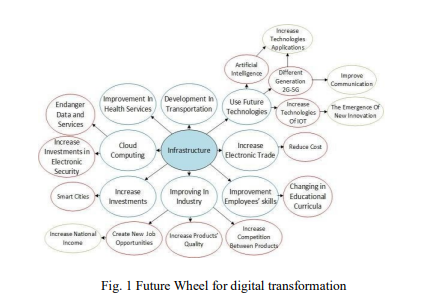
Impact of COVID-19 on Information Technology Sector in Egypt
Pandemics raise huge challenges yet brought several opportunities. The sudden attack of COVID-19 revealed the importance of the information technology (IT) applications. The Reliance on the IT sector has become imperative to ensure sustainability and to raise most sectors' performance efficiency, especially the services' ones. This study applied PESTEL analysis to evaluate the current status of IT in Egypt. SWOT analysis was performed to explore points of strength, weakness, opportunities, and threats that face the IT sector in Egypt as a result of the COVID19 attack. The process of foreseeing
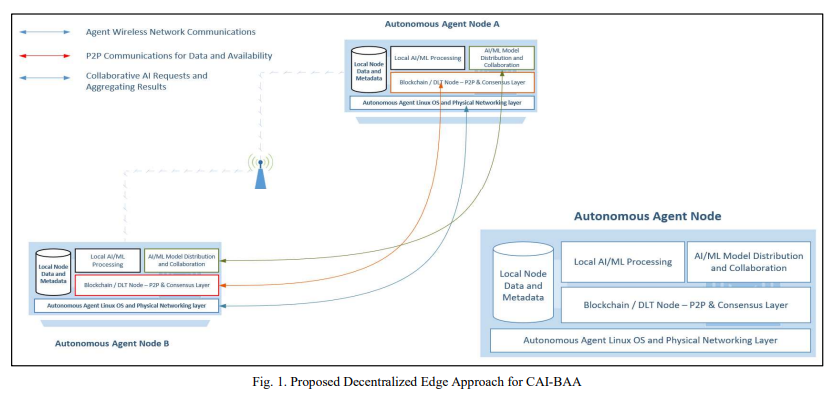
Modeling Collaborative AI for Dynamic Systems of Blockchain-ed Autonomous Agents
Artificial Intelligence has been strongly evolving disrupting almost every research and application domain. One of the key attributes - and at the same time an enabler - of today's innovations is the massive connectivity resulted in the opportunity to exploit Artificial Intelligence across distributed network of self-contained smart agents those could range from software bots to complex devices like autonomous vehicles, IoT collations, UAVs and Robot Swarms. Such heterogenous networks of Autonomous Agents could differ in size, networking topology, protocols, computing profiles, algorithms
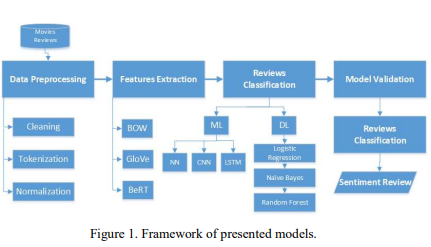
Sentiment Analysis using Machine Learning and Deep Learning Models on Movies Reviews
The huge amount of data being generated and transferred each day on the Internet leads to an increase of the need to automate knowledge-extraction tasks. Sentiment analysis is an ongoing research field in knowledge extraction that faces many challenges. In this paper, different machine learning, neural networks, deep learning models were evaluated over the IMDB benchmark dataset for movies reviews. Moreover, various word-embedding techniques were tested. Among all the presented models, the results of this work showed that the Long Short-Term Memory (LSTM) model with Bidirectional Encoder
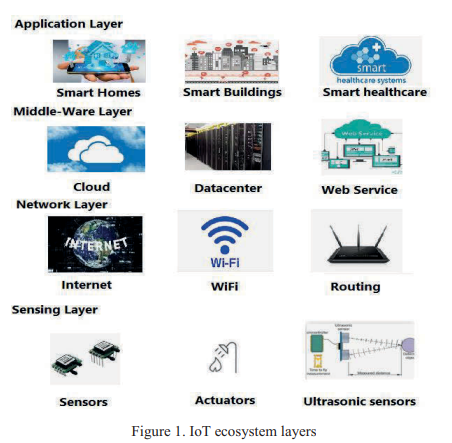
Mitigating IoT Security Challenges Using Blockchain
There is an increase in the usage of the Internet of Things (IoT) devices which focus on, efficiency and automation of different tasks to minimize the user intervention during COVID-19 pandemic. These IoT devices incur seamless excessive data exchange, Therefore, there is need for reinforcing the security, authentication and privacy to be more resilient to the various types of attacks which are the key concern for many organizations, especially cloud based networks carrying sensitive data. This paper presents a review of the challenges facing the IoT ecosystem along with the attack vectors
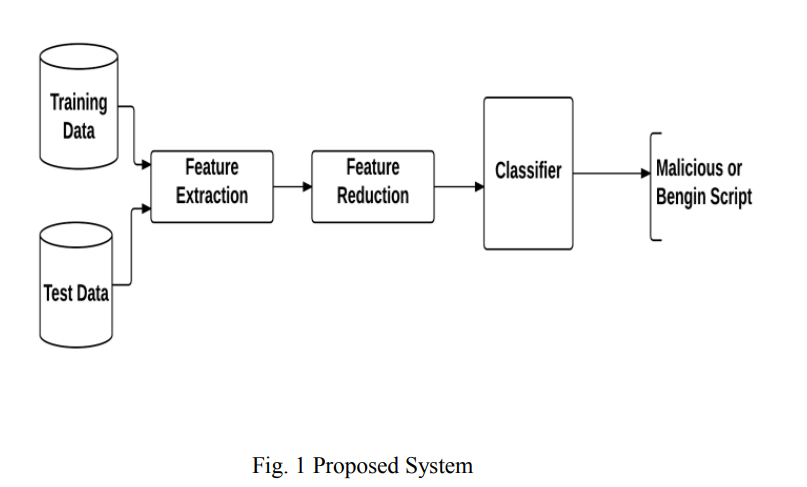
Malicious VBScript detection algorithm based on data-mining techniques
Malware attacks are amongst the most common security threats. Not only malware incidents are rapidly increasing, but also the attack methodologies are getting more complicated. Moreover malware writers expand in using different platforms and languages. This raises the need for new detection methods which support more reliable, low resource consuming and fast solutions. In this paper, a new algorithm has been proposed based on machine learning techniques and static analysis features to detect malicious scripts specifically for VBScript files. Experimental results show that the proposed
Correlation between protocol selection and packet drop attack severity in ad hoc networks
Mobile Ad hoc Network (MANET) are self-configuring, dynamic, networks that consist of nodes with various capabilities communicating through a wide spectrum of frequencies. Such flexibility in infrastructure and design comes with great risks in form of attacks on its nodes and the routing protocols that connect the network together. The aim of this paper is to explore the correlation between the attack severity and the protocol used. In this paper, the comparison will be mainly between the Dynamic Source Routing (DSR) protocol, and the Ad-Hoc On-Demand Distance Vector (AODV) protocol and how
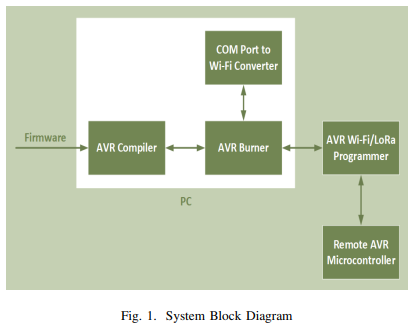
On Flashing over the Air 'FOTA' for IoT Appliances - An ATMEL Prototype
Wireless flashing over the air is a challenging task. Appliances are required to update its flash or EEPROM via a remote system update. However, direct connectivity via a wire is not available. Within the application of consumer electronics, such as utility meters or other appliances, there is always a room to update the appliance remotely for optimal operation. In this paper, we present a new system for remotely flashing all models of ATMEL AVR microcontrollers via Wi-Fi and LoRa technologies. Also, we will demonstrate an experimental work to prove our new methodology as well as applying it
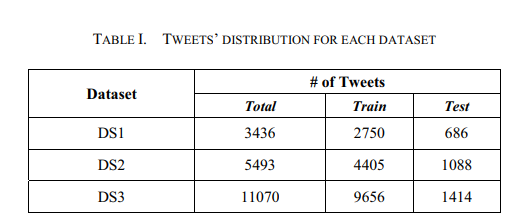
Which configuration works best? an experimental study on supervised Arabic twitter sentiment analysis
Arabic Twitter Sentiment Analysis has been gaining a lot of attention lately with supervised approaches being exploited widely. However, to date, there has not been an experimental study that examines how different configurations of the Bag of Words model, text representation scheme, can affect various supervised machine learning methods. The goal of the presented work is to do exactly that. Specifically, this work examines which configurations work best for each of three machine learning approaches that have shown good results when applied on the task of sentiment analysis, namely: Support

A collaborative resource to build consensus for automated left ventricular segmentation of cardiac MR images
A collaborative framework was initiated to establish a community resource of ground truth segmentations from cardiac MRI. Multi-site, multi-vendor cardiac MRI datasets comprising 95 patients (73 men, 22 women; mean age 62.73. ±. 11.24. years) with coronary artery disease and prior myocardial infarction, were randomly selected from data made available by the Cardiac Atlas Project ( Fonseca et al., 2011). Three semi- and two fully-automated raters segmented the left ventricular myocardium from short-axis cardiac MR images as part of a challenge introduced at the STACOM 2011 MICCAI workshop (
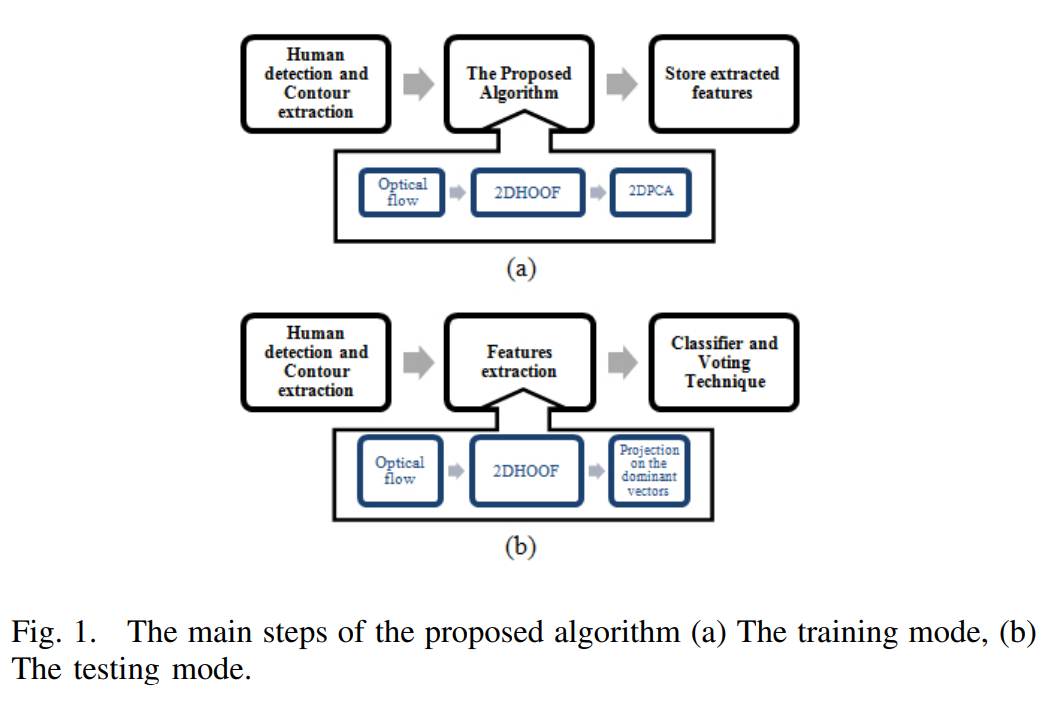
2DHOOF-2DPCA contour based optical flow algorithm for human activity recognition
A novel algorithm for human activity recognition is presented in this paper. This approach is based on a new 2D representation for the Histogram of Oriented Optical Flow (2DHOOF) describing the motion of the actor's contour, where one multi-layer 2D-histogram per video is constructed. Each histogram layer consists of 2D bins (layers) that represent different range of angles. Applying our 2DHOOF features descriptors on the actor's contour reduces the storage requirement and the computation complexity since a sparse optical flow is calculated instead of dense optical flow. In addition, it is
Pagination
- Previous page ‹‹
- Page 28
- Next page ››
