due to nodes' mobility. This causes frequent unpredictable changes in topology, a characteristic that must be dealt with using special routing protocols. The Ad-hoc on Demand Distance Vector (AODV) is one of the most commonly used routing protocols, where nodes act as routers and routes are only provided on demand. In this paper, we evaluate the AODV's performance in the presence of two MANET attacks: Hello
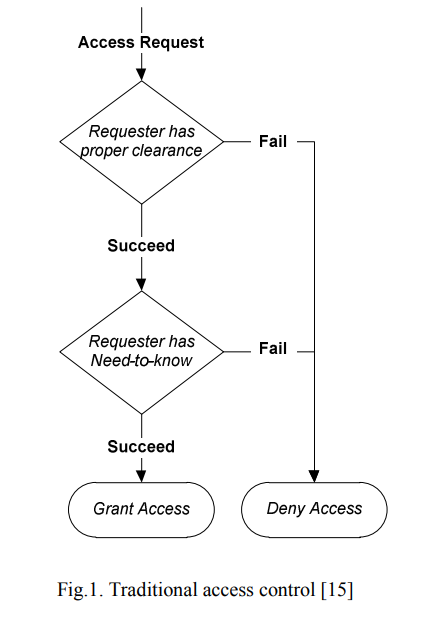
Security access control research trends
Information security policy is a critical property in any organization. For systems, the security policy addresses constraints on access by external systems and adversaries including programs and access to data by people. A continuous research effort is done throughout security policy aspects, such as policy procedures, documentation, policy enforcement, and administration. In this paper, we explore the research trends in an important component of security policies, which is access control. We survey the different modes of access controls, and identify the open research areas associated with
Preventing wormhole attack in wireless ad hoc networks using cost-based schemes
Ad hoc networks can be rapidly deployed and reconfigured. Hence, they are very appealing as they can be tailored to lots of applications. Due to their features, they are vulnerable to many attacks. A particularly severe security attack, called the wormhole attack, has been introduced in the context of ad-hoc networks. During the attack a malicious node captures packets from one location in the network, and tunnels them to another malicious node at a distant point, which replays them locally. In this paper we explain the wormhole attack modes and propose two schemes for the wormhole attack
Preventing wormhole attack in wireless ad hoc networks using cost-based schemes
Ad hoc networks can be rapidly deployed and reconfigured. Hence, they are very appealing as they can be tailored to lots of applications. Due to their features, they are vulnerable to many attacks. A particularly severe security attack, called the wormhole attack, has been introduced in the context of ad-hoc networks. During the attack a malicious node captures packets from one location in the network, and tunnels them to another malicious node at a distant point, which replays them locally. In this paper we explain the wormhole attack modes and propose two schemes for the wormhole attack
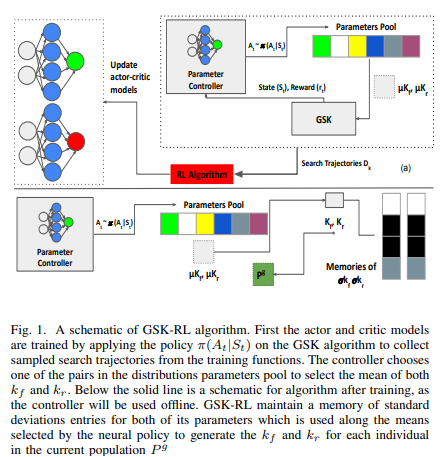
GSK-RL: Adaptive Gaining-sharing Knowledge algorithm using Reinforcement Learning
Meta-heuristics and nature inspired algorithms have been prominent solvers for highly complex, nonlinear and hard optimization problems. The Gaining-Sharing Knowledge algorithm (GSK) is a recently proposed nature-inspired algorithm, inspired by human and their tendency towards growth and gaining and sharing knowledge with others. The GSK algorithm have been applied to different optimization problems and proved robustness compared to other nature-inspired algorithms. The GSK algorithm has two main control parameters kfand kr which controls how much individuals gain and share knowledge with
Pagination
- Previous page ‹‹
- Page 30
- Next page ››
