Evaluating the Modsecurity Web Application Firewall against SQL Injection Attacks
SQL injection attacks target databases of web servers. The ability to modify, update, retrieve and delete database contents imposes a high risk on any website in different sectors. In this paper, we investigate the efforts done in the literature to detect and prevent the SQL injection attacks. We also assess the efficiency of the Modsecurity web application firewall in preventing SQL injection attacks. © 2020 IEEE.
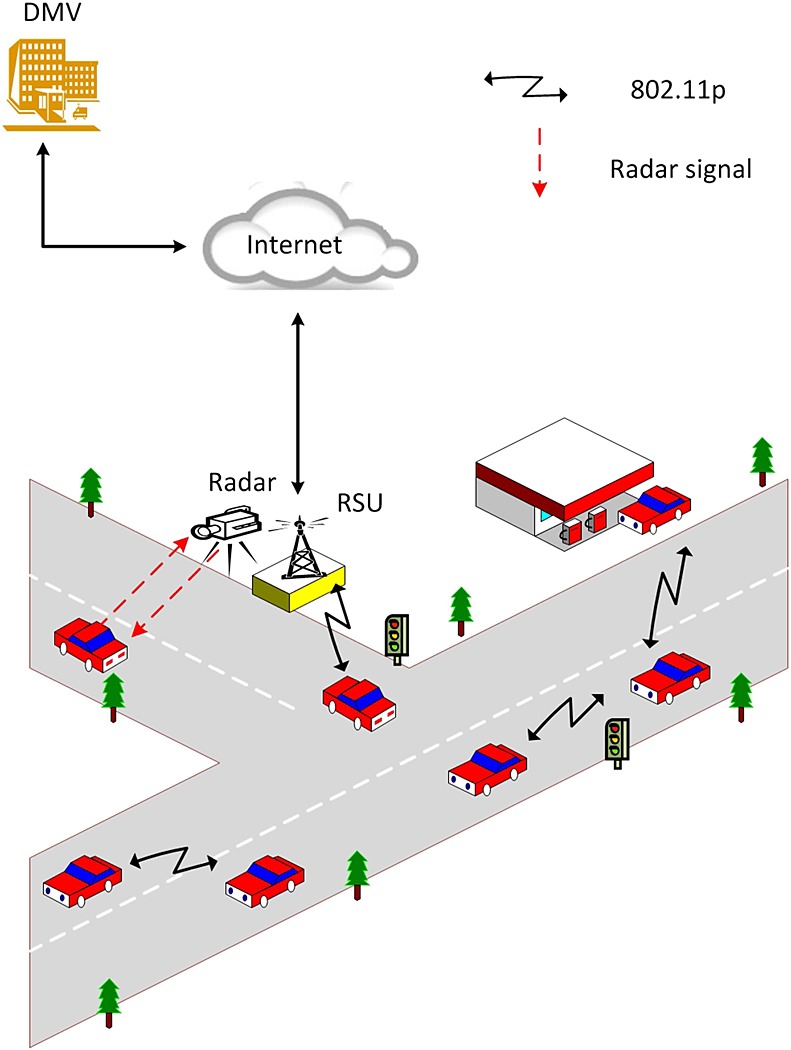
A secure and privacy-preserving event reporting scheme for vehicular Ad Hoc networks
In vehicular ad hoc networks, vehicles should report events to warn the drivers of unexpected hazards on the roads. While these reports can contribute to safer driving, vehicular ad hoc networks suffer from various security threats; a major one is Sybil attacks. In these attacks, an individual attacker can pretend as several vehicles that report a false event. In this paper, we propose a secure event-reporting scheme that is resilient to Sybil attacks and preserves the privacy of drivers. Instead of using asymmetric key cryptography, we use symmetric key cryptography to decrease the
Cloud computing privacy issues, challenges and solutions
There are many cloud computing initiatives that represent a lot of benefit to enterprise customers. However, there are a lot of challenges and concerns regarding the security and the privacy of the customer data that is hosted on the cloud. We explore in this paper the various aspects of cloud computing regarding data life cycle and its security and privacy challenges along with the devised methodology to address those challenges. We mention some of the regulations and law requirements in place to ensure cloud customer data privacy. © 2017 IEEE.
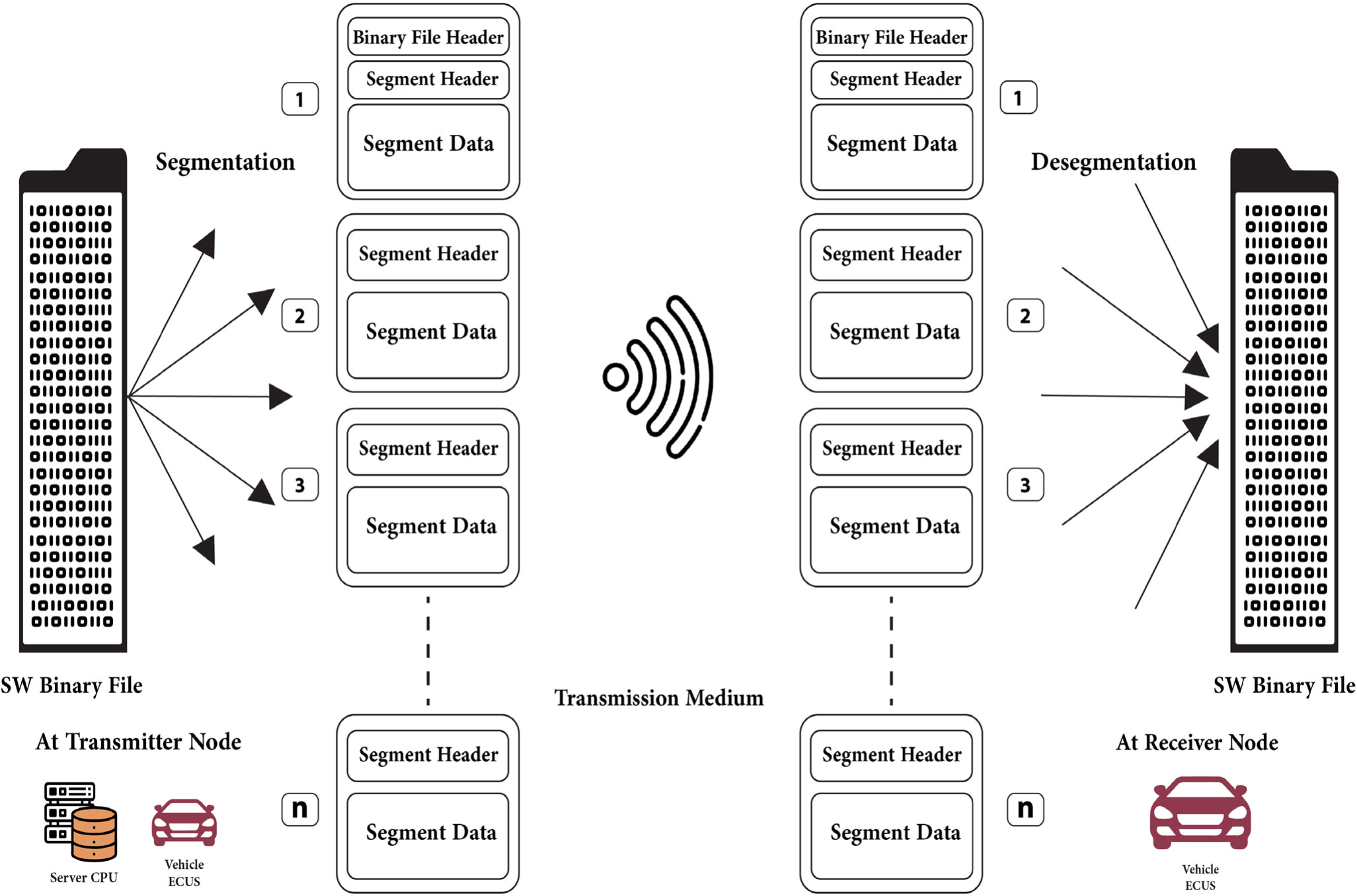
Segmented OTA Platform Over ICN Vehicular Networks
The Internet Protocol (IP) architecture could not fully satisfy the Vehicular Ad-hoc Networks (VANETs) needed efficiency, due to their dynamic topology and high mobility. This paper presents a technique that updates the software of Electronic Control Units (ECUs) in vehicles using segmented Over The Air (OTA) platform over Information-Centric Network (ICN) architecture. In VANET, the amount of time for active vehicles’ connectivity varies due to the vehicular network’s dynamic topologies. The importance of Flashing Over The Air (FOTA) has been illustrated as well as the impact of applying the
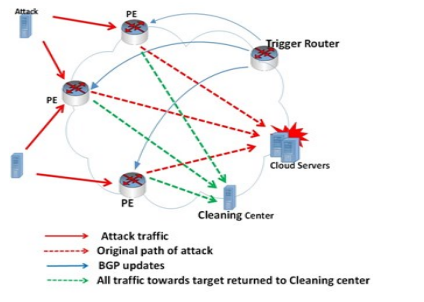
Detection and Countermeasures of DDoS Attacks in Cloud Computing
Greater portions of the world are moving to cloud computing because of its advantages However, due to its distributed nature, it can be easily exploited by Distributed Denial of Service (DDoS) attacks. In distributed DDoS attacks, legitimate users are prevented from using cloud resources. In this paper, the various DDoS detection and defenses mechanisms cloud computing are reviewed. We propose a new technique based on Remote Triggered Black Hole (RTBH) to prevent DDoS attacks before it target to cloud resources. © 2018 IEEE.
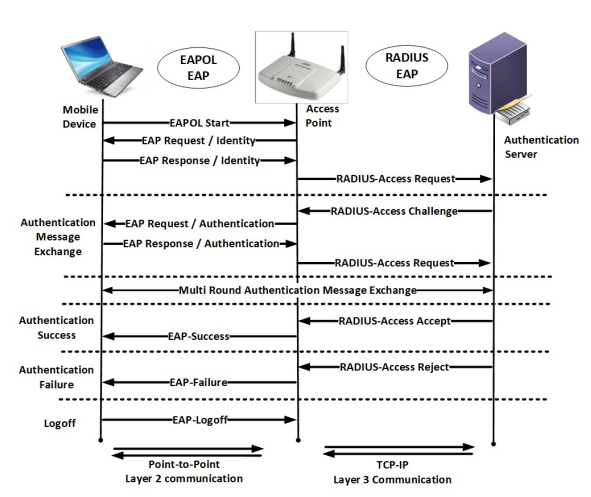
A study in WPA2 enterprise recent attacks
Organizations and network developers continuously exert much money and efforts to secure wireless transmission. WPA2 framework is widely deployed for Wi-Fi communications since it is efficient and secure against several wireless attacks. However, WPA2 security has been lately threatened by advanced developed versions of wireless attacks. The increase of computer processing power, continuous efforts by penetration testers, network evaluators and researchers led to the emerging of new advanced attacking techniques that may exploit WPA2 wireless systems detected vulnerabilities. In this paper, we
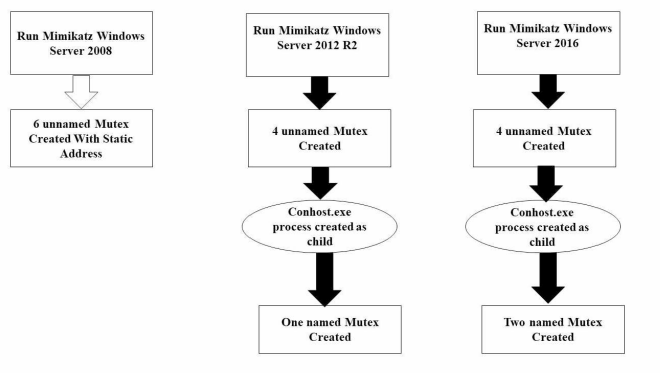
Detecting Mimikatz in Lateral Movements Using Mutex
Advanced Persistent Threat (APT) is a stealthy computer network attack. Its threat lies in the fact that unauthorized access to a network is gained and the attackers, whether a person or a group may remain undetected for an extended period. APT group can spread and gain access to the most valuable assets in the targeted organization. Depending on the tools used by APT group it can be hard and complex to respond to those groups and their tools. Mimikatz is one of the most powerful tools used by many APT groups, penetration testers and malware. In this paper, we focus on lateral movement and APT
Reconstruction of High Resolution image from a set of blurred, warped, undersampled, and noisy measured images
This paper proposes an algorithm to reconstruct a High Resolution (HR) image from a set of blurred, warped, undersampled, and noisy measured images. The proposed algorithm uses the affine block-based algorithm in the maximum likelihood (ML) estimator. It is tested using synthetic images, where the reconstructed image can be compared with its original. A number of experiments were performed with the proposed algorithm to evaluate its behavior before and after noise addition and also compared with its behavior after noise removal. The proposed system results show that the enhancement factor is
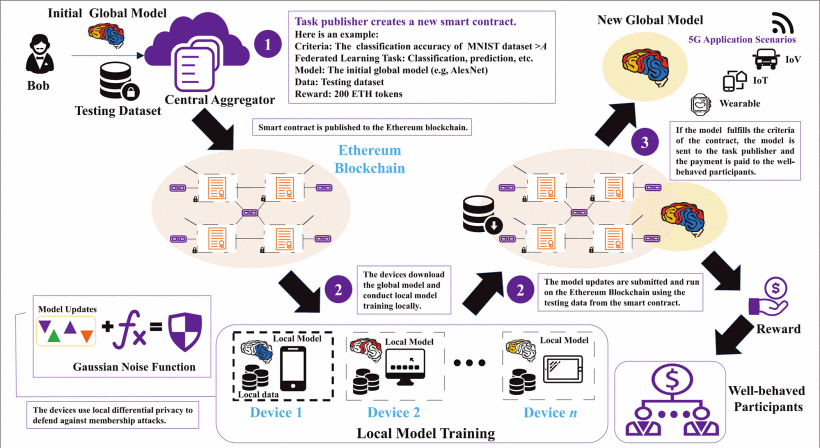
A Secure Federated Learning Framework for 5G Networks
Federated learning (FL) has recently been proposed as an emerging paradigm to build machine learning models using distributed training datasets that are locally stored and maintained on different devices in 5G networks while providing privacy preservation for participants. In FL, the central aggregator accumulates local updates uploaded by participants to update a global model. However, there are two critical security threats: poisoning and membership inference attacks. These attacks may be carried out by malicious or unreliable participants, resulting in the construction failure of global
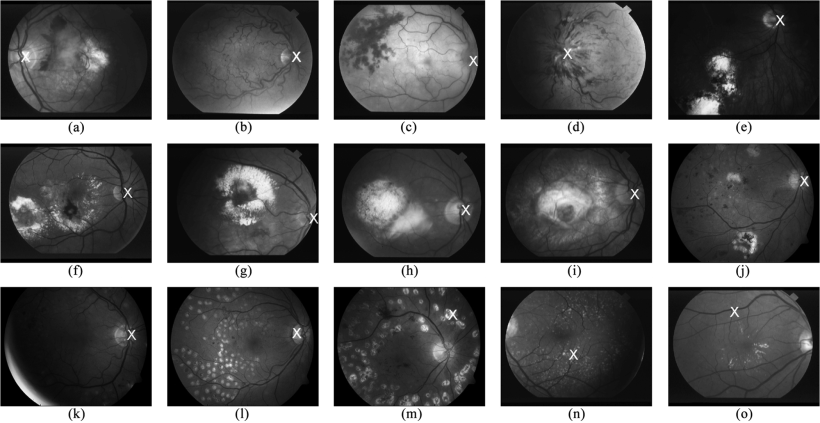
Fast localization of the optic disc using projection of image features
Optic Disc (OD) localization is an important pre-processing step that significantly simplifies subsequent segmentation of the OD and other retinal structures. Current OD localization techniques suffer from impractically-high computation times (few minutes per image). In this work, we present a fast technique that requires less than a second to localize the OD. The technique is based upon obtaining two projections of certain image features that encode the x- and y- coordinates of the OD. The resulting 1-D projections are then searched to determine the location of the OD. This avoids searching
Pagination
- Previous page ‹‹
- Page 20
- Next page ››
