Gray Wolf Optimization of Fractional Order Control of 3-Omni Wheels Mobile Robot: Experimental Study
Committing robotics with artificial intelligence becomes mandatory collaboration with distinct environments. Omnidirectional Wheeled (Omni-WD) mobile robots are one of the robots that interact with humans in various circumstances, where it is important to function effectively and accurately. In this paper, the distinction of a 3WD-Omni model and control using machine vision is demonstrated. The use of fractional order (FO) calculus has been stated to increase the degrees of freedom of the controller over the integer ones. Hybridization of FO control and metaheuristics optimization is reported
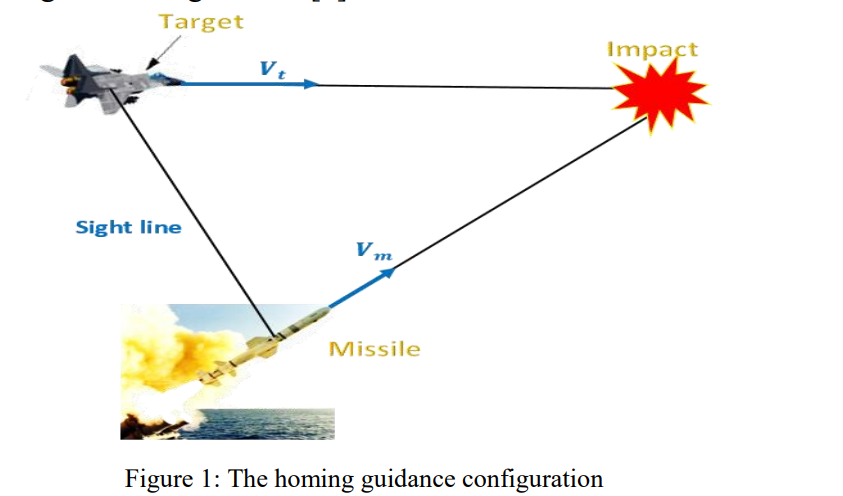
Intercept algorithm for maneuvering targets based on differential geometry and lyapunov theory
Nowadays, the homing guidance is utilized in the existed and under development air defense systems (ADS) to effectively intercept the targets. The targets became smarter and capable to fly and maneuver professionally and the tendency to design missile with a small warhead became greater, then there is a pressure to produce a more precise and accurate missile guidance system based on intelligent algorithms to ensure effective interception of highly maneuverable targets. The aim of this paper is to present an intelligent guidance algorithm that effectively and precisely intercept the
A Grunwald–Letnikov based Manta ray foraging optimizer for global optimization and image segmentation
This paper presents a modified version of Manta ray foraging optimizer (MRFO) algorithm to deal with global optimization and multilevel image segmentation problems. MRFO is a meta-heuristic technique that simulates the behaviors of manta rays to find the food. MRFO established its ability to find a suitable solution for a variant of optimization problems. However, by analyzing its behaviors during the optimization process, it is observed that its exploitation ability is less than exploration ability, which makes MRFO more sensitive to attractive to a local point. Therefore, we enhanced MRFO by
Control design approaches for parallel robot manipulators: A review
In this article, different control design approaches for parallel robot manipulators are presented with two distinguished classes of control strategies in the literature. These are the model-free control and the dynamic control strategy, which is mainly a model-based scheme, and is mostly the alternative when the control requirements are more stringent. The authors strongly believe that this paper will be helpful for researchers and engineers in the field of robotic systems. Copyright 2017 Inderscience Enterprises Ltd.
Diabetes Prediction Using Machine Learning: A Comparative Study
Diabetes is a common, metabolic disease, that results in a high level of blood sugar. Patients diagnosed with diabetes suffer from a body that cannot effectively use the insulin or cannot produce a sufficient amount of insulin. Providing a method of detection via symptoms that can be noticed by the patient can prompt the patient to seek medical assistance more promptly and in turn to be correctly diagnosed and treated. This paper proposed a solution for the problem using machine learning techniques. We applied eight algorithms on a data set of 521 subjects. The results are compared to each
Study of Energy Harvesters for Wearable Devices
Energy harvesting was and still an important point of research. Batteries have been utilized for a long time, but they are now not compatible with the downsizing of technology. Also, their need to be recharged and changed periodically is not very desirable, therefore over the years energy harvesting from the environment and the human body have been investigated. Three energy harvesting methods which are the Piezoelectric energy harvesters, the Enzymatic Biofuel cells, and Triboelectric nanogenerators (TENGs) are being discussed in the paper. Although Biofuel cells have been investigated for a
Fractional canny edge detection for biomedical applications
This paper presents a comparative study of edge detection algorithms based on integer and fractional order differentiation. A performance comparison of the two algorithms has been proposed. Then, a soft computing technique has been applied to both algorithms for better edge detection. From the simulations, it shows that better performance is obtained compared to the classical approach. The noise performances of those algorithms are analyzed upon the addition of random Gaussian noise, as well as the addition of salt and pepper noise. The performance has been compared to peak signal to noise
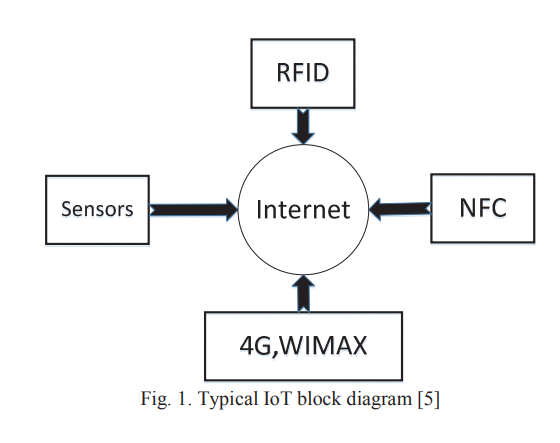
IoT ethics challenges and legal issues
IoT systems have different technologies such as: RIFD, NFC, 3G, 4G, and Sensors. Their function is to transfer very large sensitive and private data. There are many ethical challenges that need to be taken into consideration by individuals and companies that use this technology. Amongst the challenges is the user awareness of attack risks. This paper discusses different ethical and legal challenges that need to be taken in account for IoT health care applications during the near future. © 2017 IEEE.
FPGA-Based Memristor Emulator Circuit for Binary Convolutional Neural Networks
Binary convolutional neural networks (BCNN) have been proposed in the literature for resource-constrained IoTs nodes and mobile computing devices. Such computing platforms have strict constraints on the power budget, system performance, processing and memory capabilities. Nonetheless, the platforms are still required to efficiently perform classification and matching tasks needed in various applications. The memristor device has shown promising results when utilized for in-memory computing architectures, due to its ability to perform storage and computation using the same physical element
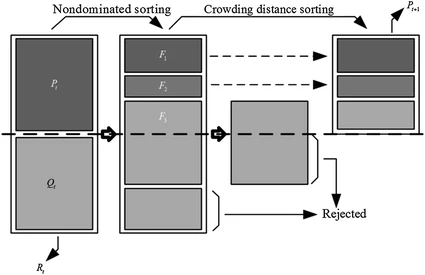
Chaotic system modelling using a neural network with optimized structure
In this work, the Artificial Neural Networks (ANN) are used to model a chaotic system. A method based on the Non-dominated Sorting Genetic Algorithm II (NSGA-II) is used to determine the best parameters of a Multilayer Perceptron (MLP) artificial neural network. Using NSGA-II, the optimal connection weights between the input layer and the hidden layer are obtained. Using NSGA-II, the connection weights between the hidden layer and the output layer are also obtained. This ensures the necessary learning to the neural network. The optimized functions by NSGA-II are the number of neurons in the
Pagination
- Page 1
- Next page ››
