Transform domain two dimensional and diagonal modular principal component analysis for facial recognition employing different windowing techniques
Spatial domain facial recognition Modular IMage Principal Component Analysis (MIMPCA) has an improved recognition rate compared to the conventional PCA. In the MPCA, face images are divided into smaller sub-images and the PCA approach is applied to each of these sub-images. In this work, the Transform Domain implementation of MPCA is presented. The facial image has two representations. The Two Dimensional MPCA (TD-2D-MPCA) and the Diagonal matrix MPCA (TD-Dia-MPCA). The sub-images are processed using both non-overlapping and overlapping windows. All the test results, for noise free and noisy
An approach for extracting and disambiguating arabic persons' names using clustered dictionaries and scored patterns
Building a system to extract Arabic named entities is a complex task due to the ambiguity and structure of Arabic text. Previous approaches that have tackled the problem of Arabic named entity recognition relied heavily on Arabic parsers and taggers combined with a huge set of gazetteers and sometimes large training sets to solve the ambiguity problem. But while these approaches are applicable to modern standard Arabic (MSA) text, they cannot handle colloquial Arabic. With the rapid increase in online social media usage by Arabic speakers, it is important to build an Arabic named entity
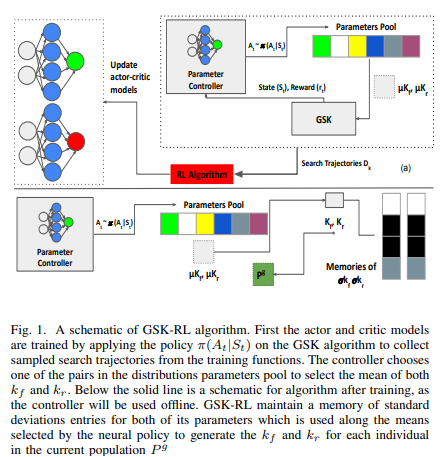
GSK-RL: Adaptive Gaining-sharing Knowledge algorithm using Reinforcement Learning
Meta-heuristics and nature inspired algorithms have been prominent solvers for highly complex, nonlinear and hard optimization problems. The Gaining-Sharing Knowledge algorithm (GSK) is a recently proposed nature-inspired algorithm, inspired by human and their tendency towards growth and gaining and sharing knowledge with others. The GSK algorithm have been applied to different optimization problems and proved robustness compared to other nature-inspired algorithms. The GSK algorithm has two main control parameters kfand kr which controls how much individuals gain and share knowledge with
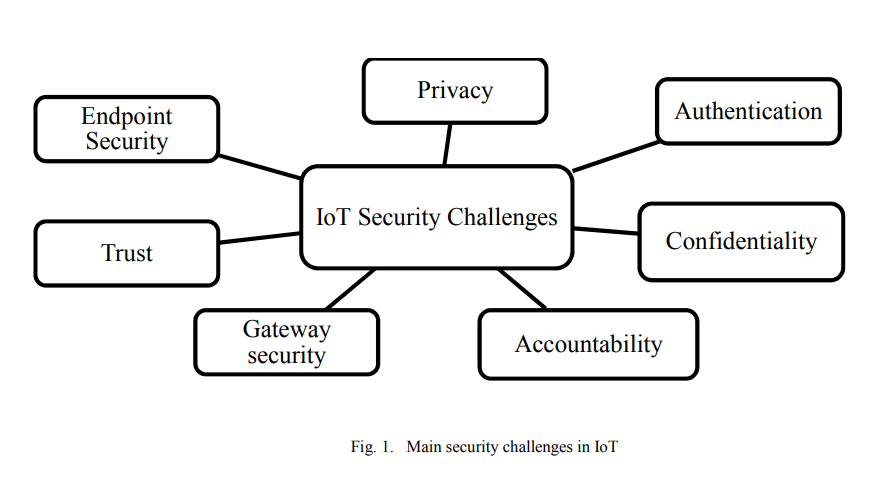
Internet of Things security framework
For the past decade, Internet of Things (IoT) had an important role in our lives. It connects a large number of embedded devices. These devices fulfill very difficult and complicated tasks, which facilitate our work. Till now the security of IoT faces many challenges such as privacy, authentication, confidentiality, trust, middleware security, mobile security and policy enforcement. In order to provide a secure environment for IoT, this paper proposes a framework for IoT devices. © 2017 IEEE.
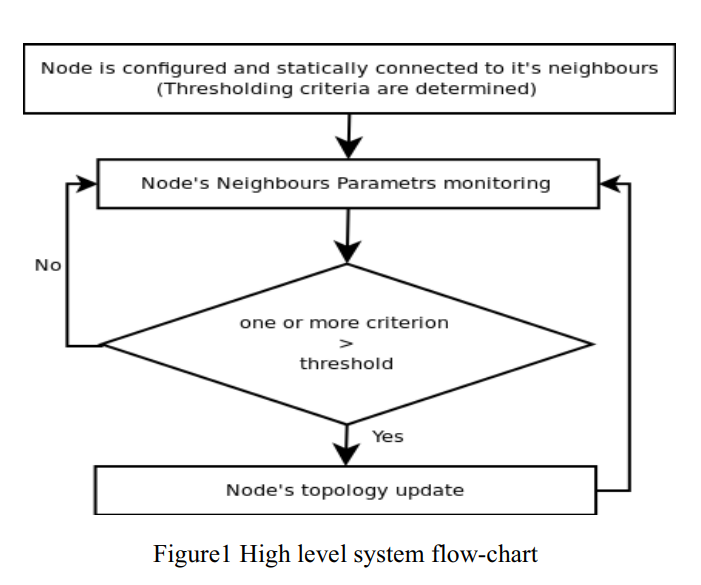
Janitor, certificate and jury (JCJ): Trust scheme for wireless ad-hoc networks
Ad hoc networks are peer mobile nodes that self configure to form a network. In these types of networks there is no routing infrastructure, and usually nodes have limited resources. This imposes a serious problem due to some nodes' selfishness and willingness to preserve their resources. Many approaches have been proposed to deal with this problem and mitigate the selfishness; amongst these approaches are reputation systems. This paper proposes a reputation system scheme that helps isolating misbehaving nodes and decreasing their ability to launch an attack on the network. The idea of this
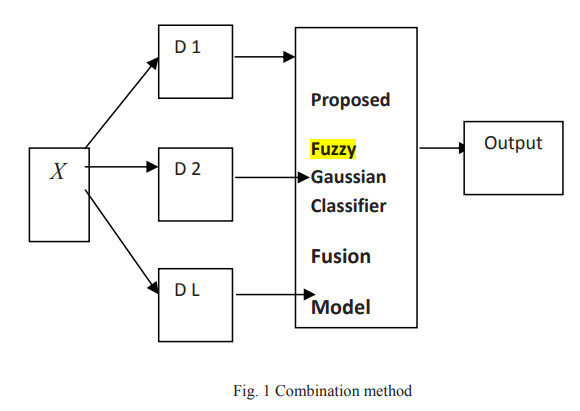
Fuzzy gaussian classifier for combining multiple learners
In the field of pattern recognition multiple classifier systems based on the combination of outputs from different classifiers have been proposed as a method of high performance classification systems. The objective of this work is to develop a fuzzy Gaussian classifier for combining multiple learners, we use a fuzzy Gaussian model to combine the outputs obtained from K-nearest neighbor classifier (KNN), Fuzzy K-nearest neighbor classifier and Multi-layer Perceptron (MLP) and then compare the results with Fuzzy Integral, Decision Templates, Weighted Majority, Majority Naïve Bayes, Maximum
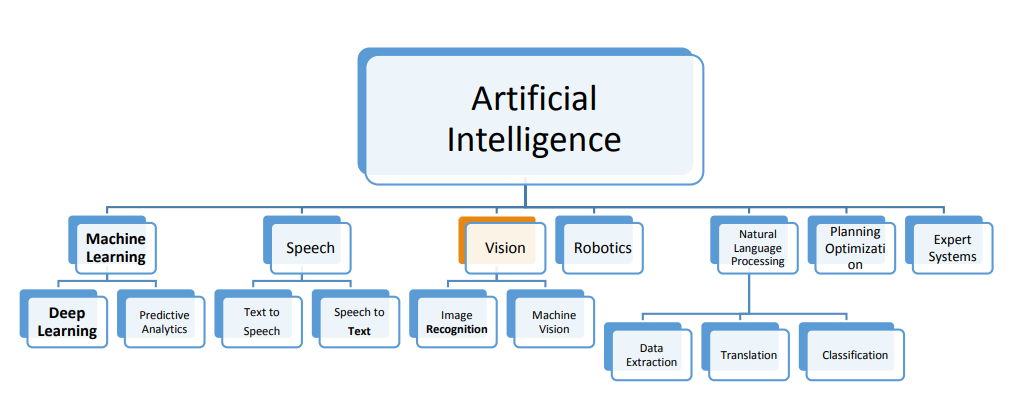
Artificial intelligence for retail industry in Egypt: Challenges and opportunities
In the era of digital transformation, a mass disruption in the global industries have been detected. Big data, the Internet of Things (IoT) and Artificial Intelligence (AI) are just examples of technologies that are holding such digital disruptive power. On the other hand, retailing is a high-intensity competition and disruptive industry driving the global economy and the second largest globally in employment after the agriculture. AI has large potential to contribute to global economic activity and the biggest sector gains would be in retail. AI is the engine that is poised to drive the
Assessing leanness level with demand dynamics in a multi-stage production system
Purpose - The purpose of this paper is to present a dynamic model to measure the degree of system's leanness under dynamic demand conditions using a novel integrated metric. Design/methodology/approach - The multi-stage production system model is based on a system dynamics approach. The leanness level is measured using a new developed integrated metric that combines efficiency,WIP performance as well as service level. The analysis includes design of experiment technique at the initial analysis to examine the most significant parameters impacting the leanness score and then followed by
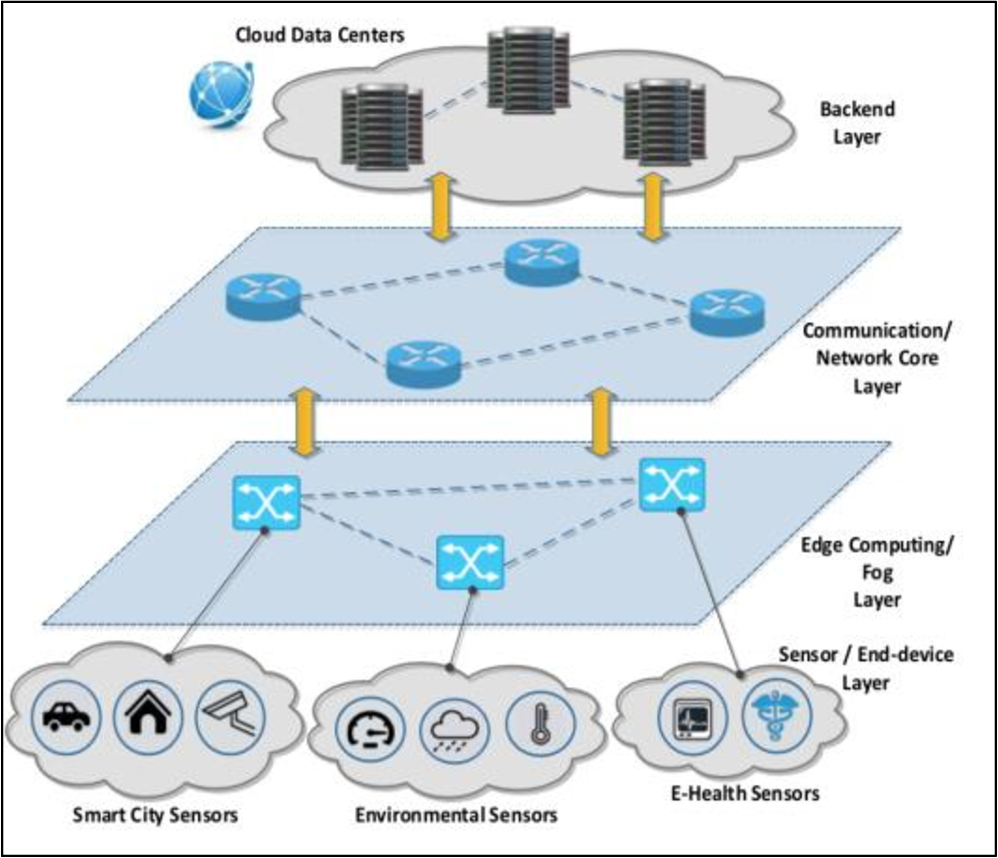
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
Current-Mode Multiplier Accumulator Design using a Memristor-Transistor Crossbar Architecture
This paper discusses the implementation of a Multiplier Accumulator (MAC) design using memristor and crossbar architecture. MAC consists of an array of memristors alongside transistors making a cell that works as a switch (i.e., turned ON or OFF). When a cell is selected, it adds the current in the array path, followed by a current mirror circuit amplified to determine the accumulated current. A traditional MAC is also implemented to compare it with the proposed MAC. The proposed MAC consumed power of 3.9μW, while the traditional MAC consumed power of 19μW. The delay of the proposed MAC is 1
Pagination
- Previous page ‹‹
- Page 57
- Next page ››
