Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
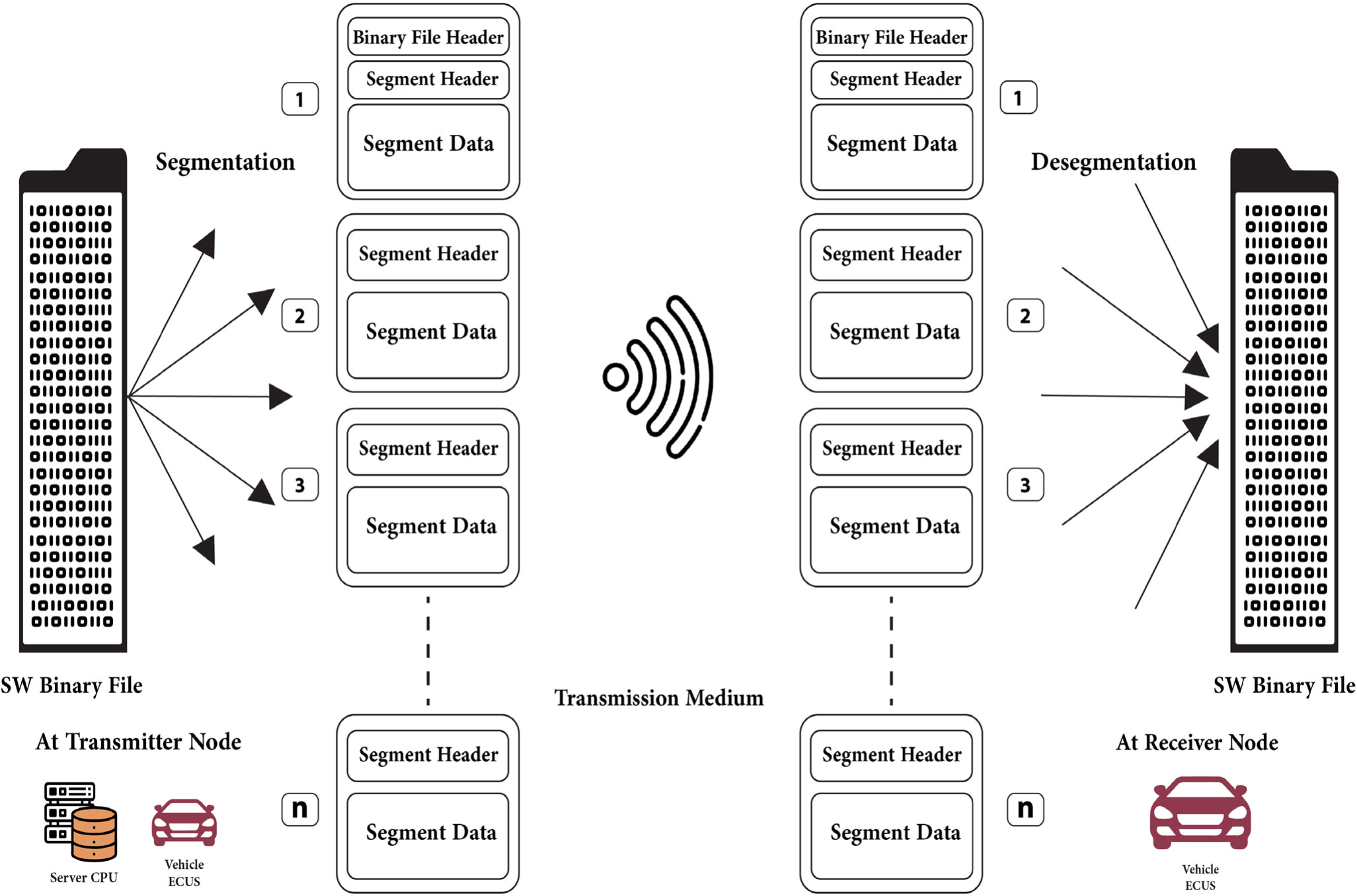
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
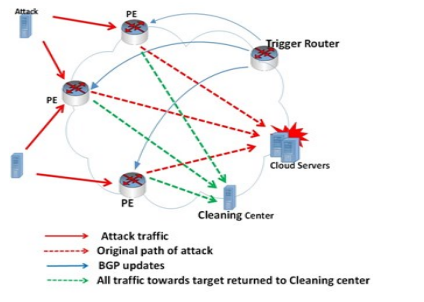
Detection and Countermeasures of DDoS Attacks in Cloud Computing
Greater portions of the world are moving to cloud computing because of its advantages However, due to its distributed nature, it can be easily exploited by Distributed Denial of Service (DDoS) attacks. In distributed DDoS attacks, legitimate users are prevented from using cloud resources. In this paper, the various DDoS detection and defenses mechanisms cloud computing are reviewed. We propose a new technique based on Remote Triggered Black Hole (RTBH) to prevent DDoS attacks before it target to cloud resources. © 2018 IEEE.
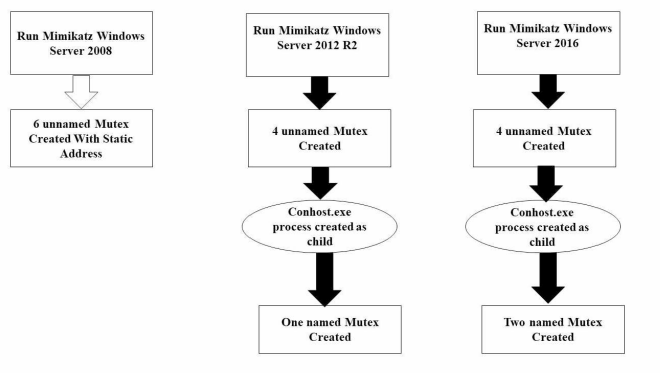
Detecting Mimikatz in Lateral Movements Using Mutex
Advanced Persistent Threat (APT) is a stealthy computer network attack. Its threat lies in the fact that unauthorized access to a network is gained and the attackers, whether a person or a group may remain undetected for an extended period. APT group can spread and gain access to the most valuable assets in the targeted organization. Depending on the tools used by APT group it can be hard and complex to respond to those groups and their tools. Mimikatz is one of the most powerful tools used by many APT groups, penetration testers and malware. In this paper, we focus on lateral movement and APT
Cooperation incentives in wireless ad hoc networks
Mobile ad hoc networks heavily rely on nodes' cooperation for packet forwarding. As a result, misbehaving, malicious, and selfish nodes can significantly degrade the performance of the network. To cope with this issue and to stimulate cooperation among selfish mobile nodes, a continuous research effort is done on identifying nodes trust and reputation. In this paper, we survey recently proposed reputation and incentive schemes for ad hoc networks. In order to help in the design of different reputation systems tailored to specific applications and network topologies, we classify the different
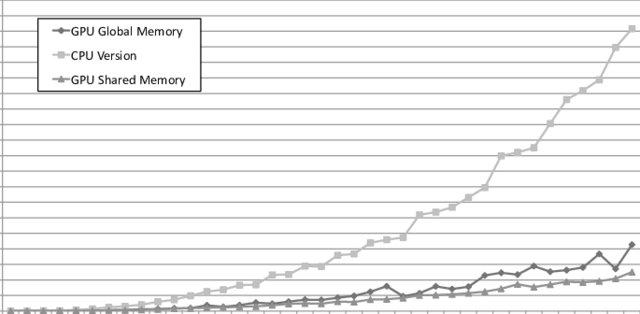
A GPU-enabled solver for time-constrained linear sum assignment problems
This paper deals with solving large instances of the Linear Sum Assignment Problems (LSAPs) under realtime constraints, using Graphical Processing Units (GPUs). The motivating scenario is an industrial application for P2P live streaming that is moderated by a central tracker that is periodically solving LSAP instances to optimize the connectivity of thousands of peers. However, our findings are generic enough to be applied in other contexts. Our main contribution is a parallel version of a heuristic algorithm called Deep Greedy Switching (DGS) on GPUs using the CUDA programming language. DGS
Transverse momentum spectra of strange hadrons within extensive and nonextensive statistics
Using generic (non)extensive statistics, in which the underlying system likely autonomously manifests its extensive and nonextensive statistical nature, we extract various fit parameters from the CMS experiment and compare these to the corresponding results obtained from Tsallis and Boltzmann statistics. The present study is designed to indicate the possible variations between the three types of statistical approaches and characterizes their dependence on collision energy, multiplicity, and size of the system of interest. We analyze the transverse momentum spectra pT of the strange hadrons Ks
Evaluation of Different Sarcasm Detection Models for Arabic News Headlines
Being sarcastic is to say something and to mean something else. Detecting sarcasm is key for social media analysis to differentiate between the two opposite polarities that an utterance may convey. Different techniques for detecting sarcasm are varying from rule-based models to Machine Learning and Deep Learning models. However, researchers tend to leverage Deep Learning in detecting sarcasm recently. On the other hand, the Arabic language has not witnessed much improvement in this research area. Bridging the gap in sarcasm detection of the Arabic language is the target behind this work. In
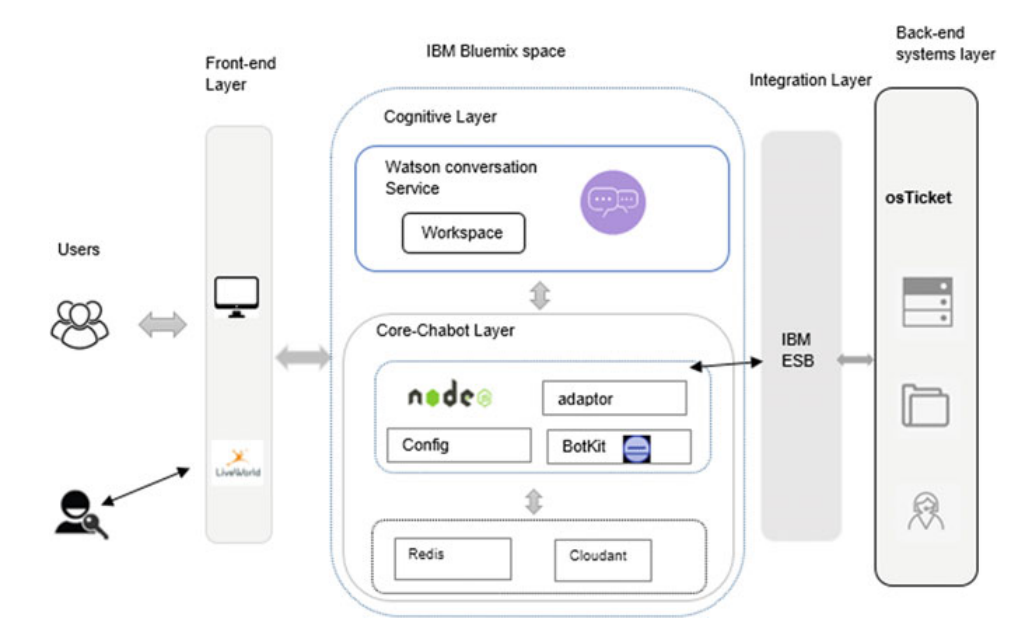
A study about using a cognitive agent in replacing level 1 and 2 service desk activities
The radical change in technology and high customer expectations and demand are pushing the service desk to provide a competent service for the customers. And this service should be faster, more flexible and gives a more accurate response and high user experience. Replacing the human call agent’s activities with a cognitive agent could improve the user experience by providing a faster response to customer’s requests, removing the human errors and giving 24/7 support with less operational cost. The cognitive agent has the potential to scale personalized and tailored interactions. And this will
Recognizing Clothing Patterns and Colors for BVI People Using Different Techniques
For blind and visually impaired (BVI) people, it is an arduous task to recognize clothing patterns and colors. It is especially complex to recognize them automatically. This is a highly researched area in image processing. This paper provides BVI with the ability to detect patterns and colors without depending on personal assistance, leading to increasing their confidence. The user first captures an image; then, our system detects colors and patterns. The color model used here is the hue saturation value (HSV). The main colors detected by our system are magenta, cyan, blue, green, red and
Pagination
- Previous page ‹‹
- Page 15
- Next page ››
