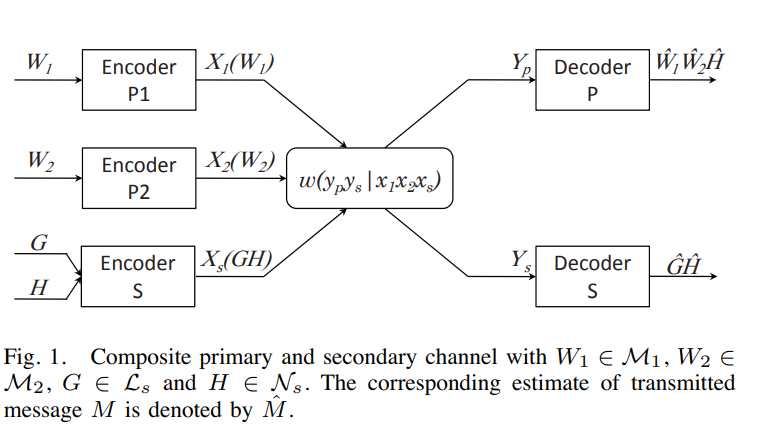
An achievable rate region for a primary network shared by a secondary link
We consider a multiple access primary network with N transmitters. A secondary link of one transmitter and a corresponding receiver causes interference to the primary network. An achievable rate region for the primary network and the secondary link is obtained given the following mode of operation. The secondary transmitter employs rate-splitting so that the primary receiver can decode part of the secondary's signal and cancel it. The secondary receiver, on the other hand, treats primary interference as noise. Given a Gaussian channel model, we investigate the effect of rate-splitting on the
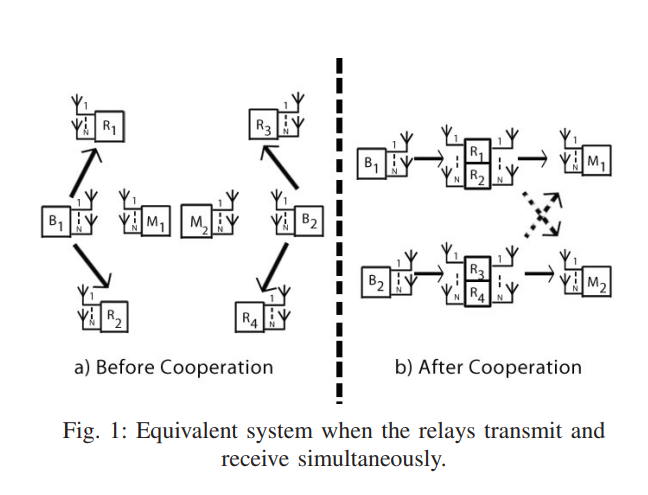
Alternate relaying and the degrees of freedom of one-way cellular relay networks
In this paper, a cellular relaying network consisting of two source-destination pairs, and four decode-and-forward relays operating in half-duplex mode is considered. Each source is assisted by two relays and all nodes are equipped with N antennas. In order to compensate for the loss of capacity by a factor of half due to the half-duplex mode, an alternate transmission protocol among the two relays is proposed. An outer bound on the degrees of freedom (DoF) of this system is developed. A constructive proof of achievability based on two different schemes is provided. Aligning the inter-relay
Optimum Scheduling of the Disinfection Process for COVID-19 in Public Places with a Case Study from Egypt, a Novel Discrete Binary Gaining-Sharing Knowledge-Based Metaheuristic Algorithm
The aim of this paper is to introduce an improved strategy for controlling COVID-19 and other pandemic episodes as an environmental disinfection culture for public places. The scheduling aims at achieving the best utilization of the available working day-time hours, which is calculated as the total consumed disinfection times minus the total loosed transportation times. The proposed problem in network optimization identifies a disinfection group who is likely to select a route to reach a subset of predetermined public places to be regularly disinfected with the most utilization of the
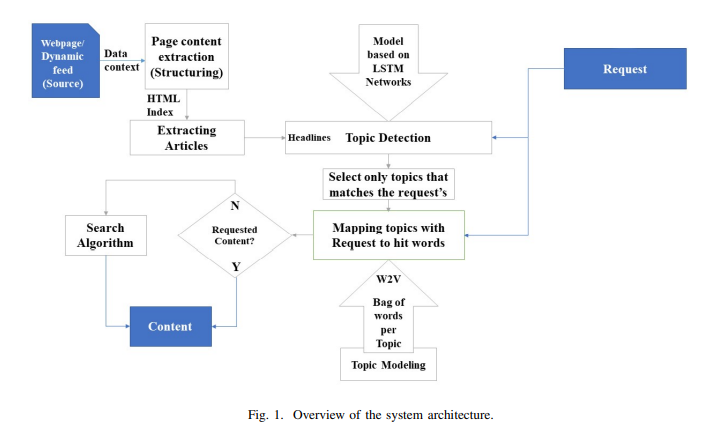
Towards Intelligent Web Context-Based Content On-Demand Extraction Using Deep Learning
Information extraction and reasoning from massive high-dimensional data at dynamic contexts, is very demanding and yet is very hard to obtain in real-time basis. However, such process capability and efficiency might be affected and limited by the available computational resources and the consequent power consumption. Conventional search mechanisms are often incapable of real-time fetching a predefined content from data source, without concerning the increased number of connected devices that contribute to the same source. In this work, we propose and present a concept for an efficient approach
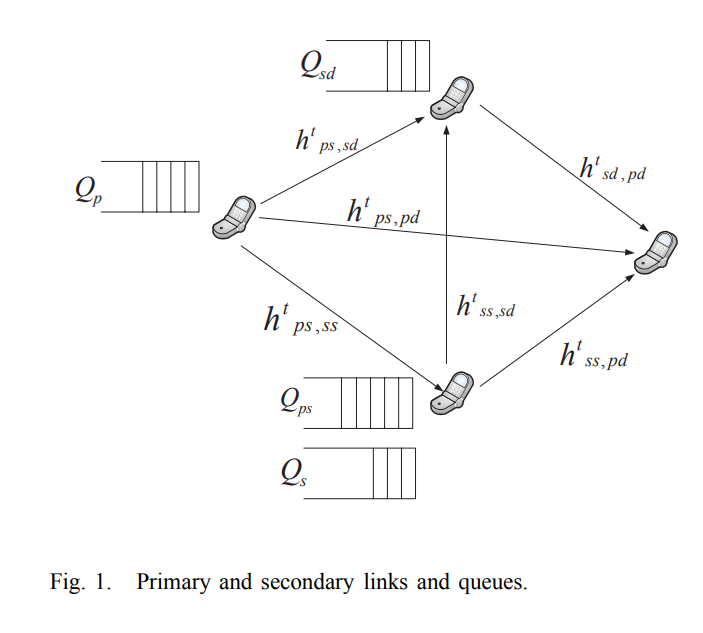
Transmit and receive cooperative cognition: Protocol design and stability analysis
In this paper, we investigate the stability of a cooperative cognitive system. We propose a cooperative secondary transmitter-receiver system (CSTR), where, the secondary transmitter (ST) and the secondary receiver (SR) increase the spectrum availability for the ST packets by relaying the unsuccessfully transmitted packets of the primary transmitter (PT). We assume receiving nodes with multipacket reception capability (MPR). We provide two inner bounds and two outer bounds on the stability region of the considered system. © 2013 ICST - The Institute for Computer Sciences, Social Informatics
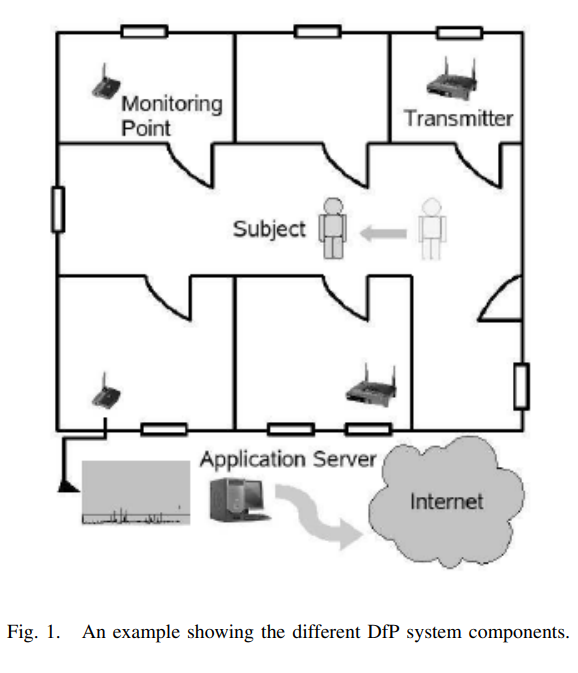
Smart devices for smart environments: Device-free passive detection in real environments
Device-free Passive (DfP) localization is a system envisioned to detect, track, and identify entities that do not carry any device, nor participate actively in the localization process. A DfP system allows using nominal WiFi equipment for intrusion detection, without using any extra hardware, adding smartness to any WiFi-enabled device. In this paper, we focus on the detection function of the DfP system in a real environment. We show that the performance of our previously developed algorithms for detection in a controlled environments, which achieved 100% recall and precision, degrades
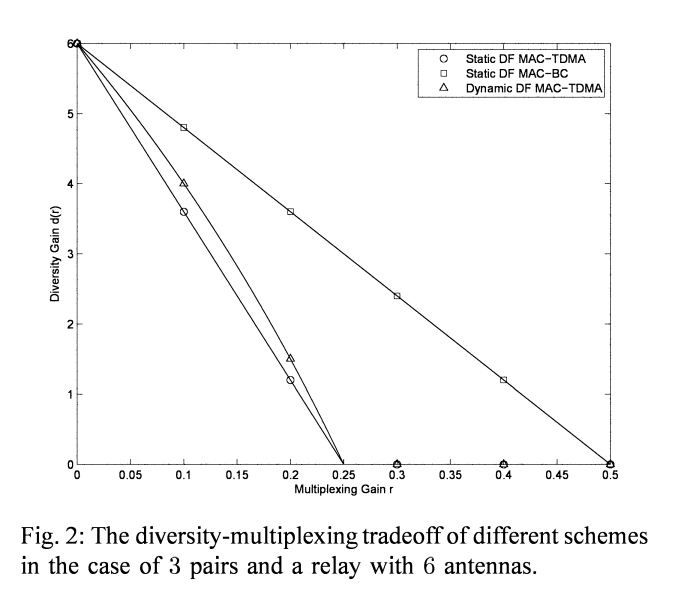
The MIMO wireless switch: Relaying can increase the multiplexing gain
This paper considers an interference network composed of K half-duplex single-antenna pairs of users who wish to establish bi-directional communication with the aid of a multiinput-multi-output (MIMO) half-duplex relay node. This channel is referred to as the "MIMO Wireless Switch" since, for the sake of simplicity, our model assumes no direct link between the two end nodes of each pair implying that all communication must go through the relay node (i.e., the MIMO switch). Assuming a delay-limited scenario, the fundamental limits in the high signal-to-noise ratio (SNR) regime is analyzed using
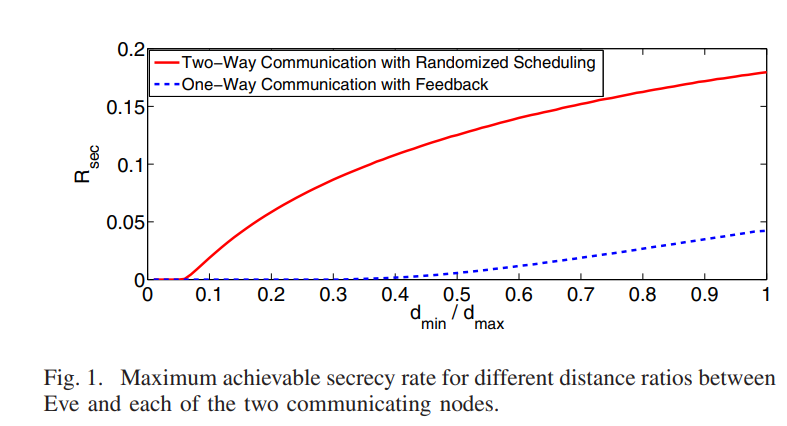
Randomization for security in half-duplex two-way Gaussian channels
This paper develops a new physical layer framework for secure two-way wireless communication in the presence of a passive eavesdropper, i.e., Eve. Our approach achieves perfect information theoretic secrecy via a novel randomized scheduling and power allocation scheme. The key idea is to allow Alice and. Bob to send symbols at random time instants. While Alice will be able to determine the symbols transmitted by Bob, Eve will suffer from ambiguity regarding the source of any particular symbol. This desirable ambiguity is enhanced, in our approach, by randomizing the transmit power level. Our
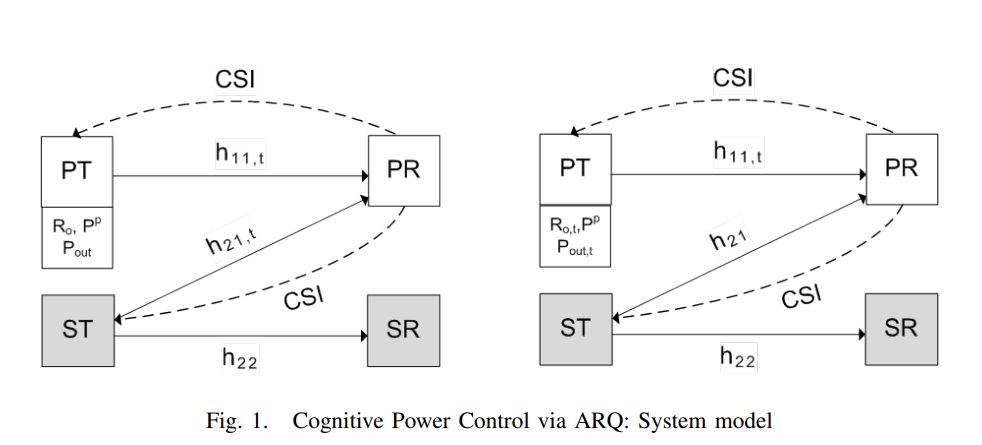
Throughput maximization over temporally correlated fading channels in cognitive radio networks
We consider a primary link and a secondary link, each composed of a transmitter and a receiver. The primary channel and the channel between the secondary transmitter and the primary receiver follow a first-order Markov model for channel variation over time. Under this assumption of temporal correlation and via exploiting the channel state information (CSI) feedback, we pose the cognitive power control problem as the maximization of secondary throughput subject to a constraint on the primary outage. To solve this problem, we assume that the primary transmitter sends with a constant-rate and

SANC: Source authentication using network coding
In this paper, we explore the security merits of network coding and potential trade-offs with the widely accepted throughput benefits, especially in multicast scenarios. In particular, we propose a novel Source Authentication using Network Coding (SANC) scheme that can either complement state-of-the-art application-layer authentication schemes proposed in the literature or be used as a stand-alone scheme in network coding-based networks. Towards this objective, we propose a general framework for embedding the authentication information within the network coding Global Encoding Vector. This is
Pagination
- Previous page ‹‹
- Page 28
- Next page ››
