Arithmetic optimization approach for parameters identification of different PV diode models with FOPI-MPPT
The Maximum Power Point Tracker (MPPT) provides the most efficient use of a Photo-voltaic system independent of irradiance or temperature fluctuations. This paper introduces the modeling and control of a photo-voltaic system operating at MPPT using the arithmetic optimization algorithm (AOA). The single and double Photo-voltaic models are investigated. Their optimal unknown parameters are extracted using AOA based on commercial Photo-voltaic datasheets. A comparison is performed between these optimal parameters extracted by AOA and other optimization techniques presented in the literature
Modeling and characterization of carrier mobility for truncated conical quantum dot infrared photodetectors
In the present paper, a theoretical model for calculating the carrier mobility which is a result of the existence of a truncated conical quantum dots of n-type quantum dot infrared photodetectors (QDIPs) is developed. This model is built on solving Boltzmann’s transport equation that is a complex integro-differential equation describing the carrier transport. The time-domain finite-difference method is used in this numerical solution. The influences of dimensions and density of the QDs for this structure on the carrier mobility are studied. Eventually, the calculated mobility for truncated
Modeling of Soft Pneumatic Actuators with Different Orientation Angles Using Echo State Networks for Irregular Time Series Data
Modeling of soft robotics systems proves to be an extremely difficult task, due to the large deformation of the soft materials used to make such robots. Reliable and accurate models are necessary for the control task of these soft robots. In this paper, a data-driven approach using machine learning is presented to model the kinematics of Soft Pneumatic Actuators (SPAs). An Echo State Network (ESN) architecture is used to predict the SPA’s tip position in 3 axes. Initially, data from actual 3D printed SPAs is obtained to build a training dataset for the network. Irregularintervals pressure
Reliability and Security Analysis of an Entanglement-Based QKD Protocol in a Dynamic Ground-to-UAV FSO Communications System
Quantum cryptography is a promising technology that achieves unconditional security, which is essential to a wide range of sensitive applications. In contrast to optical fiber, the free-space optical (FSO) link is efficiently used as a quantum channel without affecting the polarization of transmitted photons. However, the FSO link has several impairments, such as atmospheric turbulence and pointing errors, which affect the performance of the quantum channel. This paper proposes a quantum key distribution (QKD) scheme that uses a time-bin entanglement protocol over the FSO channel that suffers
Current-Mode Multiplier Accumulator Design using a Memristor-Transistor Crossbar Architecture
This paper discusses the implementation of a Multiplier Accumulator (MAC) design using memristor and crossbar architecture. MAC consists of an array of memristors alongside transistors making a cell that works as a switch (i.e., turned ON or OFF). When a cell is selected, it adds the current in the array path, followed by a current mirror circuit amplified to determine the accumulated current. A traditional MAC is also implemented to compare it with the proposed MAC. The proposed MAC consumed power of 3.9μW, while the traditional MAC consumed power of 19μW. The delay of the proposed MAC is 1
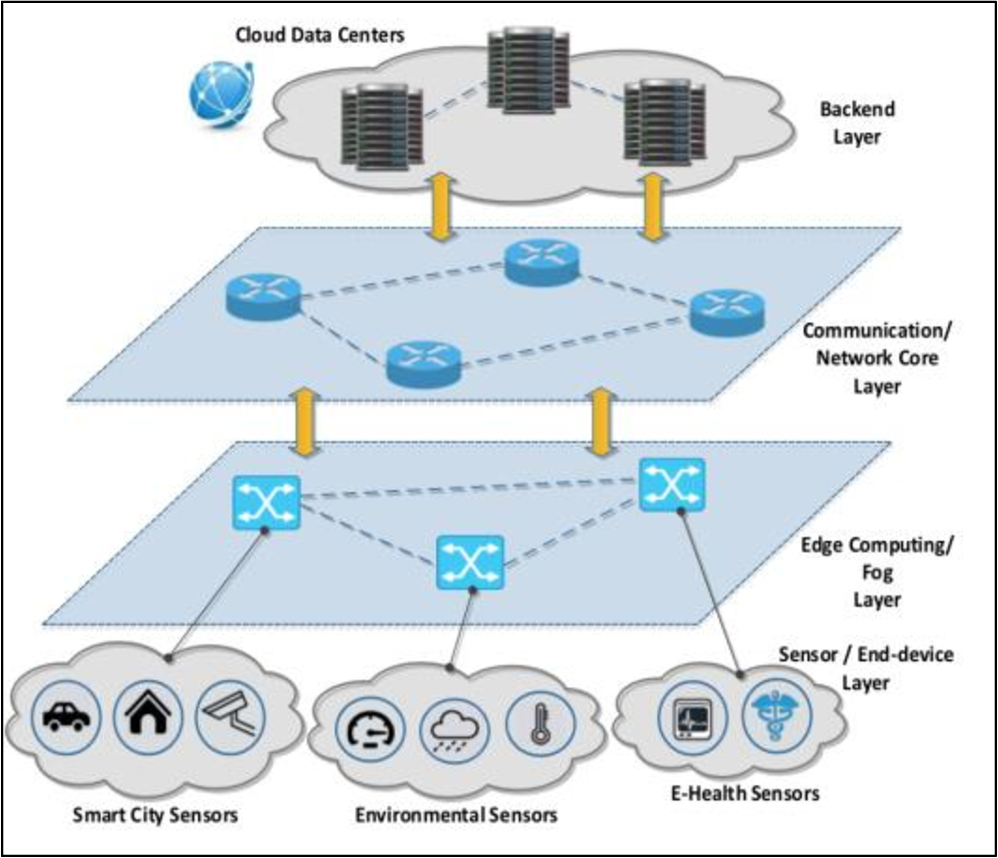
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
Assessing leanness level with demand dynamics in a multi-stage production system
Purpose - The purpose of this paper is to present a dynamic model to measure the degree of system's leanness under dynamic demand conditions using a novel integrated metric. Design/methodology/approach - The multi-stage production system model is based on a system dynamics approach. The leanness level is measured using a new developed integrated metric that combines efficiency,WIP performance as well as service level. The analysis includes design of experiment technique at the initial analysis to examine the most significant parameters impacting the leanness score and then followed by
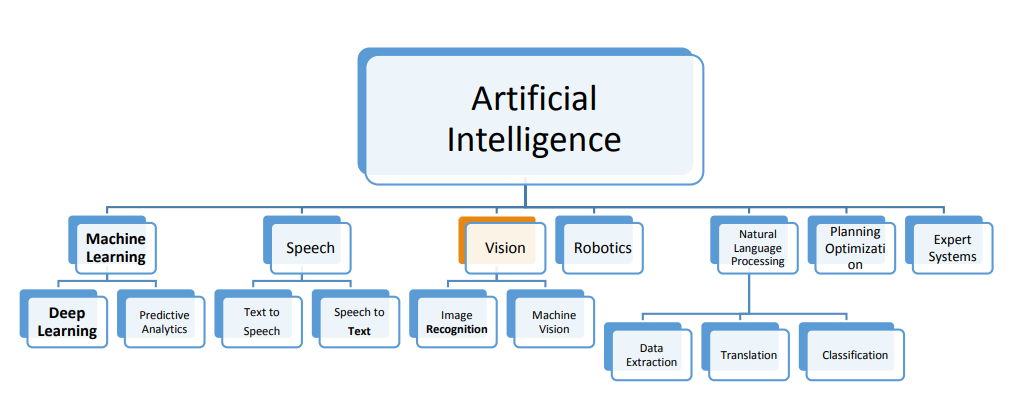
Artificial intelligence for retail industry in Egypt: Challenges and opportunities
In the era of digital transformation, a mass disruption in the global industries have been detected. Big data, the Internet of Things (IoT) and Artificial Intelligence (AI) are just examples of technologies that are holding such digital disruptive power. On the other hand, retailing is a high-intensity competition and disruptive industry driving the global economy and the second largest globally in employment after the agriculture. AI has large potential to contribute to global economic activity and the biggest sector gains would be in retail. AI is the engine that is poised to drive the
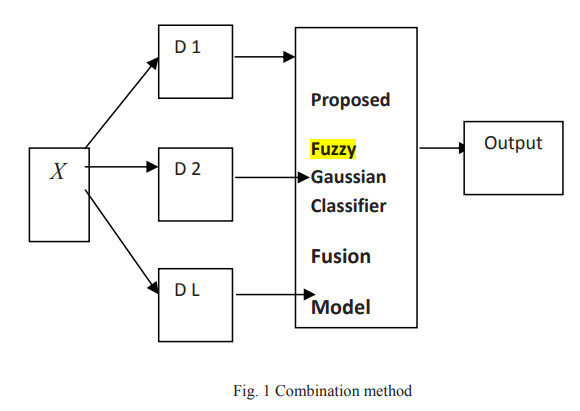
Fuzzy gaussian classifier for combining multiple learners
In the field of pattern recognition multiple classifier systems based on the combination of outputs from different classifiers have been proposed as a method of high performance classification systems. The objective of this work is to develop a fuzzy Gaussian classifier for combining multiple learners, we use a fuzzy Gaussian model to combine the outputs obtained from K-nearest neighbor classifier (KNN), Fuzzy K-nearest neighbor classifier and Multi-layer Perceptron (MLP) and then compare the results with Fuzzy Integral, Decision Templates, Weighted Majority, Majority Naïve Bayes, Maximum
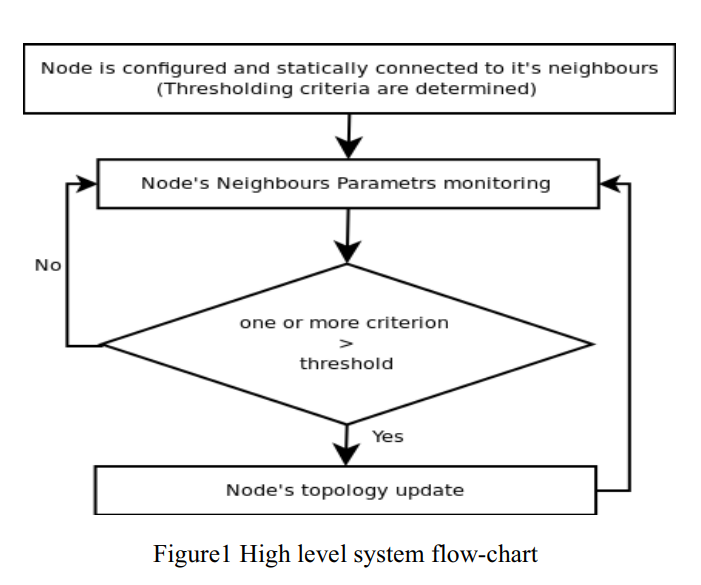
Janitor, certificate and jury (JCJ): Trust scheme for wireless ad-hoc networks
Ad hoc networks are peer mobile nodes that self configure to form a network. In these types of networks there is no routing infrastructure, and usually nodes have limited resources. This imposes a serious problem due to some nodes' selfishness and willingness to preserve their resources. Many approaches have been proposed to deal with this problem and mitigate the selfishness; amongst these approaches are reputation systems. This paper proposes a reputation system scheme that helps isolating misbehaving nodes and decreasing their ability to launch an attack on the network. The idea of this
Pagination
- Previous page ‹‹
- Page 4
- Next page ››
