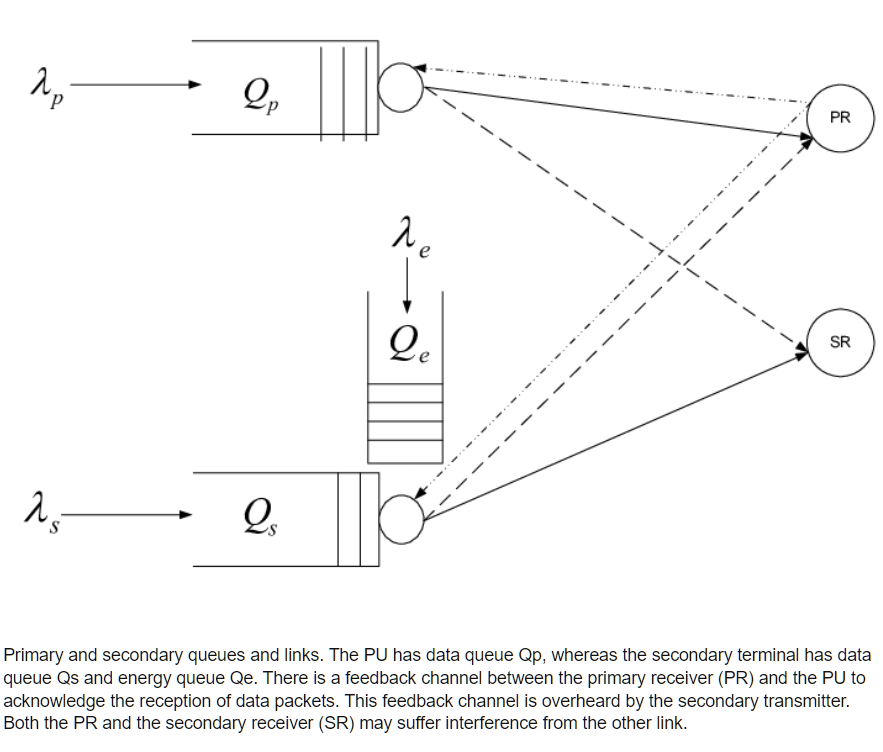
Optimal random access and random spectrum sensing for an energy harvesting cognitive radio
We consider a secondary user with energy harvesting capability. We design access schemes for the secondary user which incorporate random spectrum sensing and random access, and which make use of the primary automatic repeat request (ARQ) feedback. The sensing and access probabilities are obtained such that the secondary throughput is maximized under the constraints that both the primary and secondary queues are stable and that the primary queueing delay is kept lower than a specified value needed to guarantee a certain quality of service (QoS) for the primary user. We consider spectrum sensing
Geographic Routing with Cooperation for Reliable Paths in Device-to-Device Networks
In this paper, we introduce a novel geographic routing with cooperation scheme for 5G Device-to-Device ad hoc networks. The prime focus of our scheme (coined Cooperative Routing for Reliable Paths (CRRP)) is to enhance the routing performance in cooperative communication networks in terms of the path length and reliability. In particular, it introduces novel algorithms for cooperative relay and forwarder selections, which strike the best balance between path length and achieved symbol error rate, compared to prior work in the literature. Moreover, it exhibits the flexibility of deciding
Hierarchical proactive caching for vehicular ad hoc networks
Recently, emerging vehicular applications are increasing the demand of vehicles which form significant burdens on network backhaul and represents a cause to the quality of experience (QoE) decay of the vehicular users. Proactive caching is a promising technique to mitigate the load on core networks by caching some of the expected data items. This work proposes a hierarchical proactive caching scheme which jointly considers caching in vehicles and roadside units (RSUs). Minimization of the vehicle communication latency is the main objective of our study. The optimization problem is formulated
Transmission power adaptation for cognitive radios
In cognitive radio (CR) networks, determining the optimal transmission power for the secondary users (SU) is crucial to achieving the goal of maximizing the secondary throughput while protecting the primary users (PU) from service disruption and interference. In this paper, we propose an adaptive transmission power scheme for cognitive terminals opportunistically accessing a primary channel. The PU operates over the channel in an unslotted manner switching activity at random times. The secondary transmitter (STx) adapts its transmission power according to its belief regarding the PU's state of
AROMA: Automatic generation of radio maps for localization systems
Current methods for building radio maps for wireless localization systems require a tedious, manual and error-prone calibration of the area of interest. Each time the layout of the environment is changed or different hardware is used, the whole process of location fingerprinting and constructing the radio map has to be repeated. The process gets more complicated in the case of localizing multiple entities in a device-free scenario, since the radio map needs to take all possible combinations of the location of the entities into account. In this demo, we present a novel system (AROMA) that is
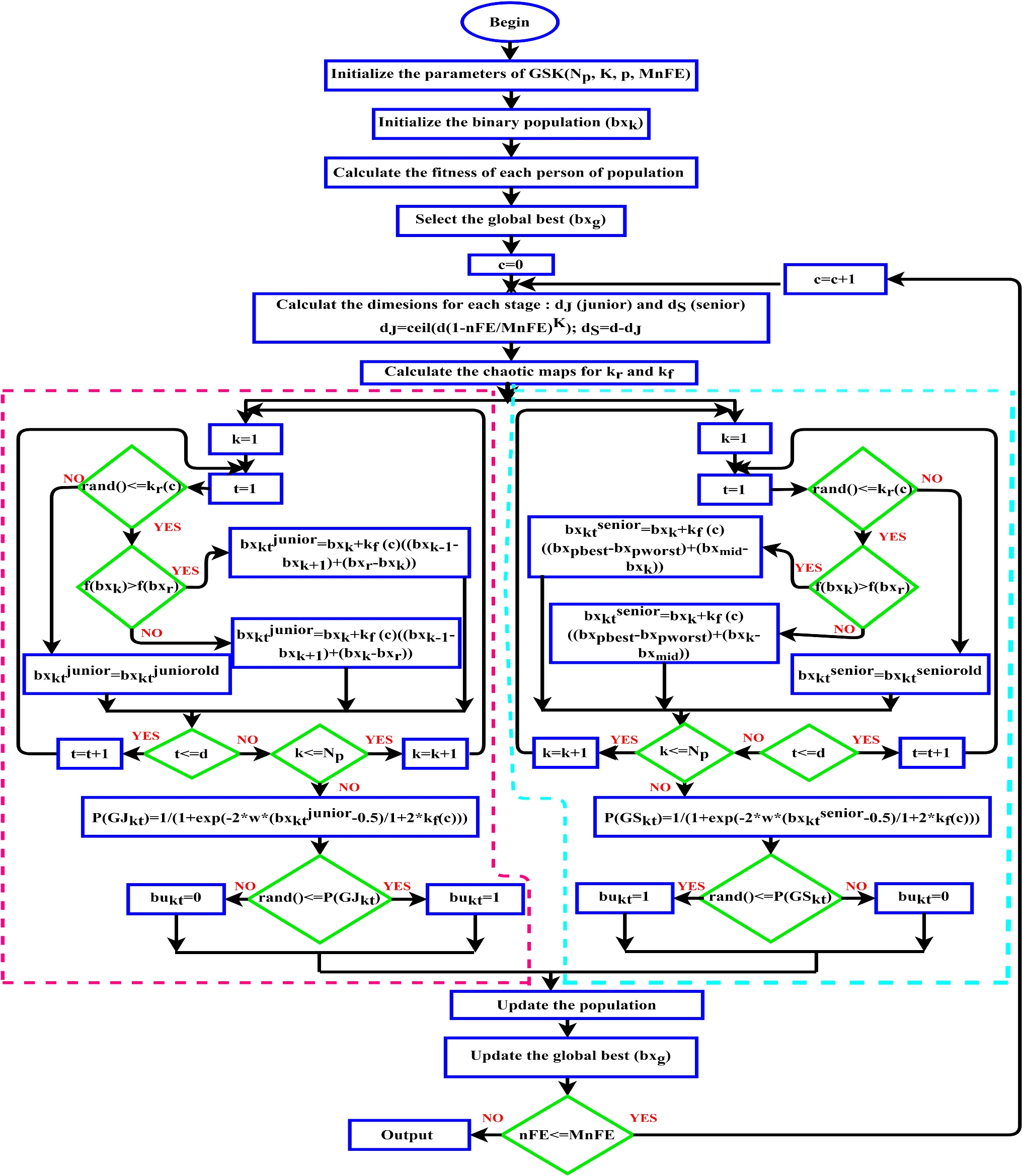
Chaotic gaining sharing knowledge-based optimization algorithm: an improved metaheuristic algorithm for feature selection
The gaining sharing knowledge based optimization algorithm (GSK) is recently developed metaheuristic algorithm, which is based on how humans acquire and share knowledge during their life-time. This paper investigates a modified version of the GSK algorithm to find the best feature subsets. Firstly, it represents a binary variant of GSK algorithm by employing a probability estimation operator (Bi-GSK) on the two main pillars of GSK algorithm. And then, the chaotic maps are used to enhance the performance of the proposed algorithm. Ten different types of chaotic maps are considered to adapt the
Towards Mobility-Aware Proactive Caching for Vehicular Ad hoc Networks
Harnessing information about the user mobility pattern and daily demand can enhance the network capability to improve the quality of experience (QoE) at Vehicular Ad- Hoc Networks (VANETs). Proactive caching, as one of the key features offered by 5G networks, has lately received much interest. However, more research is still needed to convey large-sized multimedia content including video, audio and pictures to the high speed moving vehicles. In this paper, we study the gains achieved by proactive caching in Roadside Units (RSUs) where we take into consideration the effect of the vehicle
Towards optimal resource allocation in caching at relay networks
We investigate the performance of caching in relay networks where an intermediate relay station (RS) caches content for future demand by end users. With uncertain user demand over multiple data items and dynamically changing wireless links, we characterize the optimal transmission time for serving data items, cached data portion allocation of relay station and optimal service portion, which represents a part from the cached portion, to minimize the total average transmission energy. We argue that under several settings fully caching the higher popular items is the optimal caching policy which
Towards optimal power control for delay-constrained cognitive radio networks
In this paper we study the problem of optimal power control for a Z-interference channel abstracting an underlay cognitive radio network where the secondary user has delay constraints. More specifically, we minimize the packet drop probability at the secondary user (equivalent to delay bound violation probability) subject to quality of service (QoS) constraints at the primary and secondary users, among other constraints. Towards, this objective, we develop a mathematical framework using Markov chains and formulate a constrained optimization problem. First, we assess the complexity of the
Reduced-complexity SFBC-OFDM for vehicular channels with high mobility
Space frequency block coding with orthogonal frequency division multiplexing (SFBC-OFDM) suffers from the effect of inter-carrier interference (ICI) in doubly-selective communication channels. In this paper, a scheme is proposed in which windowing is applied to the received signal to reduce the effect of ICI to a limited number of neighboring sub-carriers. The sub-carriers holding the SFBC components of each codeword are separated by a number of sub-carriers larger than the ICI range, and hence, they do not interfere with each other. In order to preserve the structure of the SFBC, the
Pagination
- Previous page ‹‹
- Page 12
- Next page ››
