A fast algorithm for the multiple genome rearrangement problem with weighted reversals and transpositions
Background: Due to recent progress in genome sequencing, more and more data for phylogenetic reconstruction based on rearrangement distances between genomes become available. However, this phylogenetic reconstruction is a very challenging task. For the most simple distance measures (the breakpoint distance and the reversal distance), the problem is NP-hard even if one considers only three genomes. Results: In this paper, we present a new heuristic algorithm that directly constructs a phylogenetic tree w.r.t. the weighted reversal and transposition distance. Experimental results on previously
Constructing suffix array during decompression
The suffix array is an indexing data structure used in a wide range of applications in Bioinformatics. Biological DNA sequences are available to download from public servers in the form of compressed files, where the popular lossless compression program gzip [1] is employed. The straightforward method to construct the suffix array for this data involves decompressing the sequence file, storing it on disk, and then calling a suffix array construction program to build the suffix array. This scenario, albeit feasible, requires disk access and throws away valuable information in the compressed
Evaluating the Modsecurity Web Application Firewall against SQL Injection Attacks
SQL injection attacks target databases of web servers. The ability to modify, update, retrieve and delete database contents imposes a high risk on any website in different sectors. In this paper, we investigate the efforts done in the literature to detect and prevent the SQL injection attacks. We also assess the efficiency of the Modsecurity web application firewall in preventing SQL injection attacks. © 2020 IEEE.
Cooperation incentives in wireless ad hoc networks
Mobile ad hoc networks heavily rely on nodes' cooperation for packet forwarding. As a result, misbehaving, malicious, and selfish nodes can significantly degrade the performance of the network. To cope with this issue and to stimulate cooperation among selfish mobile nodes, a continuous research effort is done on identifying nodes trust and reputation. In this paper, we survey recently proposed reputation and incentive schemes for ad hoc networks. In order to help in the design of different reputation systems tailored to specific applications and network topologies, we classify the different
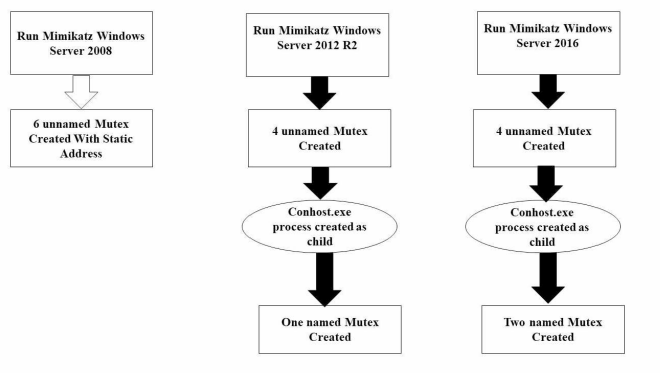
Detecting Mimikatz in Lateral Movements Using Mutex
Advanced Persistent Threat (APT) is a stealthy computer network attack. Its threat lies in the fact that unauthorized access to a network is gained and the attackers, whether a person or a group may remain undetected for an extended period. APT group can spread and gain access to the most valuable assets in the targeted organization. Depending on the tools used by APT group it can be hard and complex to respond to those groups and their tools. Mimikatz is one of the most powerful tools used by many APT groups, penetration testers and malware. In this paper, we focus on lateral movement and APT
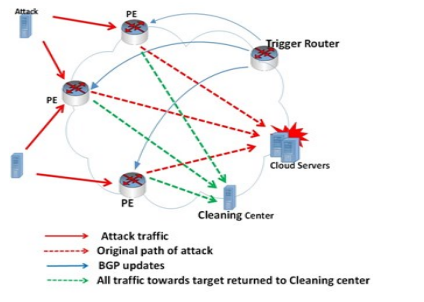
Detection and Countermeasures of DDoS Attacks in Cloud Computing
Greater portions of the world are moving to cloud computing because of its advantages However, due to its distributed nature, it can be easily exploited by Distributed Denial of Service (DDoS) attacks. In distributed DDoS attacks, legitimate users are prevented from using cloud resources. In this paper, the various DDoS detection and defenses mechanisms cloud computing are reviewed. We propose a new technique based on Remote Triggered Black Hole (RTBH) to prevent DDoS attacks before it target to cloud resources. © 2018 IEEE.
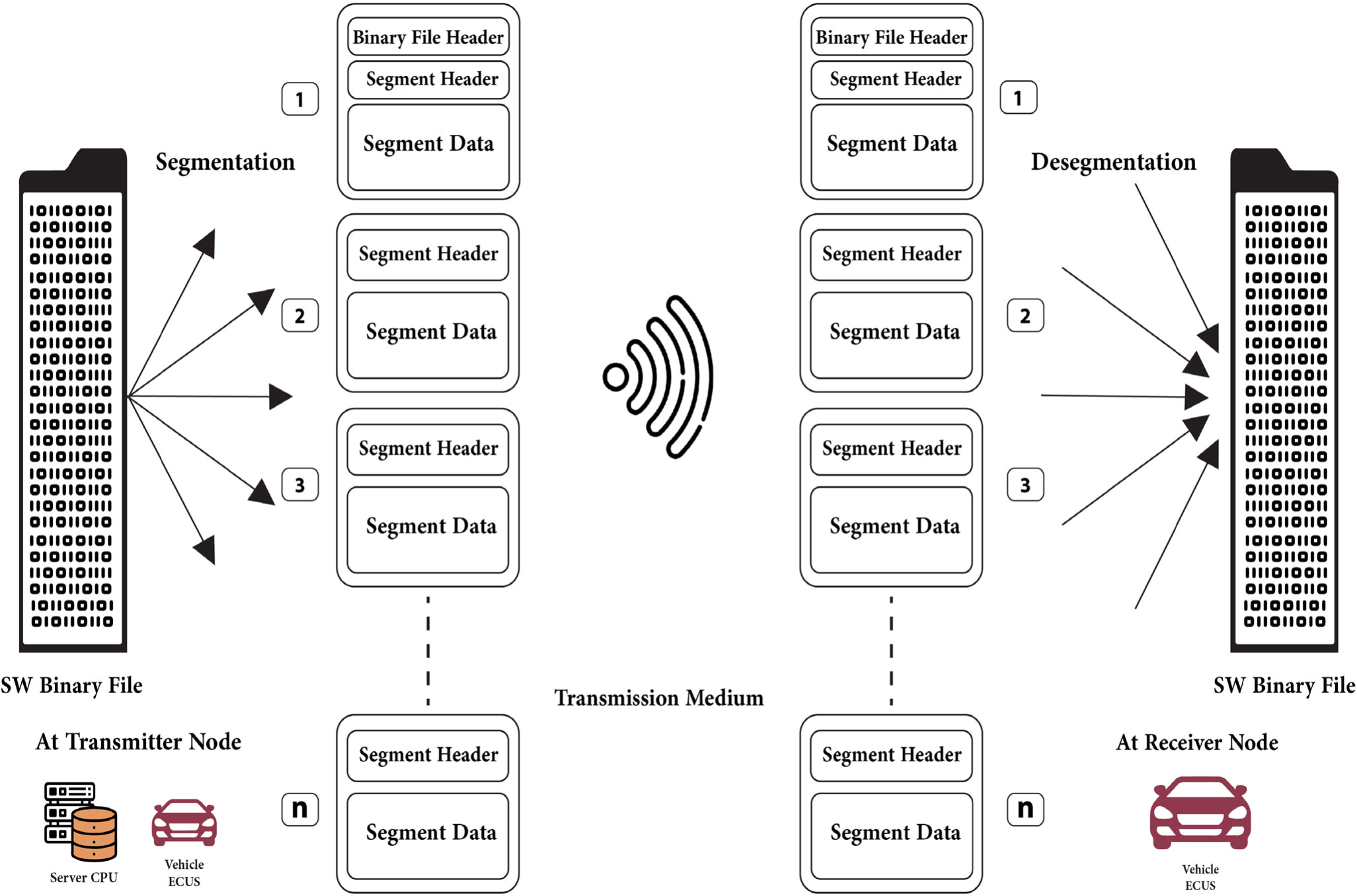
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
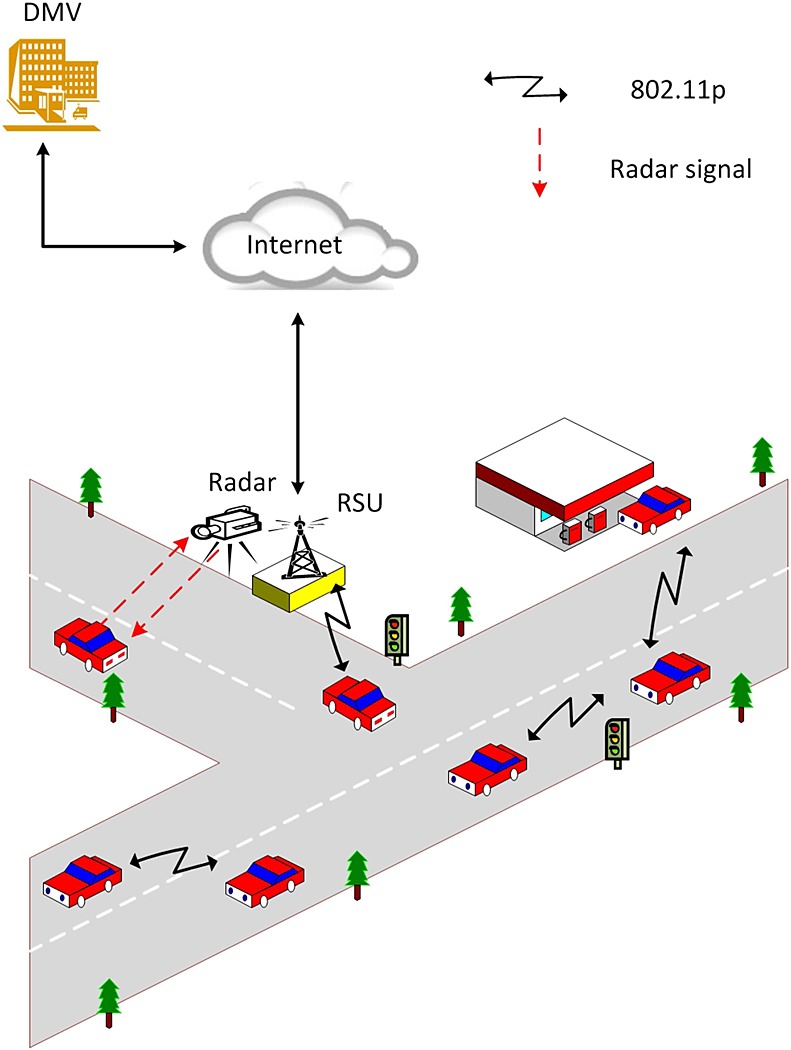
A secure and privacy-preserving event reporting scheme for vehicular Ad Hoc networks
In vehicular ad hoc networks, vehicles should report events to warn the drivers of unexpected hazards on the roads. While these reports can contribute to safer driving, vehicular ad hoc networks suffer from various security threats; a major one is Sybil attacks. In these attacks, an individual attacker can pretend as several vehicles that report a false event. In this paper, we propose a secure event-reporting scheme that is resilient to Sybil attacks and preserves the privacy of drivers. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the
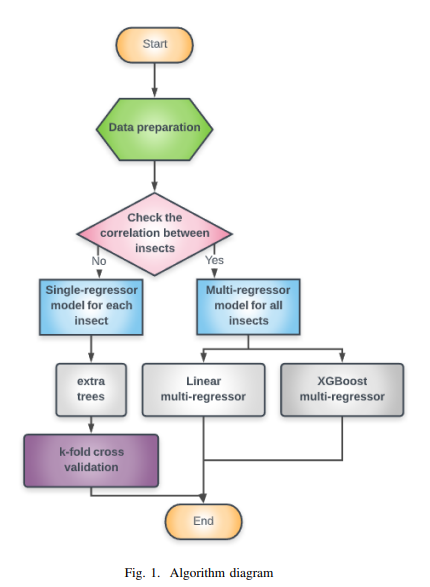
Guava Trees Disease Monitoring Using the Integration of Machine Learning and Predictive Analytics
The increase in population, food demand, and the pollution levels of the environment are considered major problems of this era. For these reasons, the traditional ways of farming are no longer suitable for early and accurate detection of biotic stress. Recently, precision agriculture has been extensively used as a potential solution for the aforementioned problems using high resolution optical sensors and data analysis methods that are able to cope with the resolution, size and complexity of the signals from these sensors. In this paper, several methods of machine learning have been utilized
Pagination
- Previous page ‹‹
- Page 14
- Next page ››
