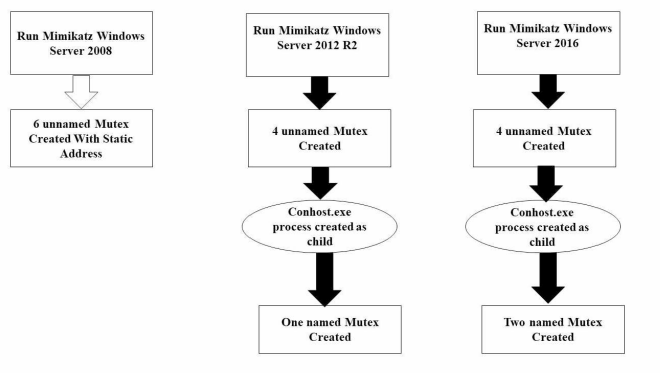
Detecting Mimikatz in Lateral Movements Using Mutex
Advanced Persistent Threat (APT) is a stealthy computer network attack. Its threat lies in the fact that unauthorized access to a network is gained and the attackers, whether a person or a group may remain undetected for an extended period. APT group can spread and gain access to the most valuable assets in the targeted organization. Depending on the tools used by APT group it can be hard and complex to respond to those groups and their tools. Mimikatz is one of the most powerful tools used by many APT groups, penetration testers and malware. In this paper, we focus on lateral movement and APT
Cooperation incentives in wireless ad hoc networks
Mobile ad hoc networks heavily rely on nodes' cooperation for packet forwarding. As a result, misbehaving, malicious, and selfish nodes can significantly degrade the performance of the network. To cope with this issue and to stimulate cooperation among selfish mobile nodes, a continuous research effort is done on identifying nodes trust and reputation. In this paper, we survey recently proposed reputation and incentive schemes for ad hoc networks. In order to help in the design of different reputation systems tailored to specific applications and network topologies, we classify the different
Traffic Analysis for Real Time Applications and its Effect on QoS in MANETs
Quality of Service (QoS) is one of the major challenges in Mobile Ad-hoc Networks (MANETs), due to their nature and special characteristics. QoS depends on different and multiple metrics such as routing protocols, route stability, channel rate quality, bandwidth, ... etc. Most of studies focus on the above metrics and some of them proposed enhancements. However, there are still unfilled gaps that need to be tackled. In this paper, we focus on the impact of QoS parameters on MANETs. The main objective is to identify the suitable applications in MANETs with respect to the network parameters. ©
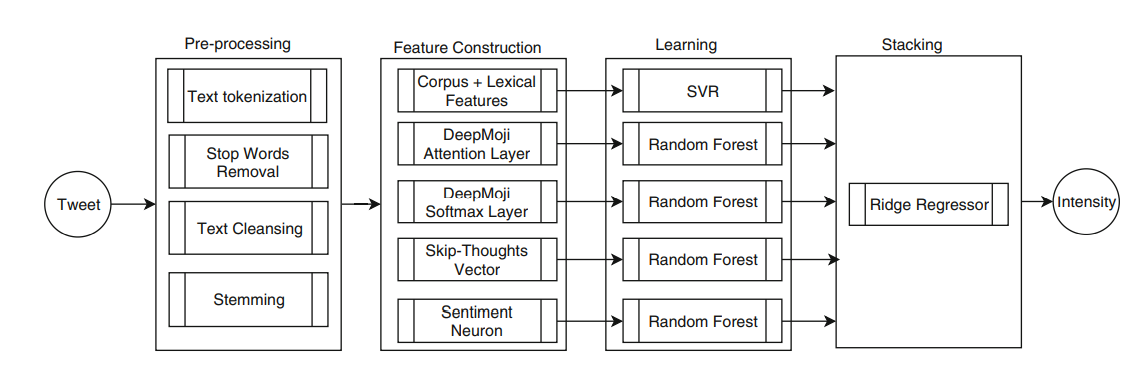
A Transfer Learning Approach for Emotion Intensity Prediction in Microblog Text
Emotional expressions are an important part of daily communication between people. Emotions are commonly transferred non verbally through facial expressions, eye contact and tone of voice. With the rise in social media usage, textual communication in which emotions are expressed has also witnessed a great increase. In this paper automatic emotion intensity prediction from text is addressed. Different approaches are explored to find out the best model to predict the degree of a specific emotion in text. Experimentation was conducted using the dataset provided by SemEval-2018 Task 1: Affect in
Simultaneous human detection and action recognition employing 2DPCA-HOG
In this paper a novel algorithm for Human detection and action recognition in videos is presented. The algorithm is based on Two-Dimensional Principal Components Analysis (2DPCA) applied to Histogram of Oriented Gradients (HOG). Due to simultaneous Human detection and action recognition employing the same algorithm, the computational complexity is reduced to a great deal. Experimental results applied to public datasets confirm these excellent properties compared to most recent methods. © 2011 IEEE.
Face and gesture recognition for human computer interaction employing 2DHoG
Face and hand gesture recognition is one of the most challenging topics in computer vision. In this paper, a novel algorithm presenting a new 2D representation of histogram of oriented gradients is proposed, where each bin represents a range of angles dealt with in a separate layer employing 2DPCA. This method maintains the spatial relation between pixels which enhance the recognition accuracy. In addition it can be applied on either face or hand gesture images. Experimental results confirm excellent properties of the proposed algorithm and promotes it for real time applications © 2013 IEEE.
DiSGD: A distributed shared-nothing matrix factorization for large scale online recommender systems
With the web-scale data volumes and high velocity of generation rates, it has become crucial that the training process for recommender systems be a continuous process which is performed on live data, i.e., on data streams. In practice, such systems have to address three main requirements including the ability to adapt their trained model with each incoming data element, the ability to handle concept drifts and the ability to scale with the volume of the data. In principle, matrix factorization is one of the popular approaches to train a recommender model. Stochastic Gradient Descent (SGD) has
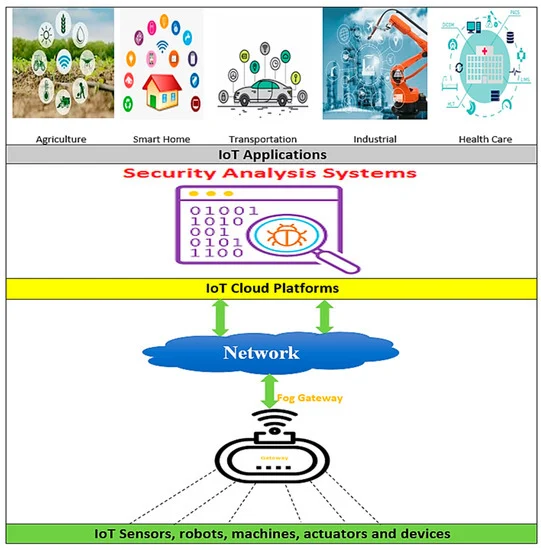
HSAS-MD Analyzer: A Hybrid Security Analysis System Using Model-Checking Technique and Deep Learning for Malware Detection in IoT Apps
Established Internet of Things (IoT) platforms suffer from their inability to determine whether an IoT app is secure or not. A security analysis system (SAS) is a protective shield against any attack that breaks down data privacy and security. Its main task focuses on detecting malware and verifying app behavior. There are many SASs implemented in various IoT applications. Most of them build on utilizing static or dynamic analysis separately. However, the hybrid analysis is the best for obtaining accurate results. The SAS provides an effective outcome according to many criteria related to the
Recognizing Clothing Patterns and Colors for BVI People Using Different Techniques
For blind and visually impaired (BVI) people, it is an arduous task to recognize clothing patterns and colors. It is especially complex to recognize them automatically. This is a highly researched area in image processing. This paper provides BVI with the ability to detect patterns and colors without depending on personal assistance, leading to increasing their confidence. The user first captures an image; then, our system detects colors and patterns. The color model used here is the hue saturation value (HSV). The main colors detected by our system are magenta, cyan, blue, green, red and
Transverse momentum spectra of strange hadrons within extensive and nonextensive statistics
Using generic (non)extensive statistics, in which the underlying system likely autonomously manifests its extensive and nonextensive statistical nature, we extract various fit parameters from the CMS experiment and compare these to the corresponding results obtained from Tsallis and Boltzmann statistics. The present study is designed to indicate the possible variations between the three types of statistical approaches and characterizes their dependence on collision energy, multiplicity, and size of the system of interest. We analyze the transverse momentum spectra pT of the strange hadrons Ks
Pagination
- Previous page ‹‹
- Page 2
- Next page ››
